Deep Dive into Royal Ransomware

The rise of ransomware and malware variants has been a growing concern for individuals and organizations alike. With new strains of malicious software emerging every day, the threat landscape has become increasingly complex and dangerous. Let’s delve into the world of ransomware and explore how we can protect ourselves against this ever-evolving threat.
Introduction
The Royal Ransomware was first observed in mid-2022. It is a type of ransomware that encrypts all volumes including network shared drives. The Royal Ransomware uses the“.Royal“, and “.Royal_w” extension on the encrypted files instead of some randomly generated extensions like other ransomware use. The group behind Royal Ransomware operates independently. The group drops the ransom note with the name README.TXT which contains the unique “tor” link for further communication with the attacker. This ransomware is distributed through torrent sites, malicious attachments, and more. This ransomware uses the AES algorithm with the key and IV encryptions using the RSA. The encryption of the file is decided on the basis of the “-ep” parameter.
Timeline of Ransomware
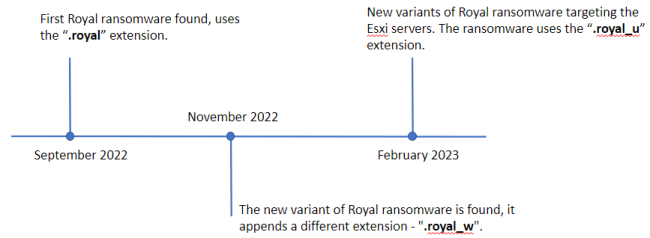
Timeline of Royal Ransomware
Technical Analysis:
On initial execution, the Royal ransomware takes the command line arguments; Path, id, and ep, where the id is a 32-bit array, and ep is the encryption percentage.
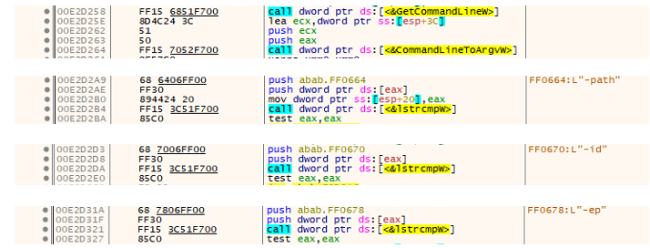
Calling cmd with arguments
Deletion of Shadow Copies:
Volume shadow copies are deleted to prevent system restoration.
vssadmin.exe Delete Shadows /All /Quiet
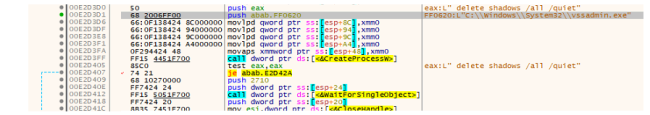 Deletion of shadow copy
Deletion of shadow copy
Before the encryption process, it creates a list for the exclusion of extensions and directories which are further used by threads at the time of encryption. In the new variant. Royal_w and .Royal_u are added in the excluded extensions.
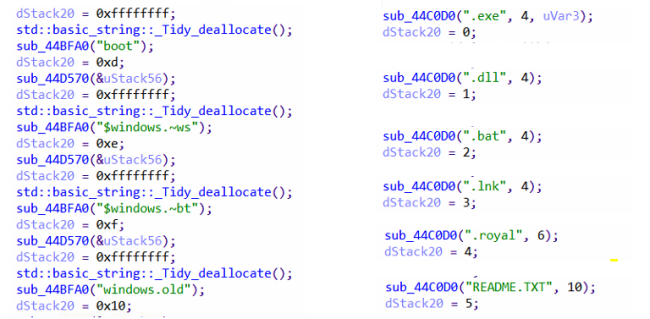
List of directories and extensions to be excluded from the encryption process.
List of extensions excluded –
|
.exe |
.dll |
|
.bat |
.lnk |
|
.royal |
.royal_w |
List of directories excluded –
|
windows |
royal |
$recycle.bin |
|
|
perflogs |
mozilla |
|
tor browser |
boot |
$windows.~ws |
|
$windows.~bt |
Windows.old |
File Encryption:
The ransomware uses the GetNativeSystemInfo API to retrieve the number of processors in a machine, then it multiplies the result by two and creates a number of threads.
These threads are responsible for the file encryption process.
