Malware Case Study: Kraken RAT Running Behind Bitcoins
Bitcoins have been in the news recently for various reasons and their popularity has also led to several scams, thefts and hacks aimed at them. It is found that exploit kits for targeting Bitcoins are readily available in the underground community and these are proving to be highly lucrative as well. The Quick Heal Threat Research Lab has analyzed samples of Kraken RAT (Remote Access Tool) which is now being used for stealing Bitcoins and mining on infected systems.
Behavior:
Kraken RAT is deployed using Microsoft Office document vulnerabilities such as CVE-2012-0158. Infected documents drop malicious components in systems and then report back to Command & Control (C&C) servers with information about systems and then download next stage components which are used for Bitcoin mining or the stealing of Bitcoin wallets.
The exploit document contains shellcodes to download and execute files from “hxxp://23.249.163.140/tilt.exe”.
A] It then copies itself to the following locations:
- C:Documents and SettingsAdministratorApplication DataSystemOraclesmss.exe
- C:WINDOWSexplorersmss.exe
B] It makes a Run registry entry as:
“HKLMSOFTWAREMicrosoftWindowsCurrentVersionRunWindows:value:”C:WINDOWS
explorersmss.exe”
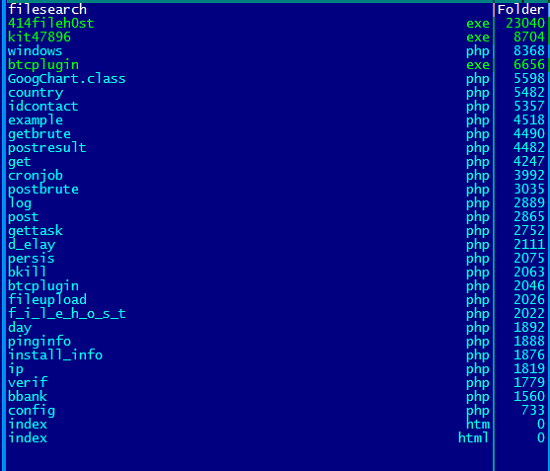
C] It then communicates back with the C2 server to get the Bitcoin address after running some checks and running scripts like verif.php, fileupload.php, f_i_l_e_h_o_s_t.php and persis.php.
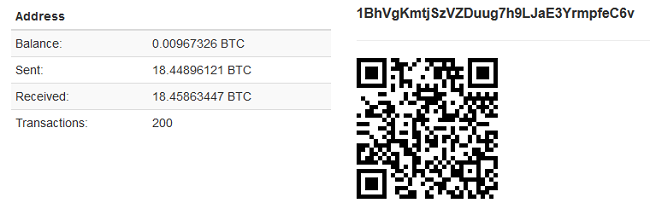
D] Then it gets the Bitcoin addresses that are returned from btcplugin.php. In this case, the Bitcoin address is “1BhVgKmtjSzVZDuug7h9LJaE3YrmpfeC6v”. We could see 18 BTC traded on this address in a total of 200 transactions.
E] It collects specific information like special games based on Steam or Origin marketplaces, web browsers, Java, .NET and more.
F] It checks to see if any of the popular antivirus products are installed and it also collects the following system information:
- Device RAM
- Hard disk size
- Whether system supports GPU or not
- CPU version
G] It then downloads and executes btcplugin.exe which is used to steal bitcoins which have the following file extensions:
Test2.doc;upx.doc;bitcoin.dat;filestealer.dat;Account.txt;Steam.txt;Brother.txt;Pro.txt;Dofus.txt;Diablo.txt;WOW.txt;Account.txt;hackforums.txt;market.doc;information.com;documentation.doc;bitcoin.dat;wallet.dat;discover.txt;filestealer.dat;Account.txt;Steam.txt;Brother.txt;Pro.txt;Dofus.txt;Diablo.txt;WOW.txt;Account.txt;hackforums.txt;market.doc;information.com;documentation.doc;bitcoin.dat;wallet.dat;discover.txt;filestealer.dat;Account.txt;Steam.txt;Brother.txt;Pro.txt;Dofus.txt;Diablo.txt;WOW.txt;Account.txt;hackforums.txt;market.doc;information.com;documentation.doc;bitcoin.dat;wallet.dat;discover.txt;filestealer.dat;Account.txt;Steam.txt;Brother.txt;Pro.txt;Dofus.txt;Diablo.txt;WOW.txt;Account.txt;hackforums.txt;market.doc;information.com;documentation.doc.
H] The Kraken RAT then communicates with the C2 server in order to download and execute other malware as well.
Command and Control Panel:
Given below is the image of the control panel for the Kraken bot used in this campaign.
The hosted panel on the C2 server shows php scripts.
Bitcoin Mining Information:
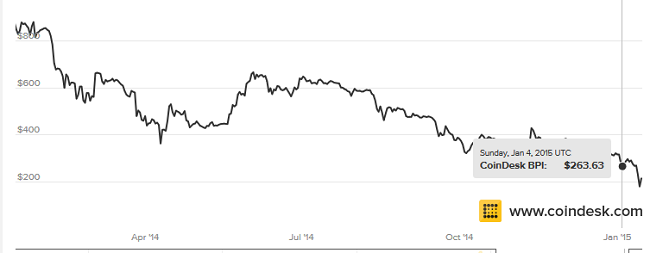
The Bitcoin address “1BhVgKmtjSzVZDuug7h9LJaE3YrmpfeC6v” is active and has been used for 200 transactions which have thus far resulted in 18 bitcoins. However, recent hacks on Bitcoin exchanges have led to drastic fluctuations in the Bitcoin exchange rate. While this rate was $860 in January 2014, it has dropped to $260 in January 2015, hence pointing to a falling trend in Bitcoin’s popularity.
References:
Exploit used – CVE-2012-0158
RTF file MD5: 08e834b6d4123f0aea27d042fceaf992
tilt.exe MD5: 02fd960e150782f1990a2e1bceb50f95


4 Comments
Great article about bitcoin targeting malware
VERY VERY NICE audit.
I have seen some of this in my country as some access logs.
Also there is in the wind some cryptolockers is this kind of type ?
Hi,
Great info once again.
Does Quick Heal browsing protection / Phishing protection blocks ( https://23.249.163.140/tilt.exe ) ?
Hi Onil,
If the link is malicious or potentially dangerous, then Quick Heal will block it.
Regards,