While everyone was engaged in new year celebrations, malware authors were busy creating new ransomware for 2019. Quick…
Phishing
Malspam email – Jack of all malware, master of none.
Malspam email or malicious spam emails are considered to be one of the favorite malware delivery channels for…
Beware! Your website might be delivering Emotet malware
In 2018, we saw a surge in Emotet activity. Emotet started as a banking trojan but this blog…
Sophisticated Ransomware : “Katyusha”
For several months, Quick Heal Security Labs has been observing an increase in ransomware, we have found one more…
Obfuscated Equation Editor Exploit (CVE-2017-11882) spreading Hawkeye Keylogger
Cyber-attacks through phishing emails are increasing and generally, attackers use DOC embedded macros to infiltrate victim’s machine. Recently…
How to differentiate between spam and phishing emails?
Emails today have become an integral part of our day-to-day life and this has made it a child’s…
How can my Facebook account be misused if hacked?
At a time when most of us are living in a virtual world, where we are connected to…
Emerging trend of spreading malware through IQY files
Nowadays attackers are searching for new techniques to spread malware, recently we came across a new emerging way…
Beware of the Armage Ransomware – the File Destroyer!
In July last week, Quick Heal Security Labs detected a new ransomware called Armage. It appends ‘.Armage’ extension…
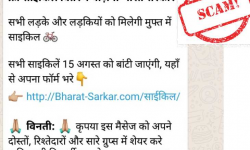
Beware of the ‘Free Cycle Distribution Yojana’ WhatsApp message. It’s fake!
As India’s Independence Day (15th of August) approaches, messages about free distribution schemes are doing the rounds on…