New wave of Mal-Spam campaign attaching Disk Imaging Files

From past few months at Quick-Heal Labs, we have been observing a sudden rise in Spear Phishing mail containing distinct file formats as attachment like IMG, ISO, etc. These new types of attachments are mainly used to deploy some well-known and older Remote Access Trojans. The subject of these emails are made to appear as genuine as possible in the form of ‘Case file against your company’ or ‘AWB DHL SHIPMENT NOTICE AGAIN’ etc. The attached files contain compressed malware (RAT’s) which have many different names like ‘Court Order.img’, ‘Product Order.img’, etc. The below image displays one such spear phishing mail.
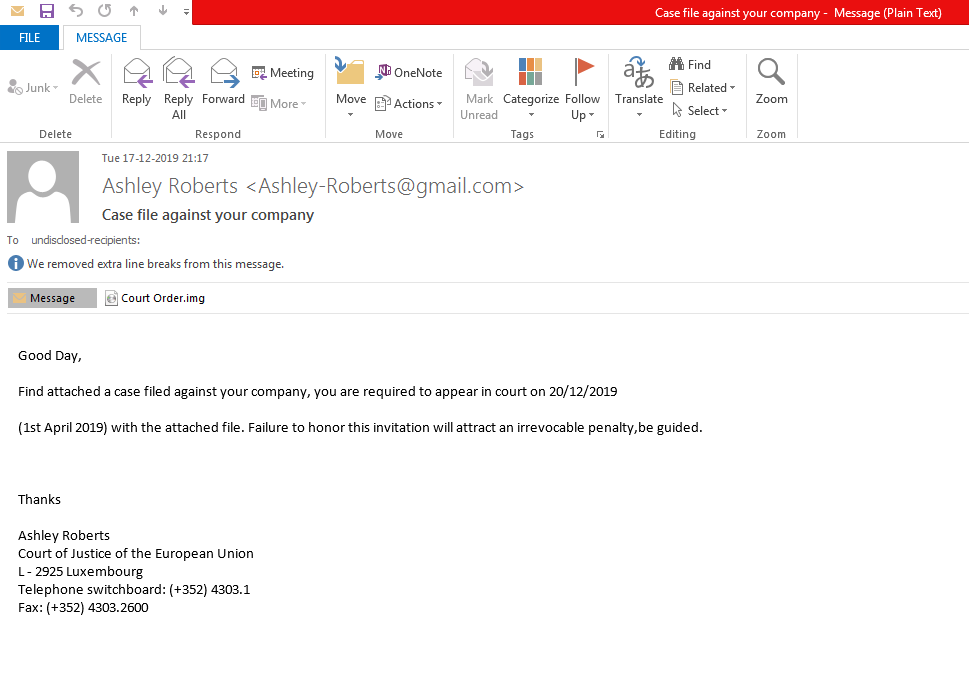
Figure 1: Spear phishing mail with malicious attachment of type IMG
Below fig. shows that common compression file formats like RAR, ZIP and GZ are used most widely for spear phishing emails. We can also see that disk imaging file format like ISO and IMG are also being used for spear phishing and deployment of malware to some extent.
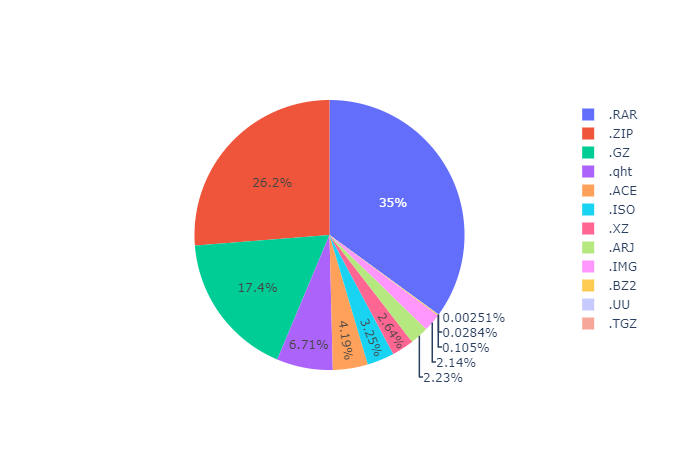
Figure 2: Distribution of various compressed file formats in Phishing Mails
The below graph shows that the number of IMG and ISO files used to deploy RAT’s is growing rapidly from November 2019. Before November 2019, the count of IMG and ISO files combined was negligible.
