Beware! Hackers target users with fake COVID-19 vaccine registration app
Have you received an SMS with a link that says, “Register for vaccine using COVID-19 app”?
Well, beware! It’s fake – and probably riddled with malware.
The government of India started with the COVID-19 vaccination drive for everyone above 18, but consumers are facing problems in booking a slot due to a shortage in vaccines. In order to make the process user-friendly, several developers came up with notify-me websites that can tell you the availability of the slots, though you still need to use the official registration platform CoWIN API to complete the formalities.
In the middle of such a crisis, hackers are taking advantage of the situation with malicious elements. A fake SMS is in circulation tricking unsuspecting users for vaccine registration via an app. The SMS primarily is a malicious link filled with Android Worm that reaches users via message app, asking to register with the ‘Vaccine Registration’ app. Once the user downloads the app, it requests permission to access all the contacts and messages. The worm then uses the contacts listed in the infected Android device to spread to other devices via text messages.
How does the Trojan malware works?
Fig.1: Malicious web page
The above webpage Fig. 1 shows how hackers misguide users to download an app for the vaccination registration for the 18+ age groups. But in reality, it downloads a malicious APK after clicking on the “Download Now” button. The malicious APK is hosted on the GitHub account, and we got few similar apps with different app name in them. You can find the GitHub account link here. On monitoring this campaign, we got some other GitHub accounts, which also host similar APKs as shown in Fig.2 and Fig.3.
Fig2: GitHub account projectpro1 with malicious APK
Fig3: GitHub account mybestnews with malicious APK
On the first launch, the application takes few suspicious permissions like access contact, send and view SMS, make a call, etc. Fig. 4 shows permissions which it asks for the Fake vaccine registration application.
Fig 4 Fake vaccine registration app.
Technical analysis:
The malware App does some checks shown in Fig. 5 like, Emulator, ADB enabled or not, debugger check. It also collects information on all installed applications on the infected device.
Fig 5: ADB and Debugger check
First, it asks for the mobile number for the registration purpose. But on clicking the register now button, it only checks the length of the entered mobile number. If it is not greater than equal to 4 characters (as shown in Fig. 6) or if it is less than 4 characters, it displays a message “Please Enter your Correct Number!!”
Fig 6: Mobile number check
Spreading through SMS:
The malware collects contact information from the infected device.
Fig 7: Collecting contacts
Malware targets only Jio operators and spreads to contacts who are using Jio sim card. To identify the Jio user, the malware checks the first 4 characters of the mobile number with the list of number that Jio serves. Secondly, it queries a public web API of Jio and checks the response. Below fig. 8 shows the checking of Jio numbers.

Fig 8: Checking the first 4 characters of the number.

Fig 9: checking the response from Web API
The unidentified numbers are checked by querying a public web API of Jio as shown in Fig.9. In response, it checks for the string NOT_SUBSCRIBED_USER. And if the response contains a mobile number, then it is considered as a Jio number. After identifying the Jio number, it collects it in a separate list and starts sending SMS using the default sim operator as shown in Fig. 10.
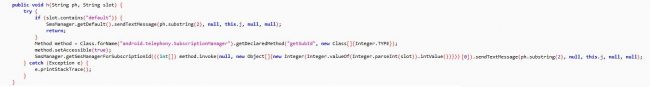
Fig 10: Sending SMS
Spreading through WhatsApp:
The malware does not automatically spread through WhatsApp. It gives a dialogue box of “Share this APP on WhatsApp groups 10 Times to Start Registration” shows in Fig 11.
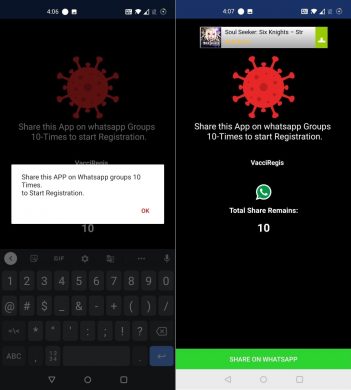
Fig 11: Malware spreading through WhatsApp
On clicking the button “Share on WhatsApp”, the malware copies the message to the clipboard. The malware does not validate whether the message is shared on WhatsApp or not. It only counts the number of clicks on the “Share on WhatsApp”. Fig 12 and Fig. 13 shows the WhatsApp sharing code.
