CryptoLocker – the New Ransomware on the Loose
Previously we had reported about the “FBI virus”. The virus locks the computer screen and stops the user from using the infected machine until they agree to pay a certain amount of money to the cybercriminal.
Today, we will discuss a new entry in the list of file encrypting ransomware; it is known as “CryptoLocker”. Last week some of our customers had reported the occurrence of this malware. Once it gets executed, it encrypts files in the victim’s computer, and demands a certain ransom for decryption. This ransomware is spread using social engineering tricks via social media and email attachments.
How does CryptoLocker work?
– When CryptoLocker gets executed, it copies itself at the root of %APPDATA% folder with names as {GUID}.exe and takes up hidden attributes.
For example, C:Documents and SettingsAdministratorApplication Data{71257279-042B-371D-A1D3-FBF8D2FADFFA}.exe
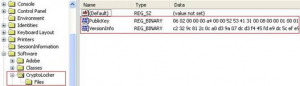
– The ransomware uses RSA algorithm with 2048 bit key. It communicates with random servers whose names are generated using Domain Name Generation (DGA) algorithm. The server generates a pair of public and private key for the machine of the targeted user. The private key is kept on the server for the next 72 hours. The public key is sent to the malware running on the user’s machine using secure communication, which is stored under HKCU registry key as shown in the following image:
– The malware starts looking for files extension mentioned in the following list.
From the list, as we can see, the malware targets all users who possibly would have some important information stored on their machine and would want to restore it back.
*.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.pdf, *.mdf, *.dbf, *.psd, *.pdd, *.eps, *.ai, *.indd, *.cdr, ????????.jpg, ????????.jpe, img_*.jpg, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7c
The list of infected documents is kept under HKEY_CURRENT_USERSoftwareCryptoLockerFiles to avoid multiple encryptions.
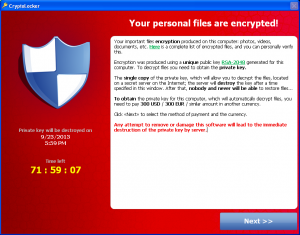
The CryptoLocker Ransomware Looks like this:
CryptoLocker provides three ways of making payment , viz. MoneyPak, Ukash and Bitcoin. The amount is equivalent to 300 USD. The amount could be paid in 15 different currencies. Bitcoin, reportedly, is being increasingly used by malware authors.
It is extremely difficult to recover encrypted files once they are encrypted with RSA algorithm, until we have the private key.
How can you Detect CryptoLocker?
Quick Heal detects this family of ransomware as Trojan.Crilock.A.
Recommended Security Measures
Taking the following security measures would help reduce the risk of such malware attack:
- Ensure that all important software on your machine, such as the Operating System, Adobe Reader, Microsoft Office, and internet browsers to name a few, are patched and up-to-date.
- Keep your machine’s security software up-to-date.
- Avoid clicking URLs and opening unsolicited email attachments, particularly from unknown sources.
- Be careful while using removal medias such as pen drives, external hard disks, etc. that are connected to machine not protected by updated security software.
- Always keep a backup of all your important documents using a reliable backup software.
As technology is touching newer grounds, malware authors are discovering better and sneakier ways to attack their targets. If one malware family is taken down, another one gets developed in no time. In such a scenario, taking the right precautionary measures and using the right security tools, should be your best defense against all malware in the wild.


27 Comments
Really gr8 info Rajesh sir
Thanks and Regards,
Hrushi Sonar.
nice information for cryptlocker and thanks for updating us
Dear Rajesh sir,
Thank You For updating Our Knowledge regarding file encrypting ransomware
Thank You Rajesh sir, for share this valuable information with us.
Sir, My computer is infected by Trojan.Nymaim and a packed file named Trojan.Agent.IRC.n3 and quick heal pro skip this packed file, What this viruses are cryptolocker or ramsomware.
All my word, excel, pdf files are not working even after removing cryptolocker manually. I also scanned the computer but still the Quick Heal antivirus is not repairing any files and showing as no virus found. Any solutions? All are official files
Hello Divyesh,
Kindly contact our support team at 0-927-22-33-000.
You can also raise a query at https://www.quickheal.com/submitticket.asp. Our support team will get back to you to resolve the issue you are facing.
Regards,
Dear Sir,
how to decrypted file??
Hello Haresh,
As we have discussed in the blog post, Cryptolocker uses asymmetric encryption algorithm where 2048 bit public and private keys are generated on server. Public key is sent to the targeted machines that is used for encrypting the documents using RSA algorithm. Practically, it is impossible to decrypt files if we don’t have the private key.