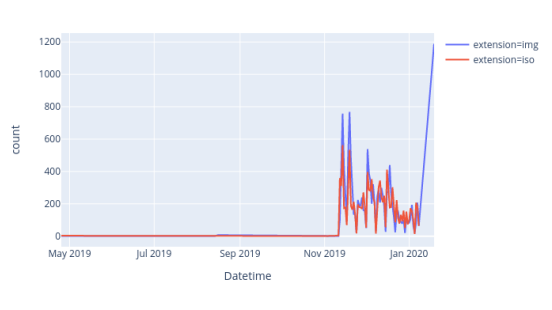
Figure 3: Rise of IMG and ISO Files used in Spear Phishing Emails
On windows 8 and above, user can directly open these files like ISO, IMG in explorer by just double clicking it. For older versions of windows, users have to mount or extract these files and then use. This might be the reason for high amount of spear phishing emails using disk imaging format.
The below image shows the widespread distribution of spear phishing emails over past 6 months, with .ISO and .IMG extension of attachment indicated with red dots in different countries.
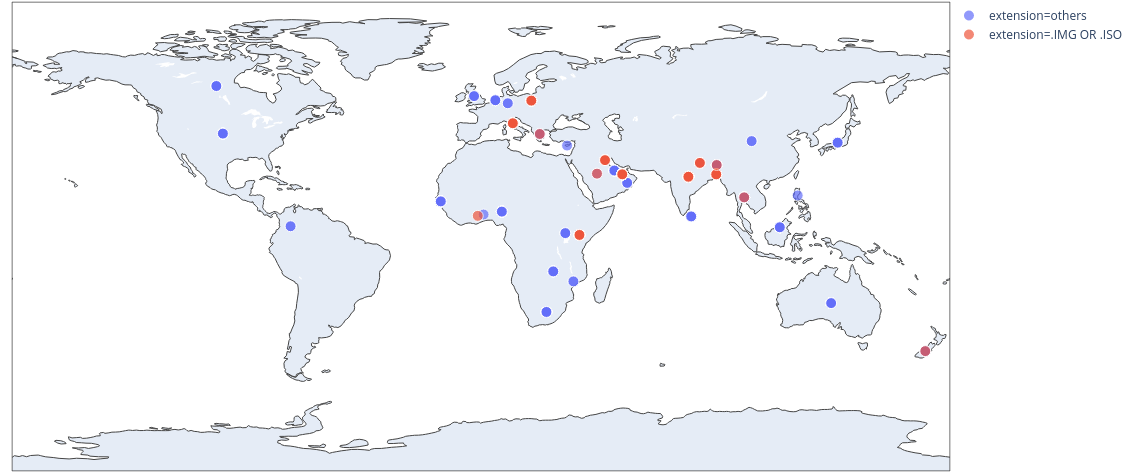
Figure 4: Country wise distribution of attachment types used in Spear Phishing Mails.
We specifically observed Nanobot, Remcos and Lokibot spreading through use of disk imaging formats. These malware are observed all over the globe with Nanobot having the highest hits for spear phishing mails.