The message shared on the WhatsApp groups:
Register for Vaccine Now*\n*from age 18+*\n\n*No Fees will be taken.*\n*It’s absolutely Free.*\n\n*Download VacciRegis android app*\n*and Register for vaccine*\n*in India*\n\n*Link:* http[:]//tiny.cc/COVID-VACCINE
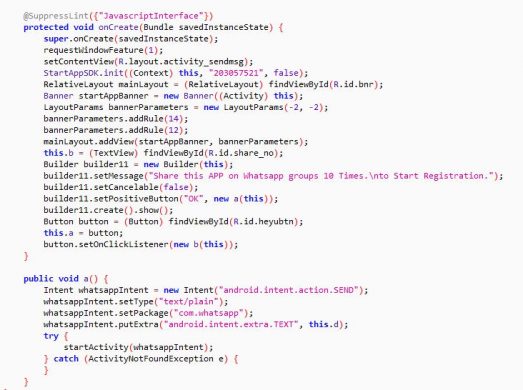
Fig 12: Spreading through WhatsApp
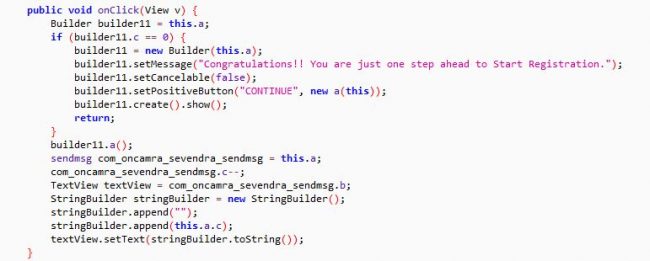
Fig 13: Completion of message sharing on WhatsApp
The main goal of the app is to generate revenue by displaying ads and spreading itself through the victim’s contact list and through SMS. At Quick Heal, we have collected multiple variants of this malicious App and all are detected with the name “Android.GoodNews.GEN41898”. All these malicious applications are signed with the same digital certificate, which means the malware is written by a single malware author.
IOCs
| Package Name | MD5 |
| com.halorozd.meditation | e9eb39d8880a1a04acc538bb717dc337 |
| com.oncamra.sevendra | 36dfa9f4c7cf017b2dcae2b67230245a |
| com.pappucantt.projectdance | 0c926ad8904f1e1d0bccda18f04722da |
| com.oncamra.sevendra | 17e3294f7bfd7e5b1fdb50465471e1db |
| com.projectchav.dudupiva | f570647c6b761aeddf644d46dcb675d9 |
| com.parthhingu.meditation | f504cfe44d9a6a0bfe6c5bf7c29c6a13 |
| com.readyfor.whosbaby | 5c04e41a3d2a00b3c9336788d9ce4835 |
| com.projectchav.dudupiva | 1335d286d70a93cfd888fb3a362ab54e |
| com.projectchav.dudupiva | 8c217585671eec3d7979be4895c3c070 |
| com.rahul.bhuvolund | 1601470a832a633fe3027ef3518bdbfd |
How to stay safe from fake mobile apps
-
- Check an app’s description before you download it from the Google play store.
- Check the app developer’s name and their website. If the name sounds strange or odd, you have all the reasons to suspect it.
- Go through the reviews and ratings of the app. But, note that these can also be faked.
- Avoid downloading apps from third-party app stores.
- Always check your system and applications updated or not.
- Use a reliable mobile antivirus that can prevent fake and malicious apps from getting installed on your phone.
- Use a reliable mobile antivirus like Quick Heal Mobile Security for Android that can prevent fake and malicious apps from getting installed on your phone.
- Don’t click on unknown links shared on social media platforms, even if shared by your trusted contacts.
No Comments, Be The First!