A sloppy click can exfiltrate your important data!

Phishing email still remains one of the top malware propagation medium. Recently, we came across an interesting phishing email containing couple of Jumpshare links pointing to malicious components. Jumpshare is an online file sharing service and often cyber criminals abuse these kind of file sharing services.
Upon clicking on one of the links in phishing mail, an executable file with name ‘90DayDemoPurpleCDR2019-Analysis-Software.exe’ was downloaded. It is an unsigned 32-bit executable file, compiled in Borland Delphi. Following is the version information found in the trojan.
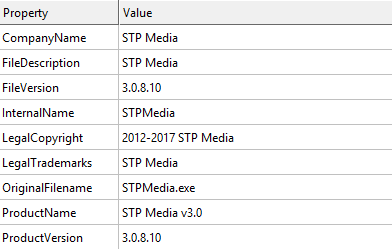
Fig. 1: Version Information
On execution, this file creates a copy of itself in following directory:
C:\Users\<USER>\AppData\Local\Microsoft\Windows\mshtinr.exe
It also drops a DLL at same location as ‘mshtinr.dll’. Then it creates a process ‘svchost.exe’ using ‘CreateProcessA’ windows API in suspended state. Further, it decrypts a DLL code in memory and that DLL is injected in target process i.e. ‘svchost.exe’. Using multiple ‘WriteProcessMemory’ API calls, it imports required modules and APIs in the newly created process and finally transfers the control to the DLL. Before that, the sample sets values in the following registry key:
HKCU\Software\Microsoft\Internet Explorer\Prefs
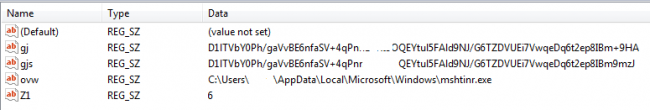
Fig. 2: Registry values set by the sample
Later these values are accessed by the target process i.e. ‘svchost.exe’.
The ‘svchost.exe’ process drops couple of files at following location:
C:\Users\<USER>\AppData\Local\Google\Chrome\User Data\Default\gjs.tmp
C:\Users\<USER>\AppData\Local\Google\Chrome\User Data\Default\<Number>.tmp
The ‘gjs.tmp’ file contains multiple functions for handling SQLite database and latter is the copy of Google Chrome user login data file, generally found at following location:
“C:\Users\<USER>\AppData\Local\Google\Chrome\User Data\Default\Login Data”
The .tmp file (named with some numerical values) contains the login information for the portals accessed through Chrome. This file is a SQLite database having credentials information in it.
This SQLite database contains following tables related to login information and other metadata information:
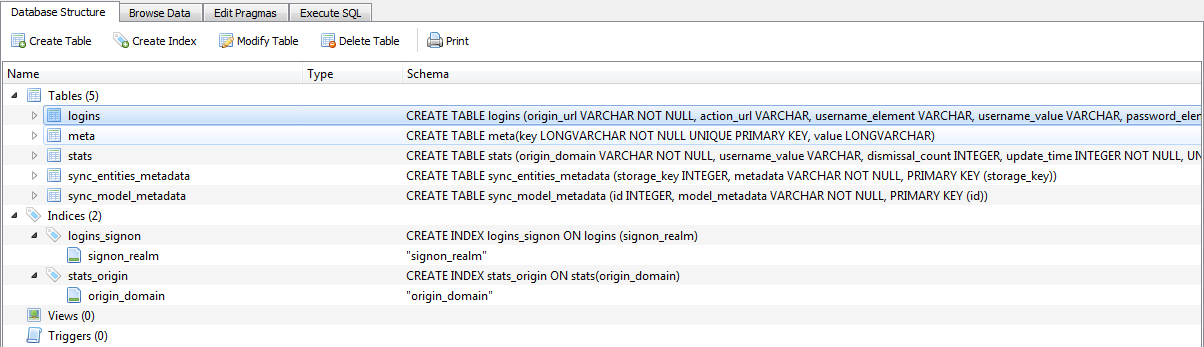
Fig. 3: SQLite schema for Chrome Login Data
Below is an example of login information and credential captured in database.
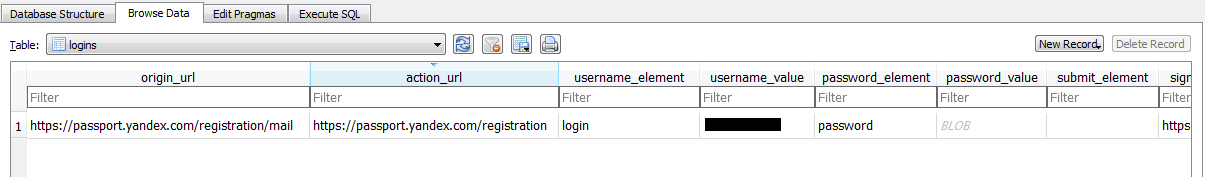
Fig. 4: Stored credential in SQLite
The dropped file ‘gjs.tmp’ is loaded in the memory and control is then transferred to it. This shared library queries the data to the SQLite DB i.e. copy of Login Data. Once the required information is retrieved, it deletes the database file.