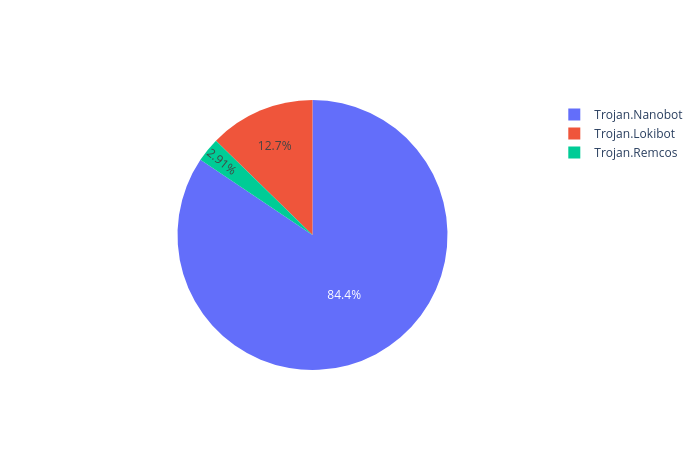
Figure 5: Comparison of Number of Spear Phishing attempts
Infection Chain:
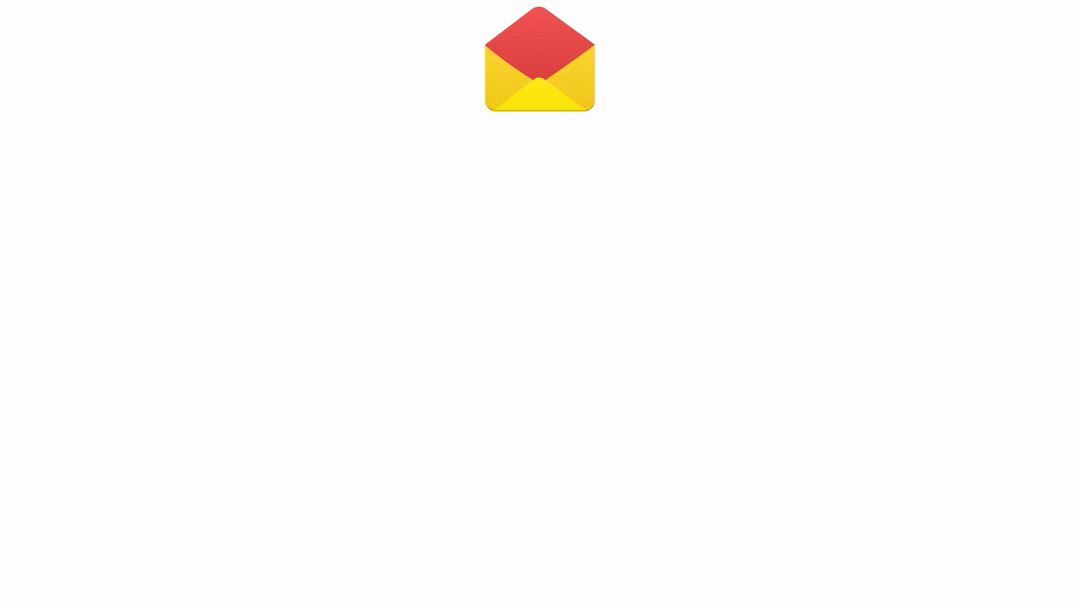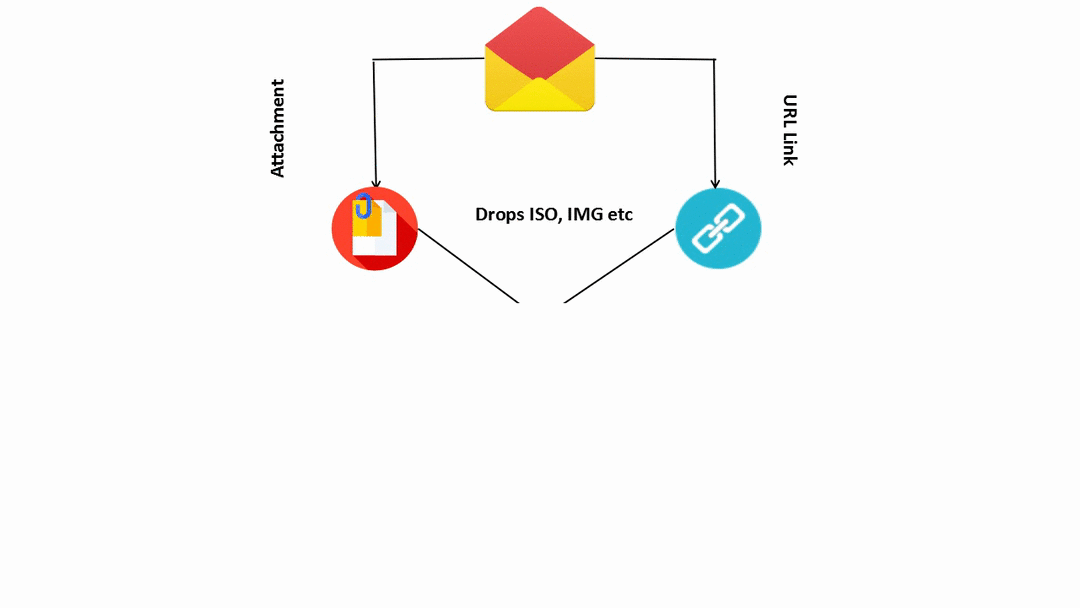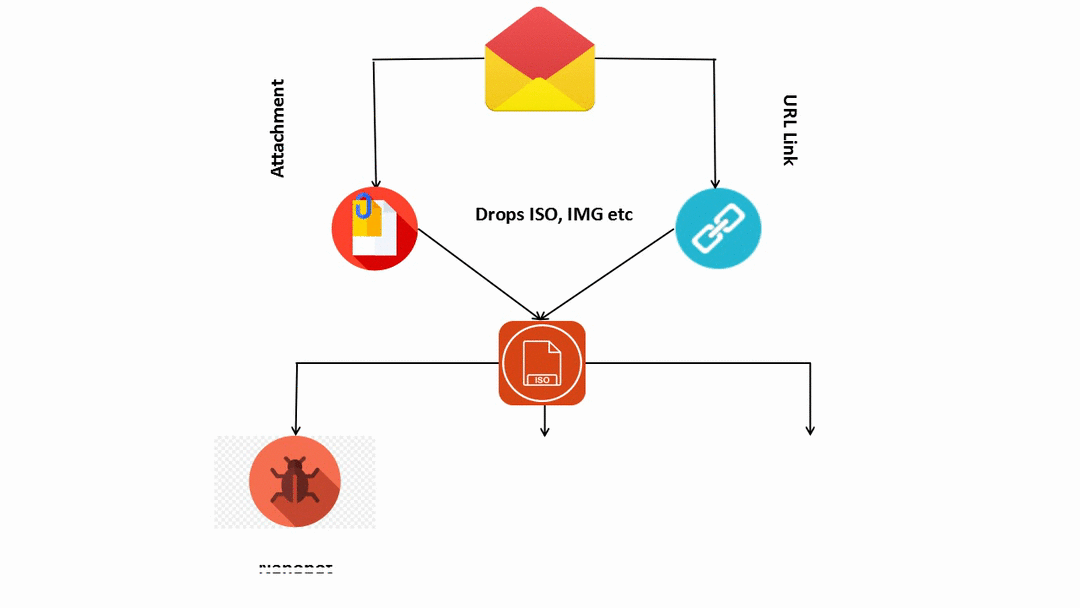