Potentially Unwanted Applications (PUAs) in Disguise of Software Updates

It has been observed that cyber criminals are using genuine names to enter into their targeted victim’s system. They are doing this by displaying random pop-up ads on Internet Explorer, Firefox, or Google Chrome that prompts the user to update Adobe Flash Player, Java, media players, etc. These pop-up ads are not from the developers of Adobe Flash Player or Java, but are used by cyber criminals to infect the victim’s computer with adware and browser hijackers.
This report presents an insight into how cyber criminals are using pop-up ads to trick users into downloading malicious software. For instance, you unknowingly visit a website with a bad reputation. You get a pop-up prompting you to update your Flash Player, even when the software is already up-to-date. If you click on this pop-up, it will download a malicious file on your computer which will further download potentially unwanted applications.
Upon analysis, we found that many of such downloaders that were downloading other PUAs belonged to the family called InstallCore.
What is InstallCore?
InstallCore is an installation and content distribution platform including an SDK (Software Development Kit) for Windows and Mac OS X. Many installers using this platform have been rated as adware and Potentially Unwanted Applications (PUAs).
We have received some InstallCore samples having genuine application names. They are as follows:
- adobe_flash_setup.exe
- JavaSetup.exe
- google-chrome.exe
- VLCPlayerSetup.exe
- FirefoxSetup.exe
These fake versions are usually found on websites that offer free music, videos, software, etc., and they redirect users to other unwanted sites. Here are a few examples:
h[t]tp://adobe-flash-player.soft112.com/download.html redirects to
h[t]tp://softwaresw177squared.xyz/3661/lp3/85529/362/79
h[t]tps://firefox.jaleco.com/ redirects to
h[t]tps://firefox.jaleco.com/download
h[t]tps://2acd-downloads.phpnuke.org/en/c53868/vlc-media-player redirects to
h[t]tp://telecharger.benjaminstrahs.com/en/download-version/-z-m-v-m-m-m-x
These downloaders were found to download other malicious applications like Palikan, PriceFountain, Search Offer, Zensearch, etc.
Quick Heal detects these malicious InstallCore samples as Adware.InstallCore.A8. It modifies default search engine, new tab, and homepage settings of the web browser or seeks out personal information stored on the infected computer’s hard drive and uses it to steal the victim’s identity.
We have demonstrated this with the following scenario:
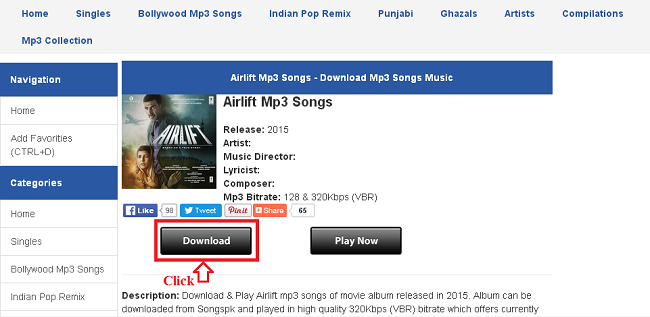
We want to download a song and we use our favorite search engine to search for websites that offer free music. When we visit such a website, we search for the desired album. A page similar to the following appears.
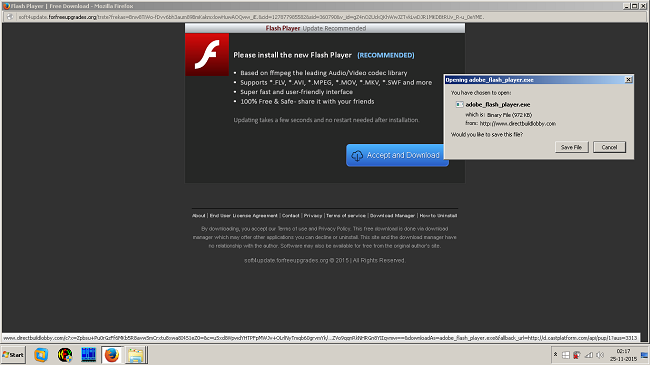
When we click on the download button, we are redirected to a page that informs us that our Flash Player is out-of-date and that we need to download an update.
