Breed of MBR Infecting Ransomware – an analysis by Quick Heal Security Labs
Ransomware is becoming one of the most perilous cyberattack methods and also the most habitual techniques for cybercriminals to earn money. It appears to have new weapons in its arsenal over time which is invariably aimed to boost its strength and enhance its business.
As encrypting the files and restricting the user access is not enough, ransomware also infects the master boot record and prevent the operating system from loading. As the operating system is not loaded, none of the ransomware tool or antivirus work for these type of ransomware. Even though this technique is also seen last year (in case of PETYA ransomware), this year there has been an exponential increase in MBR infection by ransomware.
MBR infection extends the scope for deep infection and controls the infected computers, which make the attack more severe. Ransomware copies the original MBR and overwrites it with its own malicious code. After that, it automatically restarts the system for the infection to take place. When the system restarts, the user is locked out and the ransomware displays its note and asks for a ransom.
Master Boot Record
Master Boot Record (MBR) is a small program that executes every time the computer boots, even before operating system loads. It is used for start-up process and has information of bootable partition. The MBR resides on the first sector of the hard disk.
OS Booting Sequence

Fig 1. OS booting Process
BIOS tries to read the first physical sector i.e. MBR from the boot device. If no MBR is found, an error message is displayed. Since the MBR executes every time a computer is started, an MBR infection can be extremely dangerous.
Recently, Quick Heal Security Labs analyzed various ransomware as well as MBR infections. This additional infection feature grasps attention which is trending in almost all the upcoming ransomware. We will discuss few of the recent ransomware.
Annabelle ransomware
Annabelle ransomware goes a step ahead in infection and comes up with the whole shooting match to vandalize a computer. It takes your computer hostage and does everything to ruin the system.
It encrypts all files on a computer and appends the .annabelle extension to the encrypted files, it attempts to disable the firewall, terminates the list of processes including security programs, spreads via connected USB drives and ultimately, overwrites the MBR with its own code. It destroys every hard disk connected to the system. It adds its entry in the registry to automatically execute when a user logs into Windows.
In fig 2, we see a pseudo-code of the malware which calls CreateFileA for taking the physical drive handle and write 0x800 bytes on each physical drive. Also, it does not take backup of clean MBR.

Fig 2. Calling CreatFileA for taking handle to write on physical drive
After infecting the hard disk, RtlSetProcessIsCritical is called – this function sets your process to a system critical status. As a result, the termination of this process will result in a termination of Windows as well. Calling RtlSetProcessIsCritical (1, 0, 0) will set the process as critical.

Fig 3. Calling RtlSetProcessIsCritical
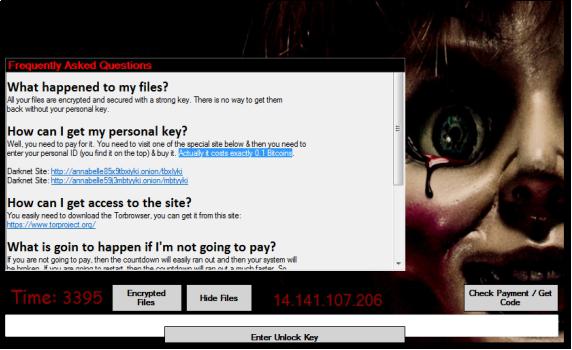
It finally calls shutdown.exe with parameter -r -f -t 0 to restart the system, -r is used for complete shutdown and restart of the system and -t to force running applications to close without forewarning user. After system restart, the malware file gets executed and a ransom note is displayed as shown in fig 4. This is the first image after infection. The ransom asked is 0.1 Bitcoin. The malware also sets the countdown timer for paying ransom within that time.

Fig 4. Ransomware 1st image after reboot
If the user does not pay the ransom within the time limit displayed on the screen set by the malware, the screen is changed as shown in fig 5 and the user is locked out. The malware finally replaces the MBR and makes the system unfit for use.

