Password Security: A dash of ‘salt’ and little of ‘hash’ to go please!
 Online services like LinkedIn, eHarmony and Last.fm were recently hacked and millions of passwords were found on Russian hacker forums. This has led to a rise in public awareness about password securing procedures like ‘salting’ and ‘hashing’.
Online services like LinkedIn, eHarmony and Last.fm were recently hacked and millions of passwords were found on Russian hacker forums. This has led to a rise in public awareness about password securing procedures like ‘salting’ and ‘hashing’.
Quick Heal users are protected from various real-time risks but attacks like this show that web services need to do more to secure passwords and data. Most services hash these passwords instead of storing them in plain text, but this is not enough. The data needs to be salted as well. Let’s see what these terms mean.
What is hashing?
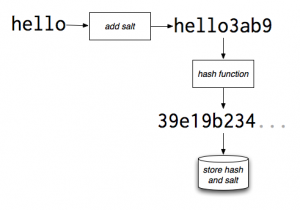
A hash is a one-way coding function used to organize and randomize large data sets. In terms of security, each password is a data unit. When a password is entered into the database, it is hashed according to a certain code. So a password like ‘123456’ becomes something like ‘0xgh56ju7h4i8’ (This is just an example). Common programs used for this purpose are MD5, SHA-1, SHA-256, SHA-384, SHA-512 etc.
What is salting?
The encryption of a data set with the help of a key is known as salting. The data cannot be viewed without the help of the key. Once a data set has been salted, it becomes very hard to crack and trace. Typically, a salt is a string that is attached to a password before it is cryptographically hashed. For instance, ‘123456’ becomes ‘123456xe6i9o56jh09’ after salting. This new value then becomes ‘0cn1b45wq6k0y2’ once it has been hashed.
Ideally, the salt factor should be unique for each data unit before it is hashed. If the same salt is used for each password, it is easier for an attacker once he cracks the salt. Additionally, a salt should not be too short in length. If two or more salts are the same, an attacker can identify similar passwords. These passwords will then be targeted with greater frequency. Adding a salt in itself does not make hacking harder. Instead, it makes the procedure longer. This is something that has left many attackers discouraged and uninterested so it is a necessary step.
Potential threats
Common sources of danger with regards to salting and hashing are as follows:
- Rainbow table: This is a list of breached hashes and passwords based on specific scrambling programs. These tables are created, updated and shared by hackers over public forums.
- Dictionary attack: Under this form of attack every word from a dictionary is run against a set of hashed passwords in order to crack the code.
- Brute-force attack: This is a dictionary attack on a larger scale. Characters and numbers are also added to words from the dictionary.
Commonly used scrambling programs are easier to crack since hackers have shared their resources over the years. Hence, it is advisable for web services to create their own scrambling tools as this makes the procedure longer and harder. Nevertheless, hacking incidents like the recently reported ones do occur from time to time.

7 Comments
Hmmmmm…!!!
Fantastic info and also nice explanation of the techniques too…!!
As per your comment”Commonly used scrambling programs are easier to crack since hackers have shared their resources over the years. ”
but the webservices…means they are not using their Self-developed scrambler`s is it sooo??
Thanks Sameer. The most popular web services do use their scrambler, but unfortunately when someone lapses, such instances occur.
give me product key
Hi Ajay,
Please send an email to support@quickheal.com for your product key. They will provide you with the necessary information.
Thank you.
thanks for latest information
I have lost my password numbers.please give me my password number
Hi Mahanta,
Can you specify which password you are looking for? You can also contact our technical support team for assistance with this – https://www.quickheal.co.in/submitticket.
Regards.