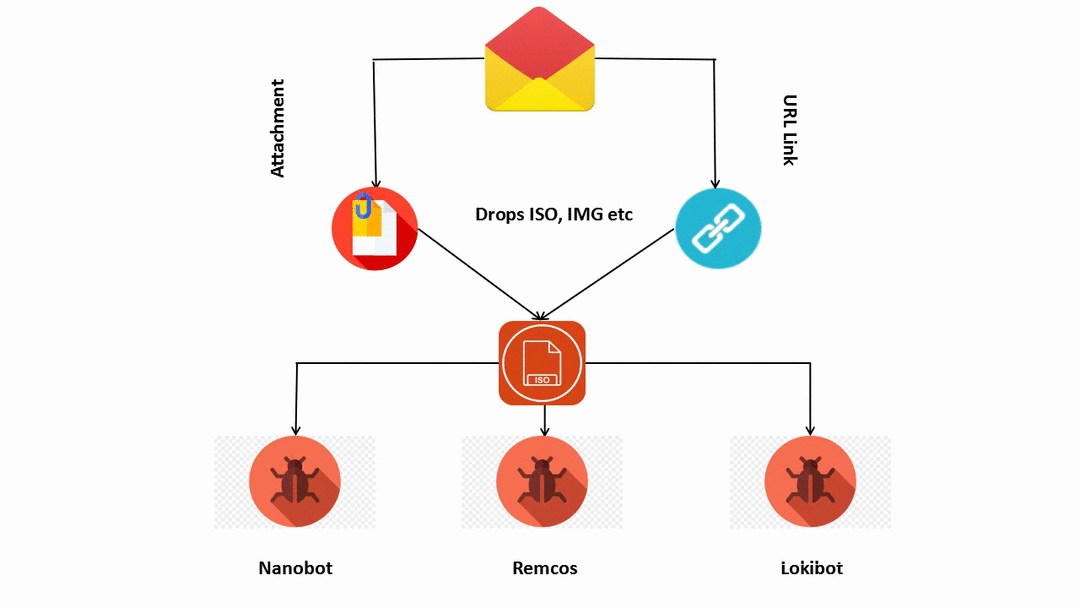
Figure 6: Flow of Infection
Now let’s see each of these one by one i.e.Nanobot, Lokibot and Remcos. As these malware are widespread and already known, we will only take a short look into them.