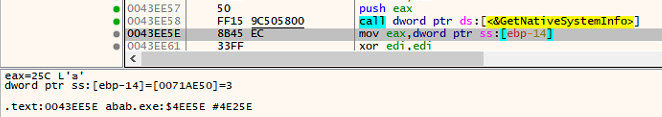
 Thread creation
Thread creation
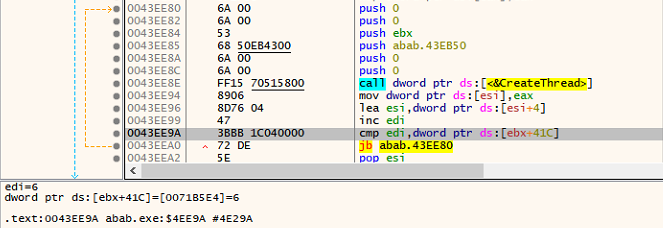
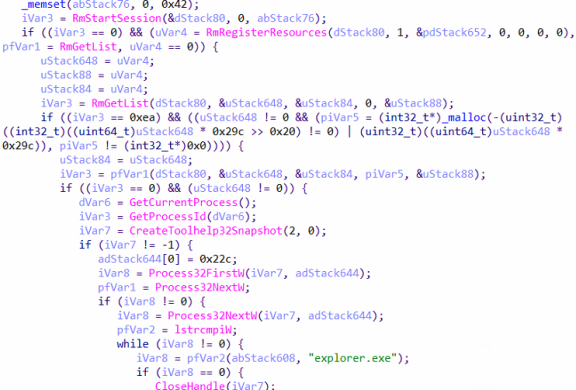
With the help of Restart Manager, it checks if there are any files that are being used by the other processes.
Royal ransomware uses the RmGetList APIs to verify which process is using the resources, and then, it compares it with explorer.exe. If the process is not explorer.exe, it calls the RmShutDown API to kill those processes.
Process kill through RmShutDown API
Royal Ransomware uses the RSA public key for encrypting AES key and IV. And the RSA Public key is embedded in the executable.
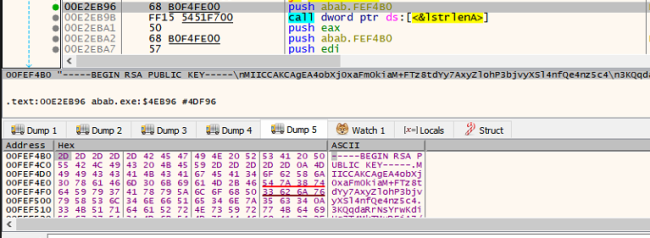
RSA Public Key
It enumerates the Drives with the API call GetLogicalDrives and adds the README.TXT in each drive, as illustrated in the following images.
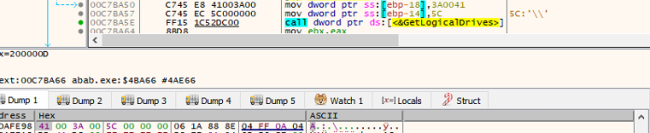
Enumeration of Logical Drives
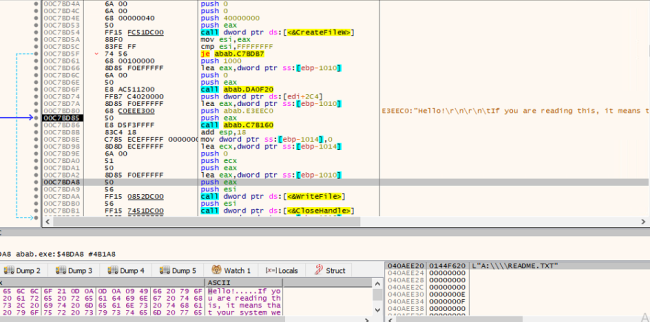
Readme file is created at A:\\
To compare the Directories and the Extension for the exclusion, it uses the API strstrIW. In the figure below the excluded directory and extensions are compared with the current directory and file respectively.
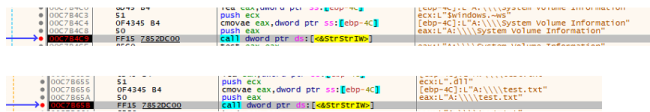
Comparing directory and extension to the Excluded list
After the encryption through the AES algorithm, it uses the MoveFileExW API to append the extension “.royal”.
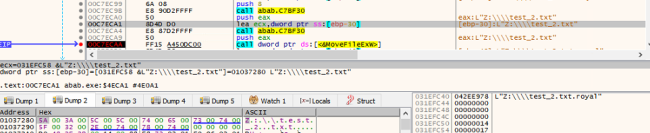
Adding the “.royal” extension
The encryption is based on two parameters, i.e. file size and the value of ep. If ep is not provided, it encrypts based on the files size parameter, as per the following:-
- If the file size is smaller than or equal to 5MB, the entire file will be encrypted.
- If the file size is larger than 5MB, only partial (50%) encryption is done.