Fig 5. Ransomware 2nd image after reboot
Its pure intention is to destroy the system completely if the user refuses to pay the ransom. Initially, it seems that it is just a ransomware which encrypts files although at a later phase, its behavior clarifies that it wants to deliberately destroy the user’s hard disk data.
MBRLock Ransomware
MBRLocker a.k.a. DexLocker was identified in Feb 2018. This ransomware modifies the master boot record of the victim’s computer and asks for a ransom of 30 Yuan before Windows starts.
The malware file is compiled in Visual C++. On execution, it tries to read the physical drive using createfile API and takes access of the physical drive.

Fig 6. Calling CreateFileA
Then it calls SetFilePointer and sets the offset to zero of the physical drive to access MBR. It reads 0x200 bytes of the physical drive in memory and writes on another sector for restoring in future. Fig 7 shows the file pointer is set to 0x400 for writing clean MBR for backup.

Fig 7. Calling SetFilePointer
The hard disk view before replacing code is shown in fig 8.

Fig 8. View of hard disk before infection
It stores the clean MBR at 0x400 offset i.e., 2nd sector of the hard disk and replaces the original MBR with the malicious code. Fig 9 shows the write operation & length of bytes to be written.

Fig 9. Process Monitor showing read-write operation
After taking a copy of the clean MBR, the malware writes a malicious code at zero offset so that whenever the system boots, the malicious code executes first.

Fig 10. Writing Malicious Code At 0 offset
Hard disk view after replacing MBR with malware code is shown in fig 11.

Fig 11. Hard disk view after infection
After replacing MBR, the malware calls ExitWindowEx API to restart the system.

Fig 12. Calling ExitWindowEx API
When the system restarts, an image is displayed as shown in fig 13. The malware does not allow the user to log in to the system. It asks for a ransom for unlocking. The message which is displayed on the screen with ascii skull is “send 30 yuan to the 2055965068 qq address in order to get access to their computer again”.

Fig 13.Message after rebooting the system
When ransom amount is sent to the specified address of the malware author, it may send the password for unlocking the screen. The password can also be tried if we use brute force method. The password may be cracked easily with this technique.
In an analysis of 16-bit code of MBR, the malware compares the entered Password with one string which is present in its code. The String or we say the password is “ssssss”. Unlike other ransomware, unlocking the screen of this ransomware is quite easy which can be done without paying any ransom.

Fig 14. Checking password in MBR code
If the same password is entered in the locked screen, then the malware restores the original MBR present at 3rd sector (sector count start from 1) and unlocks the screen. Fig 15 shows the read and write original MBR after the correct password is found.

Fig 15. Read and write operation on disk
- MBRLock Ransomware is quite easy to unlock although all are not same as seen in case of Annabelle ransomware which destroys each hard disk and does not allow the user to boot system properly. Some more MBR infecting ransomware are KillDiskFake ransomware and DiskWriter or Uselessdisk ransomware.
- Some ransomware may write some bytes in a sequence which may or may not make any sense to the user. On the other hand, some purposely wipe out all the data of hard disk for destruction purpose like in case of killDiskFake ransomware.
Conclusion
In this blog post, we have explained ransomware whose target is to gain money by infecting MBR. This ransomware has taken the level of infection at a higher level. Infected MBR does not allow the user to even boot system in safe mode.
Prevention measures to stay away from ransomware
- Altering of MBR and other sectors in the hard drive requires advance privileges. That means one can effectively avoid infection by lowering their privilege level and extending the security level in the systems. Using a non-admin user account will reduce the damage caused by a virus infection.
- Avoid clicking on suspicious links or email attachments.
- Apply the latest security patches to fix the vulnerabilities in Windows in order to diminish the chance of attack.
- We recommend our users keep their antivirus products up-to-date.
Indicators of compromise
7a243bcbff4309eafd287ecc124606171724da76fc3c1896002e5f7392b13df3
Dfc56a704b5e031f3b0d2d0ea1d06f9157758ad950483b44ac4b77d33293cb38
Subject Matter Expert
Preksha Saxena | Quick Heal Security Labs

No Comments, Be The First!