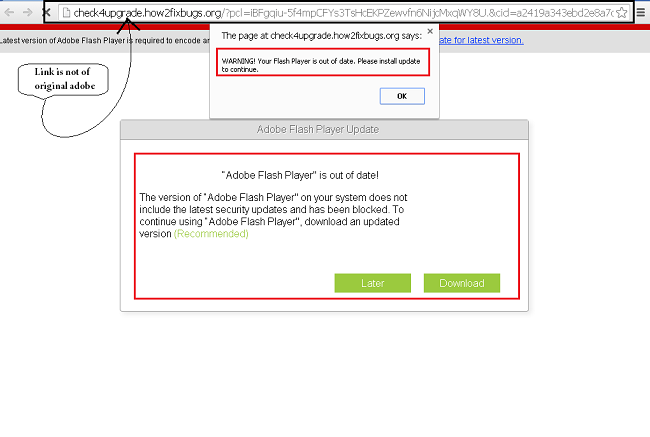
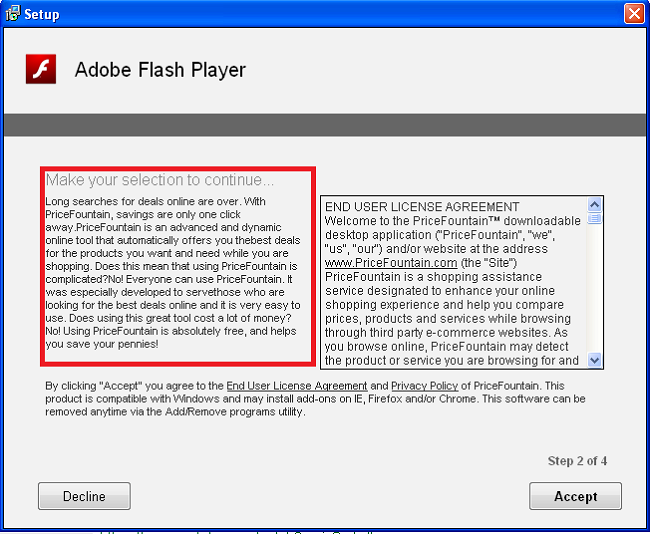
Let us see a few examples of what a fake installer of Flash Player looks like:
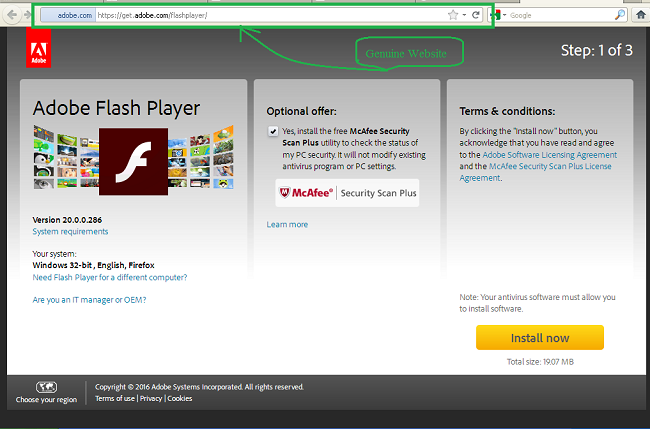
The above Figure 03 shows a fake Adobe page, whereas, a genuine website of Flash Player by Adobe looks as shown in Figure 04 below.
The genuine update for Flash Player is available at the company’s website which is:
https://get.adobe.com/flashplayer/, whereas the fake ones could be different. Also note that, fake websites do not have “HTTPS” (secured connection) in their URL while genuine ones do.
Different malicious publishers
Our research helped us find different variants of fake Flash Player setups like the ones mentioned above. We found that all of these were signed with different publishers viz. OOO Advert M, OOO KOD 7 and OOO ELEKTRO-KODTo. The genuine publisher, in this case, is ‘Adobe Systems Incorporated’ which is easy to identify. To view a publisher’s details, right-click on the setup file and click on the ‘Digital Signatures’ tab.
