Banking Spam Emails Lead to Cryptolocker
Quick Heal Lab has analyzed a malicious email campaign via which attackers intend to install the malicious ransomware called CryptoLocker in the infected machines.
Malware authors are still relying on email to spread malware using social engineering techniques. Such emails are sent with malicious attachments as zip, executable or with double extension. Over the last few weeks we have observed an increase in malicious emails that carry PDF or DOC attachments. PDF attachments contribute to 2% and DOC attachments contribute to 1% of the analyzed malicious emails.
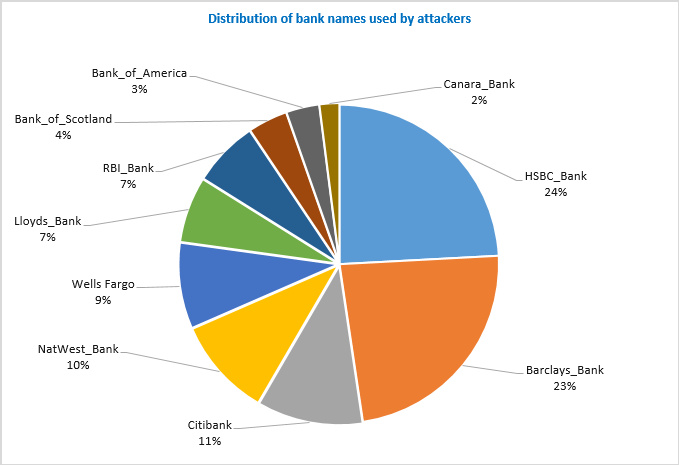
We have analyzed spam emails that seem like they have been sent from banks. In the below chart, it can be noticed that 24% of such fake emails seem to have arrived from HSBC & 23% from Barclays.
These emails usually arrive with the following subject lines:
– Wire Transfer Confirmation
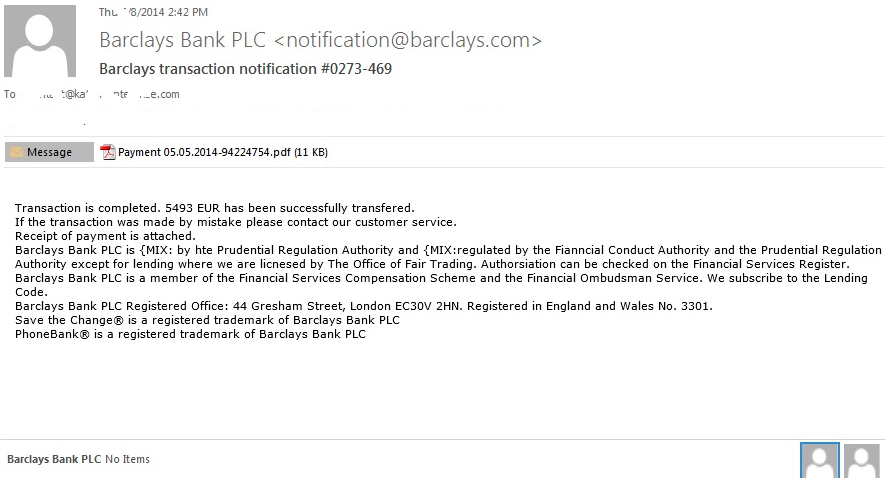
– Barclays Transaction notification
– Attached is your Approved Payment from RBI
The attachments that are sent with these emails contain malicious codes that exploit the Adobe Reader vulnerability CVE-2013-2729 [Adobe Reader BMP/RLE heap corruption vulnerability].
