New Android Malware known as Android.AVPasser.A Detected
A new variation of mobile malware that affects Android based devices has been detected by the Quick Heal Labs. An innovative feature of this malware is that it detects certain mobile security applications on the device and modifies their databases in order to avoid detection.
Quick Heal Detection: Android.AVPasser.A
As all other forms of Android malware, this variant too has the capability to modify certain system files and steal private data and information, and then broadcast the same to remote servers.
Dynamic Analysis of the Malware
Once the Android.AVPasser.A malware enters an Android device, it creates multiple icons in the Application Tray of the device. The screenshots below show the icons that are created by the malware.
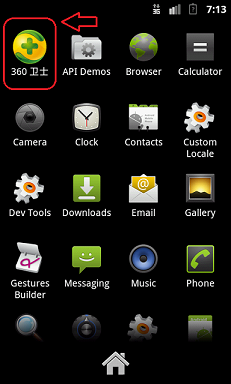
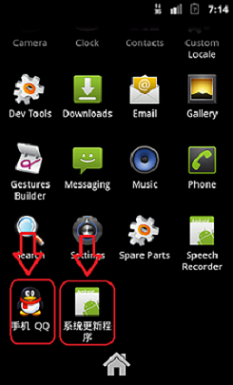
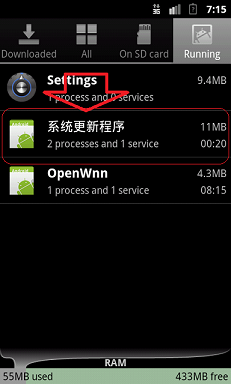
If the user clicks on any of these icon shortcuts, the icons vanish from the Application Tray. However, upon viewing the Active Applications window one can still see the SystemService.class running in the background. This can be viewed in the screenshot below.
What this Malware Does
Upon installation, this malware has the capability of stealing the following data from the compromised device:
- Photos
- SMS messages
- Contacts
- Call history
- Videos recorded by the front and rear cameras
- GPS location and history of the device
- Device specific data such as:
- Build version
- Device ID
- IMEI (International Mobile Station Equipment Identity)
- IMSI (International Mobile Subscriber Identity)
- MDN (Mobile Directory Number)
- Additionally, the application also gains control over the network activity and visits a malicious URL as shown below:
Other Activities by the Malware:
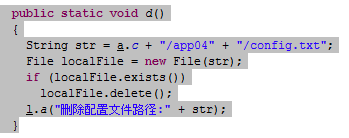
#1 Once it enters an Android device, the malware checks for the existence of a config.txt file at a preset location on the device. If found, the malware deletes the file and creates a malicious file of its own.
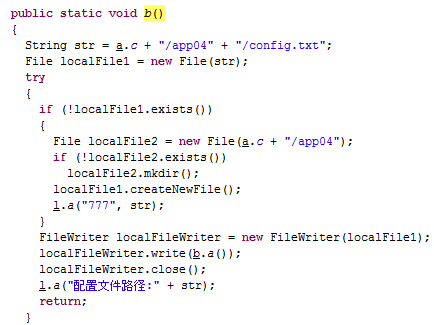
#2 The malware broadcasts the information that it collects in the following conditions:
- When any SMS is received by the device
- When any media connection is mounted or unmounted
- When the device screen goes ON or OFF
#3 The malware calls CameraPicService from the SystemService.class and then runs a thread at an interval of 2 minutes to check the number of cameras connected to the device.
#4 Lastly, the malware collects and analyzes all the packages that are installed on the compromised device and matches them to see if any of them is a mobile security application. Once an application is confirmed to be a mobile security application, the malware modifies the database of the security application in order to to avoid detection.
Quick Heal Total Security for Android and Quick Heal Mobile Security actively provides Android malware detection and Android malware removal as soon as this malware enters the device. We strongly recommend that you install the latest updated versions of either of these applications to ensure protection against this malware and other related threats.

4 Comments
Dear Quick Heal Engineers,
On my Desktop I have QHIS protection installed since 2013 even then I feel my desktop is being controlled by some external entity through such a Malware Software. But there is no such error reported on my desktop by QHIS. Could you kindly look into it, if required do visit my office to personally see the things that are happening automatically on my computer and QHIS mentions “Everything is Alright” i.e. no virus found after full scan.
With regards,
Hari Haswani (Tel. no. 020-26685347)
Hi Hari,
Request you to contact our support team so that they can analyze the situation better. Please contact them at 0-927-22-33-000.
You can also raise a query at https://www.quickheal.com/submitticket.asp.
Regards,
Recently quickheal detected android.airpush.g(adware )
in my mobile.before detection I noticed extremely slow keypad response,
Repeated calls on just received calls specially when headphones were plugged.
Can anybody tell me.whether my Whtsapp pics were stolen or not.
Hi Abhi,
Request you to kindly contact our support team at 0-927-22-33-000.
You can also raise a query at https://www.quickheal.com/submitticket.asp. Our support team will get back to you to resolve the issue you are facing.
Regards,