Dynamic Analysis
On execution of the fake Flash Setup, it offers us a variety of other freeware, whose installation check box is already ticked (shown below). The idea behind this is to trick users to install bundled software with the installation.
A few examples of the freeware offered to us are as follows:
Palikan
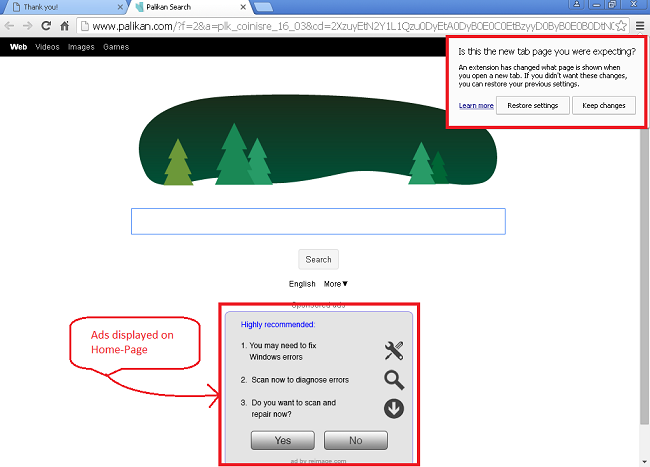
Palikan.com is a browser-hijacking application that employs a deceptive software marketing method called ‘bundling’ to install on Internet browsers. This app infiltrates Internet Explorer, Google Chrome, and Firefox browsers, modifying the new tab URL, homepage, and default search engine settings by assigning them to palikan.com. The new home page displays rogueware ads that download other PUAs.
PriceFountain
PriceFountain is advertised as a program that displays coupons for websites you are visiting and competitive prices when you are viewing product pages on popular online shopping websites. While this may sound like a useful service, the PriceFountain program can be intrusive and will display unwanted ads.
Search Offer
Search Offer installs Chromium browser, makes Yahoo as the default search engine, new tab and homepage on Internet Explorer, Firefox and Chrome browser.
Observations
In each installation, we are offered different software. In this process, we are not asked to tick the check boxes as they are selected by default. Even if we decline a few installations, we are shown another window with other software. These kind of continuous prompts make the user somehow accept all conditions and proceed with the installation.
All the free software offered are not related to Flash updates and not even necessary for the user. One can simply call them “Unwanted”. Once installed, such software pose a great threat to the performance of your computer and the information it contains. Several adware programs will interrupt activity by displaying constant pop-up windows, whether you are online or not. You may find that your web browser has been hijacked, perhaps replaced with offensive content and/or is riddled with unwanted ads. When typing into a search engine, your web requests may get redirected to other Internet locations. It may also modify default search engine, new tab and homepage settings of the browser.
Here are some changes that were observed in the browser after installing fake flash update:
We see that our initially blank home page is set to Palikan’s website. This site shows rogueware ads that would install other PUAs. While browsing on Amazon.com, we found that whenever we open any product window, the page is injected with an ad showing us the price comparison of similar products from other shopping sites such as Paytm, Snapdeal, etc.
Preventive measures to take
- Download content only from genuine websites.
- Never run an executable which seems to be suspicious. For instance, if you are downloading an episode of Game of Thrones, do not run any file named “GameOfThronesS01E01.exe.”
- Always opt for custom installation and unselect anything that is not familiar, especially optional software that you never wanted to download and install in the first place.
- Read the ‘Privacy Policies’ and ‘License Agreements’ of all software before installing them.
- Always keep browsers and other software up-to-date.
- Antivirus products can help track and detect such malicious activities. Make sure your antivirus is always up-to-date.
ACKNOWLEDGEMENT
Subject Matter Experts:
- Sarju Patil
- Pooja Panchakshari
– Threat Research and Response Team, Quick Heal
No Comments, Be The First!