Nanobot:
The attached iso or img file contains a windows executable file which works as a loader for nanobot, remcos or lokibot. Below fig shows mounted ISO image with just double click on attachment.
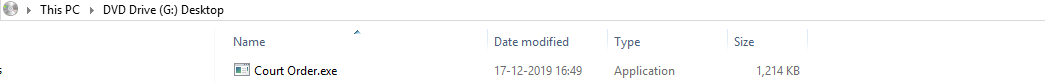
Figure 7: Mounted ISO file.
This executable is a compiled AUTOIT script. It creates a new Process ‘Regasm.exe’ and injects the main payload into it. The injected payload is a .Net executable file obfuscated with eazfuscator, and turns out to be a Nanocore client.
Figure 8: Spawned Regasm.exe
This particular sample that we analyzed is of Nanocore client of version 1.2.2.0 as shown in below fig.
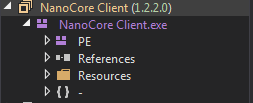
Figure 9: Nanocore Client
Nanocore client’s configuration and plugins are encrypted and present in the resources. At run-time it decrypts its configuration which contains multiple configurable options like Keyboard Logging, which can be set to true or false, bypassing UAC control, Run On Startup and various other configurable options for CNC communication.
Figure 10: Nanocore Configuration
Capabilities of NanoCore:
- Keyboard Logging
- Bypass UAC
- Multiple Plugins e.g:
- Surveillance Plugin: Microphone and Webcam access.
- Management Plugin: Remote Console, Registry Editor etc.
Remcos:
The process for dropping Remcos is similar to that of Nanobot in above case. This executable is also a compiled AUTOIT Script, which creates ‘RegSvcs.exe’ and injects a PE into it which is Remcos RAT.
Figure 11: Spawned RegSvcs.exe
It makes use of mutex to confirm only one instance of malware running on infected system. Below image shows name of malware used as part of mutex name.
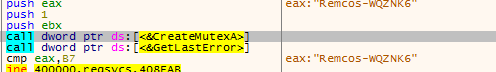
Figure 12: Mutex Creation
Remcos decrypts it’s settings from resource ‘SETTING’ present in its binary which is encrypted using RC4 algorithm.
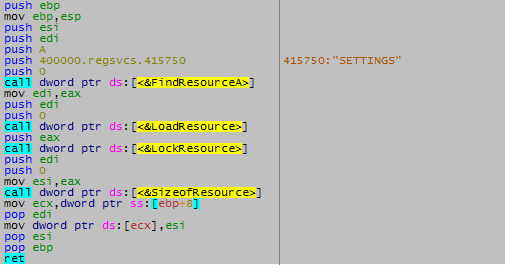
Figure 13: Reading of ‘SETTINGS’ Resource
After decryption of loaded resource called ‘SETTINGS’, below settings are generated for Remcos.