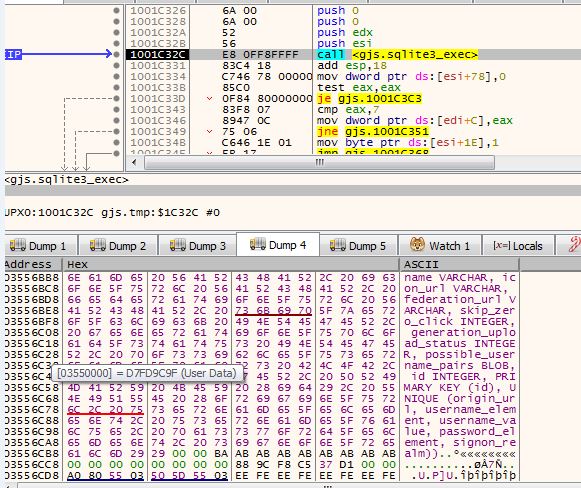
Fig. 5: SQLite query execution
We have also found keylogging activity in the svchost.exe process. It uses APIs like KeyboardType, KeyboardLayout, GetKeystate, etc. for the same.
All the keylogging output is stored in a file:
“C:\Users\<USER>\AppData\Local\Microsoft\Windows\mshtiner.ihg”
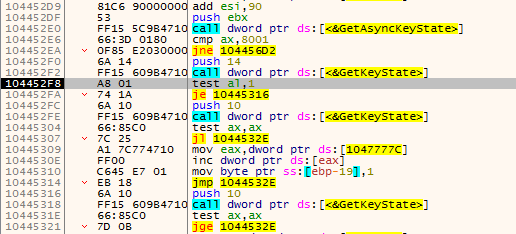
Fig. 6: Keylogging APIs
This information is stored in encrypted form. Further it copies this file to ‘elmshtinr.ihg’ at same location and deletes the original one.
Once all the data collection process is done, it sends the data to pre-defined email-id that is found in the process memory. The e-mail is composed using Microsoft’s CDO library over port 465 which is generally used for SMTPS protocol. The email-id to which data is sent was on gmail and source email-id was on ’totallyanonymous.com’ with pre-defined credentials. Email-ids and FTP on ’totallyanonymous.com’ were often observed previously during malware analysis cases.
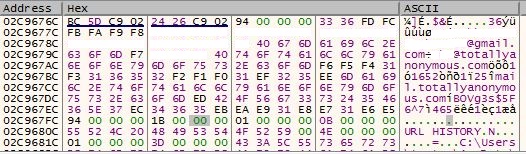
Fig. 7: Interesting strings
Also, the sample changes the last modified date for all the created files to ‘20-Nov-2010 7:24 PM’. So, in case we observed these files, the last modification date may confuse us regarding the genuineness of these files.
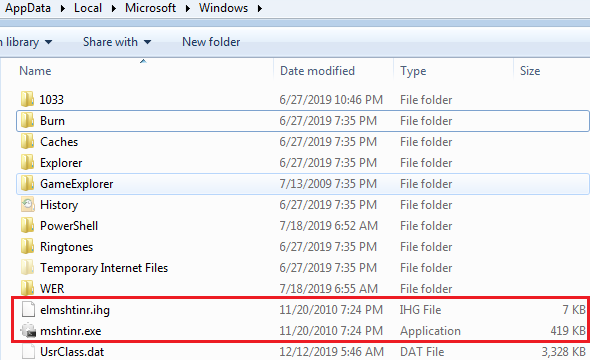
Fig. 8: Modified dates of newly created files
IOCs:
| Filename | MD5 |
| 90DayDemoPurpleCDR2019-Analysis-Software.exe | EE279BB854CA338BF50A3A682830C4E5 |
| mshtinr.exe | EE279BB854CA338BF50A3A682830C4E5 |
| mshtinr.dll | D3EAEC2B55A2D24289B03EB86EA2166D |
| gjs.tmp | 1023DF7ABD2D9B7F0BDC77024C978F0B |
Summary:
- The sample is a keylogger and an information stealer. It tries to retrieve the login data of Google chrome installed in the system of the victim.
- It uses process code injection technique for doing its main activity,to evade detection from security products.
- It uses various techniques to remain unnoticed in the system like dropping payloads in Google Chrome directory.
- The email-addresses were used to exfiltrate the collected data to the attacker.
Subject Matter Expert:
Rahul Sharma, Quick Heal Security Labs.


No Comments, Be The First!