We advise users to keep a backup of important documents and files on reliable backup systems.
Regards,
Nice information,
what is way to recover original file after infection?.
Hi,
As we have discussed in the blog post, Cryptolocker uses asymmetric encryption algorithm where 2048 bit public and private keys are generated on server. Public key is sent to the targeted machines that is used for encrypting the documents using RSA algorithm. Practically, it is impossible to decrypt files if we don’t have the private key.
We advise users to keep a backup of important documents and files on reliable backup systems.
Regards,
Dear Sir,
We have the same issue as Divyesh faced. Only difference is we are not able to one any Word file.
Virus get remove and currently system are working fine except exiting all DOC file.
Kindly suggest.
Hi Manoj,
Kindly contact our support team at 0-927-22-33-000.
You can also raise a query at https://www.quickheal.com/submitticket.asp. Our support team will get back to you to resolve the issue you are facing.
Regards,
Dear Sir,
Nice information for cryptlocker and thanks for updating us….
PRABHUDAS
I have also faced same problem. cryptolocker has encrypted all my files. from above discussion it is clear that it is impossible to recover those, but fortunately if u got any solution to recover these files, please let me know.
Hi Arati,
We would recommend you to get in touch with our support team at 0-927-22-33-000. They will help you solve the issue.
Regards,
Thank you for your co-ordination .
Dear friend , Quick heal not found this virus, but Kaspersky effectivly found 6 virus and succeessfully removed, Quick people only telling pecautionary measure to backup, they are not telling How to remove this virus ……
Hi Vikas,
With the new feature called Advanced Behavior Based Detection system, Quick Heal 2014 can automatically remove CryptoLocker.
Our motive behind listing down precautionary measures is to help users remain on guard against the malware. We never know what sophisticated techniques CryptoLocker may use in the future. So, if we can prevent it from infecting our computers in the first place, we can significantly reduce the loss that the malware usually causes.
Regards,
Dear Sir,
Thanks for your information.It was gr8.But I would take this opportunity to flow my grievances against Quick Heal Technologies:This team is the last among the team of other antivirus companies to release the solutions for any virus infections.I had faced several instances where I was forced to have my patience tested.For Instance newfolder.exe virus,the above crypto virus.I had lost my clients due to the carelessness of this team. Today after waiting for 7 days these people gave me a mail :
“Thank you so much for the patience and understanding in this most regrettable situation.
We regret the inconvenience caused to you.
Decryption of encrypted files is not possible as of now,we request you to restore from backup.”
My client has lost all his data,he believed that he was being secured by Quick Heal Internet Security but Alas he was wrong. Today I lost one more client !
Hi Navratan,
We are sorry to hear about the troubles you had to undergo. We would like to inform you that malware such as CryptoLocker use sophisticated techniques to evade detection by security software. And once data gets encrypted by it, it cannot be recovered. However, keeping a backup is the best method to prevent data loss caused by the malware. Quick Heal 2014 has introduced the Advanced Behavior based Detection System that detects and blocks around 90% of Crypto-locker samples.
Regards,
how can i get backup of Private key??
Hi Ashish,
Are you referring to Quick Heal Desktop Products or Mobile Products?
For Desktop products, you can follow these steps to take a backup of the product license key:
1. Open Quick Heal
2. Click Help [top right corner]
3. Click About
4. Click ‘License Details’
5. Click ‘Print License Details’
For mobile products,
1. Open Quick Heal
2. From MENU, select Help
3. Select About
4. Select License Details
If you require any further assistance, kindly contact our support team at 0-927-22-33-000.
You can also raise a query at https://www.quickheal.com/submitticket.asp. Our support team will get back to you to resolve the issue you are facing.
Regards,
if the file is Already Corrupted then do you Know any Solution how we can get back all the Files & Data
Please Need your Help & Support
pooja Chavn
Hi Pooja,
This is a major cause for concern and you will need to contact our technical support team. They will be able to help you out with this issue. You can contact them in the following 2 ways:
1. You can call them on 0-927-22-33-000.
2. You can submit a ticket by visiting this link – https://www.quickheal.co.in/submitticket.
Best regards.
Cryptolocker again attacked , Do we have solution,
Though my customer was having Total Security with Updated Database?
Do we have solution????????????????
Hi Gopal,
May we request you to contact our technical support team. They will help you resolve this issue as soon as possible. You can reach them here – https://www.quickheal.co.in/submitticket.
Regards.