Below are some examples of such emails received by targeted victims:
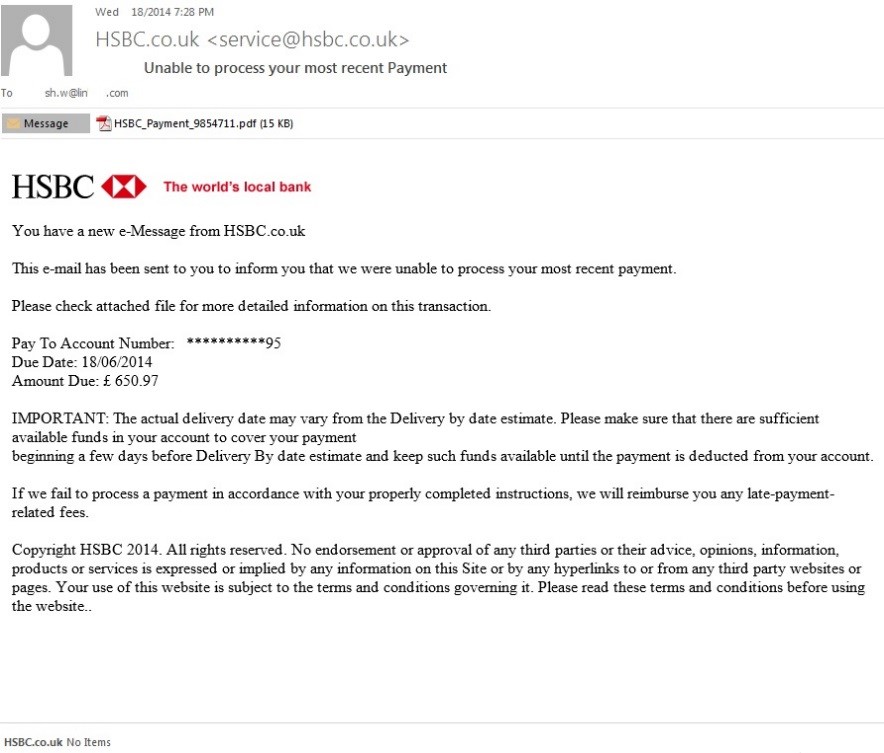
Sample Image 1
Sample Image 2
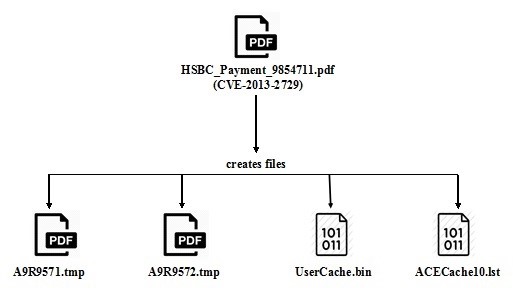
In sample image 1, the PDF attachment “HSBC_Payment_9854711.pdf” contains a shellcode [a small piece of code used as the payload in the exploitation of a software vulnerability] that downloads an executable file from a compromised website.
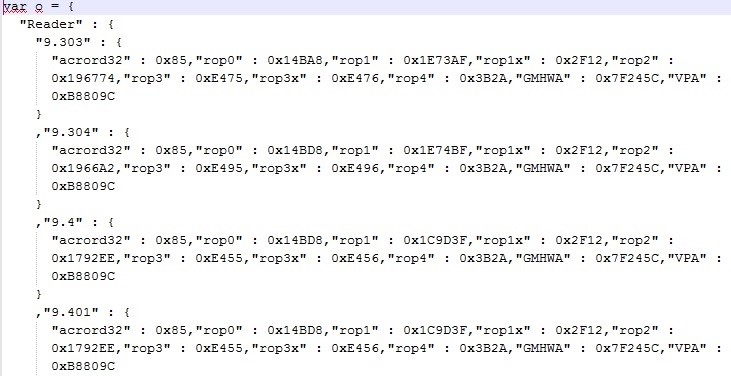
Here, the attackers have used the PoC written by Felipe Manzano and added more ROP offsets to cover as many as 23 different Adobe Reader versions starting from 9.3.0.3 to 11.0.0.1.
The below image shows ROP offsets coded for specific versions of Adobe Reader.
Usually object-1 (the first stream) is encoded twice with/FlateDecode format as (/Fl /Fl).
This object-1 stream is 14 KB in size, which is normal. But after decoding it two times using the FlateDecode method, it occupies more than 86 MB of space.
The decoded code contains Base64 encoded image and Javascript code within an XFA form.
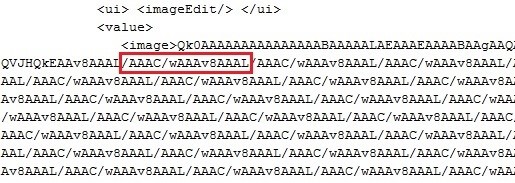
The encoded image is 84 MB in size; it is a BMP file with a repeating pattern “/AAAC/wAAAv8AAAL”.
The AcroForm.api plugin handles the embedded BMP RLE8 encoded image. While parsing this image, Adobe Reader fails to validate the input and triggers a heap overflow, and this results into an arbitrary code execution. In this case, a payload is executed which in turn downloads malicious files from a compromised site.
This PDF also creates four more files which helps the payload to use its data.
Thereafter, it injects its code into MSIEXEC.EXE and then attempts to write into the memory space of all running processes.
After the execution of the first downloaded binary it downloads variant of ZeuS or Upatre malware which in turn downloads the infamous ransomware CryptoLocker.
Read about the CryptoLocker Ransomware.
Quick Heal Antivirus generically detects such exploit PDF files as “Exploit/Pdfjsc.AMJ”.
1 Comment
I am registered user of quick heal software.
Thanks for amazing & interesting information about banking spam emails.