Beware – Banking Trojans Using Enhanced Techniques to Spread Malware.

In our Open-Source Threat Hunting, Quick Heal Security Researchers encountered a banking Trojan named Aberebot capable of stealing sensitive information from infected devices, including financial and personal data.
Malware authors used advanced anti-reverse engineering and obfuscation techniques to avoid detection. From our investigation, the fake malicious application requires some risky permissions, as shown in Fig 01:
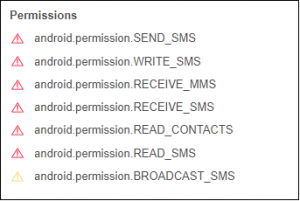
Fig 01. Complex permissions sought by the malware application
The malware has various capabilities, including:
- Collecting contact information.
- Intercepting OTPs from the infected device.
- Managing the list of installed applications from the device.
- Sending SMSs to the contacts based on the commands received from the C2 server.
- Stealing credentials of social media accounts and Banking portals.
- Monitoring the victim device by leveraging the BIND_ACCESSIBILITY_SERVICE.
- Using Telegram API to communicate with the C&C server hosted on a Telegram bot account.
Last month Android security researchers went through one new banking malware named “Escobar.” This malware is the latest variant of the banking Trojans Aberebot. This malware came with some new features in its new avatar, but it is not using Telegram for c2 communication. The main agenda of this trojan is to trick users and steal sensitive information from victims.
The new variant of this malware (Escobar) uses a name and icon like a legitimate app. This malicious APK has the package name “com.escobar.pablo”
Fig 02. Application icon
The operation requests some risky permissions, including:
- Accessibility
- Read/ write the storage
- Send SMS
- Get Account
- Disable Keyguard etc.
It also has capabilities that steal sensitive data such as contacts, SMS, call logs, and device location. Besides recording calls and audio, the malware also deletes files, sends SMS, makes calls, and takes pictures using the camera based on the commands received from the C&C server from malware authors.
The Escobar malware has some new additional features.
- It uses VNC Viewer to remotely control the screen of an infected device.
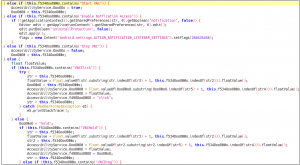
Fig 03. VNC commands used by Escobar
- The malware tries to steal Google authenticator codes on the malware author’s command.
![]()
Fig 04. 2FA code stealing.
- Escobar can also kill itself whenever it gets the commands from the C&C server.
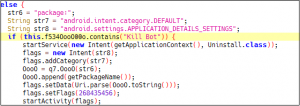
Fig 05. Code used to abort.
Banking malware also used various themes to trick the users. We have seen some applications pretending to be banking reward applications and using the legitimate Indian banking applications icon.

Fig 06. Application icon
The malware can steal credit/debit card information, net banking passwords, and SMS to read/submit one-time generated passwords on the victim’s behalf.
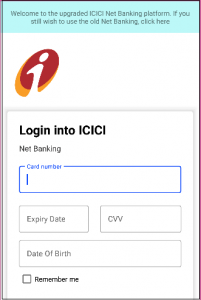
Fig 07. Asking for card details.
All the data is encrypted before sending it to the C2 server. These malicious applications can execute commands on the victim’s device transmitted by the malware authors like uploading SMS, call logs, etc.
When all the SMSs have been uploaded to the C2 server, the malware can also delete all the SMSs from the victim’s mobile device.
Fig 08. Code used to delete SMS
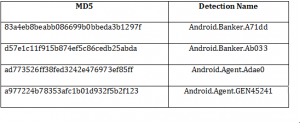
Quick Heal Detection
Quick Heal detects these malicious applications with variants of “Android.Agent” and “Android.Banker” name.
Indicator of Compromises (IOCs):
One should have trusted AVs like “Quick Heal Mobile Security for Android” to mitigate such threats and protect you from downloading malicious applications on your mobile device.
CONCLUSION:
As illustrated above, banking malware uses new techniques to lure users by using icons of legitimate applications. These banking Trojans can cause much harm to the infected devices. These types of banking Trojans are sold by Threat actors on dark web forums and use various websites and third-party stores for spreading. Users should be aware of such fake claims and not download and install such applications from untrusted sources.
TIPS TO STAY SAFE
- Download applications only from trusted sources like Google Play Store.
- Do not click on any links received through messages or any other social media platforms as they may be intentionally or inadvertently pointing to malicious sites.
- Read the pop-up messages you get from the Android system before accepting/allowing any new permissions.
- Malware authors spoof original applications’ names, icons, and developer names. So, be extremely cautious about what applications you download on your phone.
- For enhanced protection of your phone, always use a good antivirus like Quick Heal Mobile Security for Android.



No Comments, Be The First!