When it comes to desktop computers, people go for the best security software. But when the talk is…
Archives by Date
Cryptocurrency mining rampage throttles Linux machines – an analysis by Quick Heal Security Labs
Quick Heal Security Labs recently came across a Linux-based Monero (XMR) miner. Monero (XMR) is one of the…
CVE-2018-4990 – Adobe Reader Double Free (Zero Day) vulnerability alert!
The recent zero-day vulnerability CVE-2018-4990 in Adobe Reader enables attackers to perform a Remote Code Execution on targeted…
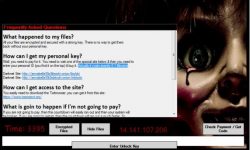
Breed of MBR Infecting Ransomware – an analysis by Quick Heal Security Labs
Ransomware is becoming one of the most perilous cyberattack methods and also the most habitual techniques for cybercriminals…
3 reasons you can’t live without your smartphone [VIDEO]
Can you think of 3 reasons why you can’t live without your smartphone? Well, we tried figuring out…
CVE-2018-8174: Windows VBScript Engine Remote Code Execution Vulnerability – An advisory by Quick Heal Security Labs
The recent zero-day vulnerability in Windows VBScript Engine (CVE-2018-8174), enables attackers to perform a remote code execution on targeted machines….
Twitter bug attack: All you need to know & ways to fight such attacks
One company with a turnover of $2.44bn 330 million users 500 million tweets per day What does it…
Quick Heal supports the Windows 10 April 2018 Update
As part of the Windows 10 Updates, Microsoft has now come up with a new update for Windows…
Got a new Android phone this summer? Here are 6 tips to take good care of it!
Planning to get a new Android phone, or already got one recently? Then you must totally follow these…
An analysis of the Dharma ransomware outbreak by Quick Heal Security Labs
On April 25, 2018, Quick Heal Security Labs issued an advisory on a new ransomware outbreak. We are…