Ako Ransomware targeting businesses using RaaS

Ako Ransomware targeting businesses using RaaS
Quick Heal security researchers recently observed ransomware that uses RaaS (Ransomware as a Service) which is a subpart of MaaS (Malware as a Service). Before delving into the AKO ransomware or RaaS, one must understand what Malware as a Service means, as it is seen that many malware families these days are using MaaS to infect more and more users.
What is MaaS: –
In the legitimate business world, the term Software-as-a-Service is more useful for Software which is controlled centrally and made available for the user by providing the license. Now in malware business, there is the term Maas (Malware-as-a-Service) that provides illegal service for the attackers. The black-market service Malware-as-a-Service provides malware such as Viruses, Worms, Banking Trojans, Ransomware that buyers can acquire and earn money through it.
The criminal customer must pay rent for the malware and the developer needs to keep their Malware-as-a-Service updated by exploring new exploits so that they can target many victims. The recent trend shows that usage of cloud in day to day tasks and business is on the rise multifold & the malware authors are very keen to exploit this user database by selling the malware as cloud services.
Malware-as-a-Service is a managed service model that consists of three levels:
- In the first level, the skilled developer constructs the malware by exploiting known vulnerabilities, malicious payloads through emails, phishing, and various other techniques.
- The second level of distributors will host computer systems.
- The third level is the treasurer for transferring the fund.
The buying and selling of malware such as ransomware etc. take place over the darknet. Darknet is often referred to as the part of the Deep Web which is hidden from the common public. It is the encrypted part of the internet where not just malware trading but several illegal activities like trading of credit card data, or any other PII (personal identifiable information) takes place. The developer uses this platform as a medium to sell their malware.
We’ve seen that many ransomware authors use Darknet to trade their ransomware with potential criminal customers. These authors then sell ransomware with the condition to get a fair share of the ransom that the buyer gets, by spreading it to various networks. This scenario is termed as Ransomware-as-a-Service.
Ako Ransomware: –
The recently observed ransomware named as Ako is also based on Ransomware-as-a-Service. Like most others, instead of targeting individuals, Ako ransomware targets businesses and spreads across networks. It uses emails as a propagation mechanism. The email contains an attachment which is a password protected zip file named as ‘agreement.zip’. Upon the extraction of this zip file, ‘agreement.scr’ is dropped which is an executable file responsible for ransomware activity.
This ransomware is written in Microsoft Visual C/C++.
Binary Analysis of the Ako ransomware: –
While analyzing the Ako ransomware, we found a list of blacklisted and whitelisted file extensions.
The list can be seen below in fig.1a and 1b.
![]()
fig.1a List of blacklisted extensions.
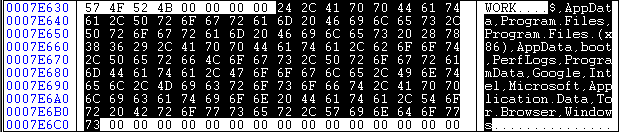
Fig.1b Blacklisted file paths
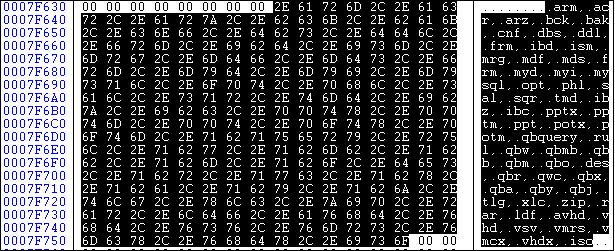
Fig.2 Whitelisted extensions
Execution flow:
- At the beginning of execution, it disables the windows recovery environment. Also, it deletes all shadow volume copies and recent backups.
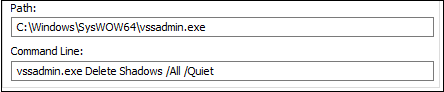
Fig.3 Command used to delete the shadow copies.
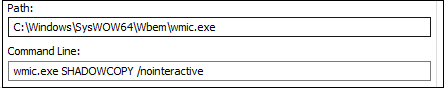
Fig.4 Commands for disabling recovery environment
- The ransomware creates a new value EnableLinkedConnections under the registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System Using RegCreateKeyA And sets the value of HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\EnableLinkedConnectionsto 1 using RegSetValueExW .
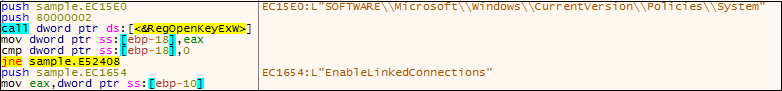
Fig.5 Addition of Registry Key
- This value is set so that the ransomware can gain access to the processes that require User Access Control (UAC). In case it does not have UAC permissions, it will not be able to spread through mapped network drives.
- It begins encryption according to the blacklisted and whitelisted file extensions and avoids files from the program files, system data. It makes sure that the files encrypted have important data of the users such as documents, databases, spreadsheets, archives, presentations, images, and other file types. In this way, the user is forced to pay the ransom. After encryption, it adds the randomly generated extension which contains six digits alphanumeric as shown below.
