‘Flamer’ Lights Fire In Cyber Space
We would like to update our readers about the findings of Flamer, the recent information stealing malware which is making news in Cyber Space.
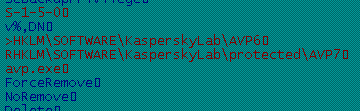
Investigation shows that a few of the malicious Flamer components were reported in the Online Scanner portal around 2 years and 10 months ago (in August 2009). Shown below are the partial list strings that Flamer uses to identify and terminate security products.
The strings ‘KasperskyLabAVP6’ and ‘KasperskyLabprotectedAVP7’ give clues about the time period during which Flamer might have been developed. These particular security products were released in 2008 and 2009 respectively. This pretty much indicates that the development of this malware might have happened between the end of 2008 and early 2009.
Flamer has various similarities like the use of Print Spooler and LNK vulnerability as propagation vector and tilded naming convention for some of its files with Stuxnet/Duqu. However, it differs in its implementations since it uses Lua Programming Language – a powerful, fast, lightweight and embeddable scripting language. Lua implementation must have had its advantages in the development process as it comes with a lot of packages (https://github.com/LuaDist/Repository) for network programming, compression libraries and database programming which all help in quick prototyping.
The use of key logging, screenshot taking, network sniffing, USB infecting, Autorun.inf infection, sending information for its C&C servers, component based architecture, self-updating mechanism and encryption/compression methods with sophisticated file formats is not unseen in recent malware. What differentiates Flamer is the use of a SQLite database to store lots of information, microphone recordings, Bluetooth functionality etc.
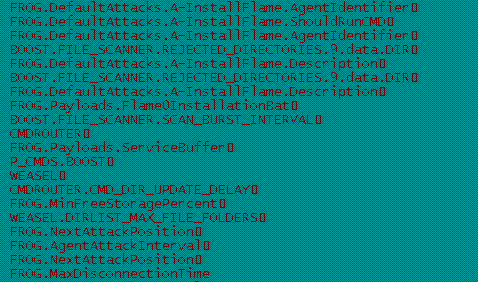
Flamer also has different modules that focus on:
– Selecting specific files from the victim’s computer
– Keeping a list of rejected directories
– Compressing files in storage
– Splitting data into parts before sending
– Prioritizing data which is to be sent
– Limiting how much data is to be sent
– Retransmitting in case of failures
– Monitoring computer performance without arousing suspicions
In the case of targeted attacks, these are important features as each successful exploitation is very valuable to the attacker. Flamer has the functionality to run these commands on a weekly and monthly basis. The total number of reported infections are below 500 at present as it specifically targets Government organizations from the Middle East. It has kept a low profile and has not surfaced on the radar of Security companies and this is why it was not detected for more than 3 years.
Questions about how the attack was carried out and what information was gathered still remain unanswered. The investigation into these questions is ongoing.
There is a possibility that similarly unexplored ‘flames’ are burning in the fields, not just in the Middle East!
Quick Heal users are protected against this Cyber espionage and it is detected as Trojan.Flamer.A.
4 Comments
I have two questions :
Is the code acquired from the executable files through the process called ‘Reverse Engineering’?
Does Quick Heal detect ALL variants (if any) of FLAME?
Hi Priyank Gupta,
Quick Heal detects the Flamer trojan on your system. If there are any subsequent variants discovered, you will be protected against them as well. You can send an email to info@quickheal.com with further questions, if any. Thank you.
Well Trojan.Flamer.A is considered to be a lethal cyberweapon-2012,
But Im quite sure,there will be solutions.
Refering the quick heal,I find it to be most effecient anti-viruses ever used.
Yes its an Indian Product So,I feel proud using it…