Shellshock Bug – How Does it Impact You?
A new security bug has been discovered recently, and it is as big, if not bigger, than the Heartbleed bug from a few months back. This security bug is called ‘Shellshock’ and it is found in a common program that runs on UNIX and Linux operating systems. The scope of this bug is pretty huge and now that attackers are aware of this, it could lead to severe security risks for many users. Not since Heartbleed have we seen such a security bug operate on such a large scale.
What is Shellshock all about?
Shellshock is a security vulnerability found in Bash. Bash is a command shell that is commonly used on Linux and UNIX operating systems and it has been around since 1989. Alarmingly, Shellshock has been around for more than 20 years now and it is yet unknown if it was accidentally developed by the creator. Just like Heartbleed, Shellshock seems to have been around for a long time and has been missed by several security audits.
What is Bash and how does Shellshock work within it?
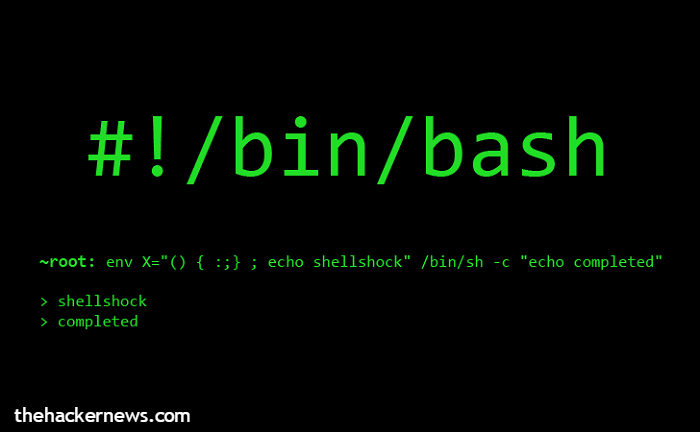
Shellshock is what is commonly termed as a Remote Code Execution (RCE) vulnerability within Bash. Just like we have the Command Prompt on Windows, Linux and UNIX have the command shell known as Bash. It helps the user run other programs within the system and Bash stands for “Bourne Again Shell”.
Using the Shellshock vulnerability, an attacker can affect machines using a technique known as command injection. Via this method, he can run a program on Bash without intimating the user and without logging on to the computer himself. Since Bash runs several programs in the background, all the attacker needs to do is ensure that his malicious text is not spotted. Harmless looking data contains malicious code that gets executed in this scenario.
Who is vulnerable to Shellshock?
Bash is commonly used in Apple’s OS X operating system. Additionally, it is also present in several web-servers and home appliances such as routers and other devices which face the Internet. This causes further trouble as updates for these devices are not easy to acquire or implement. As a result, Shellshock could potentially disrupt several services and homes.
With Heartbleed, an attacker could only steal data stored in the memory of systems. However, with Shellshock, he can gain complete access of the system. Hence the potential risk here is far greater.
Are Microsoft Windows users also vulnerable to Shellshock?
As of now, users of Apple Macs, Linux and UNIX based machines are vulnerable to Shellshock and the Bash vulnerability. Windows users are not directly vulnerable to the same. However, attackers are working on ways to utilize this weakness against Windows users as well. So it is highly recommended that Windows users keep their OS and security software completely updated at all times.
So what is the solution for Shellshock?
There are several programs and techniques that prevent command injection. However, the problem is that no one really knows what commands to look for as attackers can mask it well. Placing a few words of malicious code within thousands of lines is very easy, and pinpointing it is like finding a needle in a haystack.
The best solution here is for Bash to be updated by the people who use it. If there are any other vendor-specific updates available, they should be initiated as well.
UPDATE: It has been known that Macs use Bash as their default command shell. Hence they were at high risk. Apple has now pushed out updates that solve the Bash vulnerability in their systems. This update should be installed immediately from the following links:
OS X Lion
OS X Mountain Lion
OS X Mavericks
Moreover, we also recommend that Mac users install Quick Heal Total Security for Mac and keep this product updated for latest patches to guard against Shellshock.
10 Comments
So it is highly recommended that Windows users keep their OS and security software completely updated at all times.
So as per ur version pleaase confirm me whether I am safe…Yesterday u have updated Antivirus….
is android vulnerable
Hi,
No, Android is not vulnerable as of now.
Regards.
This is quite helpful. Thanks
From where or in which form, this virus come into my pc.
Hi Rahil,
This is not a virus as such. This is a vulnerability in the program mentioned, and this vulnerability can be used by a virus to enter the system.
Regards.
nice and thanks
Please Giv Me a sugesation that i have not compieted the update, again again faield.
Hi Atana,
Kindly contact our support team at 0-927-22-33-000.
You can also submit your query at https://www.quickheal.com/submitticket.asp. Our support team will get back to you to resolve the issue you are facing.
Regards,