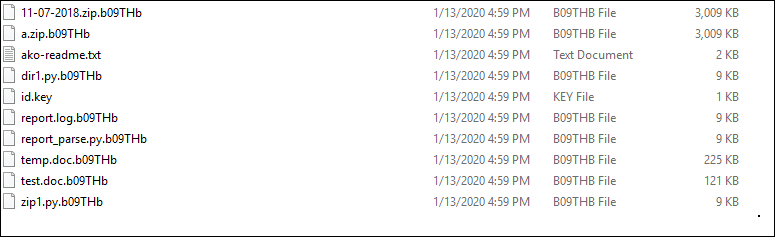
Fig.6 Encrypted files
- It also adds a file marker ‘CECAEFBE’ hex value at the end of each encrypted file. The marker is added as an indication that the file is already encrypted and this way it’ll save a lot of time. The marker is shown below in the fig.
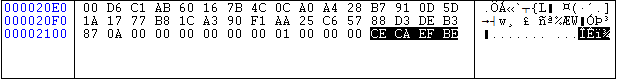
Fig.7 File marker
- After encrypting an entire system, it scans the network for other systems that can be encrypted. It uses ‘IcmpSendEcho’ function to search for other IP addresses in the domain. It further keeps hunting for new systems after encrypting an accessible system.
![]()
Fig.8 Loop used for scanning Ip’s one by one
- It uses AES Algorithm for encryption of the files and the key for decryption of files is also present in the victim’s system in an encrypted format, so it’s hard to decrypt the files.
Ransom Note: –
Ako drops a ransom note ‘’ ako-readme.txt’ in every folder which contains an infected file. Along with the ransom note, it also drops an ‘id.key’ file. Through the ransom note, it informs the victims that their network has been locked. Like other ransomware, it doesn’t provide the victim with email id. Rather it provides them a link to a website that can be accessed through ‘Tor Browser’ and even guides them on how to download it.
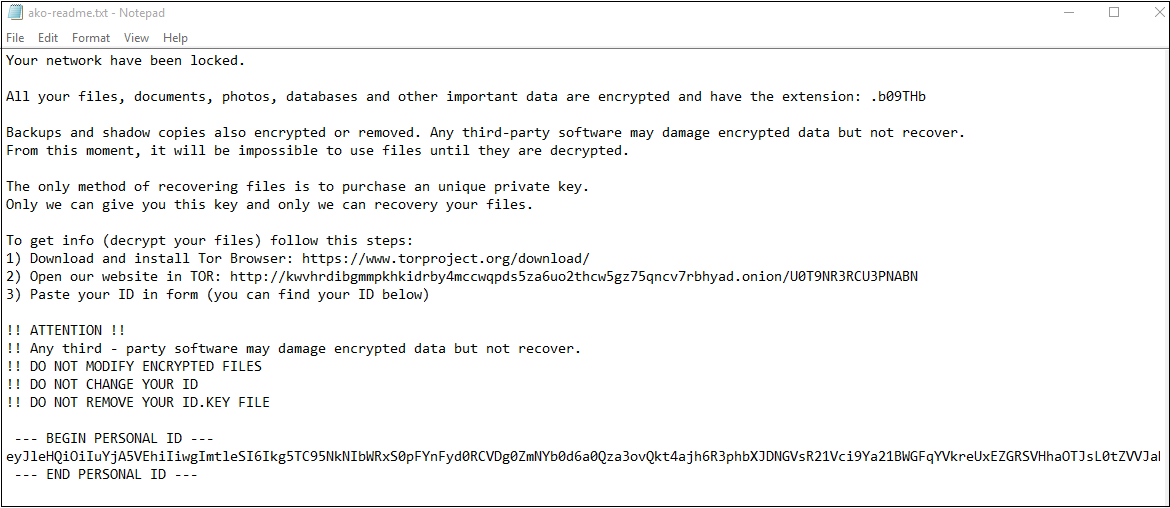
Fig.9 Ransom Note
The personal ID in ako-readme.txt is a BASE64 encoded text. When we decode the text, we get the JSON formatted text which contains an extension to be added after encryption, an encrypted key which is same as the key in the ‘id.key’ file. In addition to the key, it also contains information about the network configuration settings, version of ransomware and sub-id.
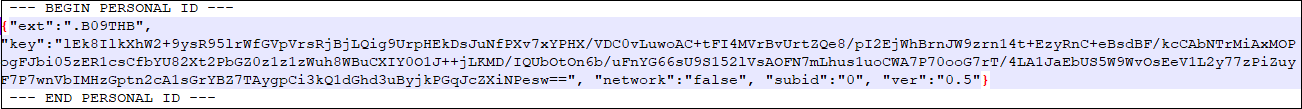
Fig.10 Decoded Personal ID
On visiting the website, it asks to enter the unique decryption key which is in the ransom note itself. Then it asks the victim to transfer the ransom into a bitcoin wallet.
Safety measures:
- Patch your PCs and server early and frequently.
- Be careful while downloading files from unidentified email addresses.
- Don’t enable MACRO’s while viewing doc files received through emails.
- Back up your PCs and Servers regularly and remember to keep a copy in some external storage drive.
Because it is said:
Prevention Is Better Than Cure!!!
Subject Matter Experts: – Shivani Mule, Lavisha Mehndiratta | Quick Heal Security Labs
No Comments, Be The First!