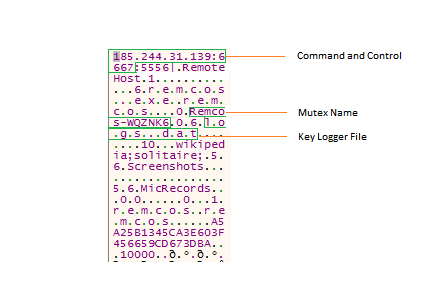
Figure 14: Decrypted Resource Settings
Capabilities of Remcos:
- Key-logging
- Get system clipboard data
- Voice Recording
- Enable Camera
Lokibot:
This is somewhat different from the above two, as it drops a Visual Basic Native Compiled executable which is a variant of Lokibot RAT.
The Lokibot malware reads registry key at present at: ‘HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\MachineGuid’ and computes its md5 hash using cryptography functions provided in advapi32.dll, which is used for creating a mutex. This mutex is used to check if system is already infected or not.
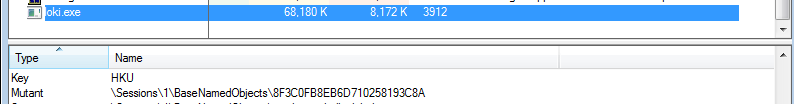
Figure 15: Mutex of Lokibot
‘MachineGuid’ is generated at the time of system installation, which is somewhat unique to the system configuration. Further this md5 hash of ‘MachineGuid’ is also used for creating a folder in %appdata% and dropping a self-copy and hdb file. The dropped self-copy’s names characters are from the md5 of ‘MachineGuid’ from characters 13 to 18, and folder name characters are from the md5 of ‘MachineGuid’ from characters 8 to 13. The hdb file generated is specific to lokibot which it uses for storing the hash of stolen data.
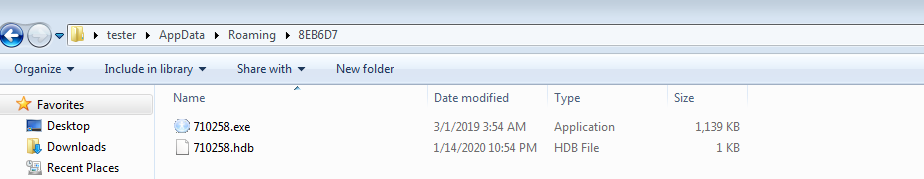
Figure 16: Dropped Files by Lokibot
Capabilities of Lokibot:
- Stealing Password from browsers like Firefox, Chrome, Opera etc.
- Stealing Configuration from browsers.
- Stealing Password from Microsoft Windows Credential Manager.
Indicators of Compromise:
| MD5 | Name | Malware |
| 795B0F5D8425DB2BBA02A7663A74447A | Purchase Order_raw_material_2019_20_05.iso | Remcos Wrapper |
| 36E49FCD84AAFCC6F02238A304A40A09 | Purchase Order_raw_material_2.exe | Remcos |
| 5BFF53521C7FB38970D09B7CD82DFCCB | DHL.iso | Nanocore Wrapper |
| B7C30DB2287179BBA2D007EC615ABCE4 | New nao.exe | Nanocore |
| 7129f51a9e66b98f0b240b62451da860 | nonfragilely6 | Lokibot |
Few interesting file names of attached files in email to watch out for:
- ‘Income Tax Payment Receipt’
- ‘IncomeTax Online Challan’
- ‘Citi Bank Payment-Advice-PDF’
- ‘DHL SHIPMENT NOTIFICATION_PDF’
- ‘FedEx Parcel’
Conclusion:
With invent of new features in Windows, threat actors also keep finding ways to abuse those features. Here, we have seen this in how disk imaging formats are being used to deploy RAT’s. In future, these formats may also be used to deploy other kinds of malware, as threat actors are adept at abusing the features present in Windows itself.
How to stay safe:
Spam mail has been one of the most common Infection Vectors for various kinds of malware. Many people fall in such trap of phishing mails as it is socially engineered by the threat actors.
Quick Heal provides protection against these threats. Users should take the below steps as security measures.
- Turn on email protection of your antivirus product.
- Do not open any link in the email body sent by an unknown source.
- Do not download and open any attachments from an unknown source.
Subject Matter Expert:
Prakash Galande, Rahul Sharma, Akshay Gaikwad
No Comments, Be The First!