After the encryption of the file, it writes the size of the file followed by the encryption percentage in hex at the end of the files. We can see this in the following encrypted file, as an example: –
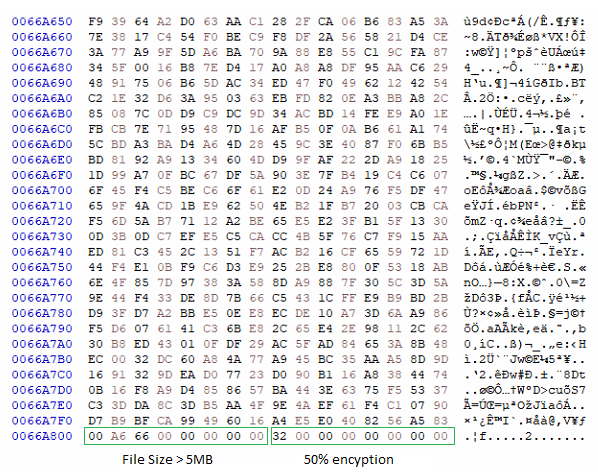
Encrypted file 1
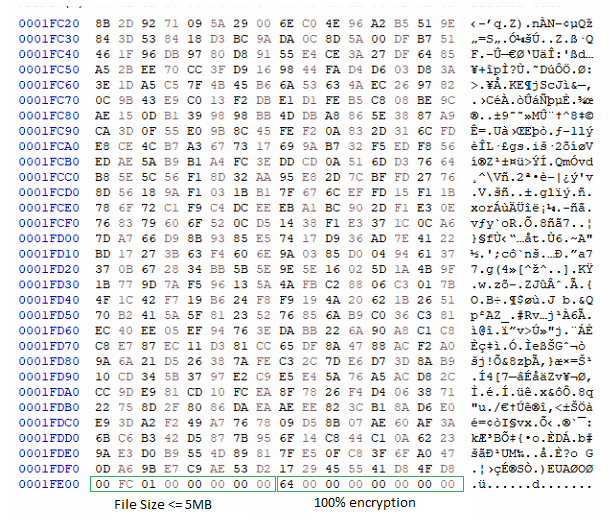
Encrypted file 2
After encryption, it uses the “.royal ” extension.
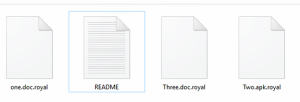
Encrypted files by the “.royal” extension

Encrypted files by the “.royal_w” extension
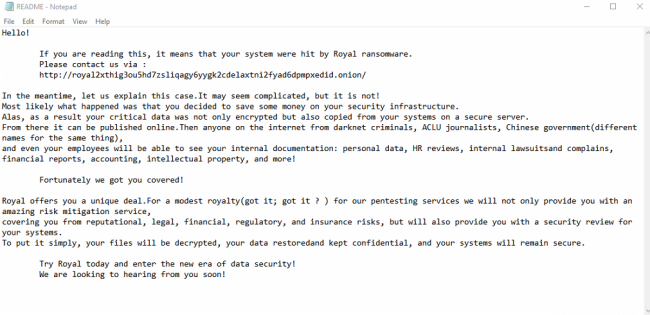
Ransom Note
Royal Ransomware drops the “README” file in every encrypted directory. It uses the tor link for further communication purposes.
How do we prevent such kinds of attacks?
- Do not download and open any attachments from unknown sources.
- Avoid clicking on any unverified links. The main cause of ransomware attacks happens due to clicking on untrusted links and attachments.
- Keep your software and antivirus updated.
- Back up your data so that it can be recovered in case of a ransomware attack.
Quick Heal Protection:
-
Ransom.Royal.S29629175
-
Ransom.Royal.S28994725
To know more about Quick Heal’s range of digital protection visit –
Conclusion:
The Royal Ransomware encrypts files with “.royal” while some other variants use the extensions “.royal_w” and “royal_u.” It has the unique feature of encryption through ep mode, which allows Royal Ransomware to modify the encryption percentage based on the file size.
As Royal ransomware uses a similar encryption technique to Conti, we suspect that the Conti group might be involved in this.
MITRE ATT&CK TTPs:
|
Command and Scripting Interpreter |
T1059 |
|
Inhibit System Recovery |
T1490 |
|
File and Directory Discovery |
T1083 |
|
System Information Discovery |
T1082 |
|
Data Encrypted for Impact |
T1486 |
|
Service Stop |
T1489 |
IOCs:
250BCBFA58DA3E713B4CA12EDEF4DC06358E8986CAD15928AA30C44FE4596488
15D4A2FC500DFA55A64221A0A38D9C47510D8D348D3289C89D26E6184DDD51FF
491C2B32095174B9DE2FD799732A6F84878C2E23B9BB560CD3155CBDC65E2B80
312F34EE8C7B2199A3E78B4A52BD87700CC8F3AA01AA641E5D899501CB720775
87EED751035A0BCCE040079E48545A7265E1A0C7D4BCAF0B37A8A70D833FEAFC
42EEC2B721E59640D7B88202B80D2D9A5C84BF34534396098A497A60EF5EBB97
8E01ECF9D804454F34EECEB0F7793F4884BE8868886A646526419FC2E2BBB648
BED8C25DD445B9B9A782291C00F9839890A09459A2A568153491B2F47BBD1463
Co-Author:
Soumen Burma


No Comments, Be The First!