One more phishing attack on Indian bank
After the holiday season is over and people resumed their office with new year work load ahead, it all started with phishing scam on one of the India’s popular nationalized bank. Since 8th January I had been observing that I had been receiving phishing emails targeting Punjab National Bank of India. The email looked as follows:
=======================
Subject: Important Notification From Punjab National Bank
Dear Valued Customer,
This is an official notification from Punjab National Bank . Your account access has been limited due to a login attempt failure.
To restore your account we have attached a form to this email.Please download the form and follow the instructions on your screen.
NOTE: The form needs to be opened in a modern, javascript enabled, browser (ex: Internet Explorer 8, Firefox 3, Safari 3,Opera 9).
We are continually improving our Web site to better serve you. Be sure to check back with us often as we add exciting new services to meet your financial needs.
If you have questions or need assistance, our customer service team is here to help.
Thank you for using Punjab National Bank !
===========================================
There were lot of signs that indicated it was a spam email for targeted phishing attack. One can see that this specific message was sent to “undisclosed-recipients” and starts with “Dear Valued Customer,”. I knew it was a spam as they have not addressed the email to me even though they have my complete details.
The message is short and OK, and the link it refers the receiver to isn’t going to a bank domain at all, it points to:
hxtxtxpx:x/x/x7xsearch.com/scripts/search/click.aspx?t=p&qu=204.249.69.25/in d.htm&a=0 &s=sb&r=1&du=http%3a%2f%2f2x04.249.69.25/ind.htm&cu=http%3 a%2f%2f204.249. 69.25/ind .htm
which further takes the browser automatically to:
htt p: // 2x0x4.249.69.25 / ind.htm (this is US based server)
and further redirection happens automatically to:
https://x6x1.181.83.65 /ind /pnbindia / index.php (this is China based server)
On this server the fake PNB phishing website is hosted. The phishing site looks identical to the original website, only the link is different. Here is a sample screenshot:
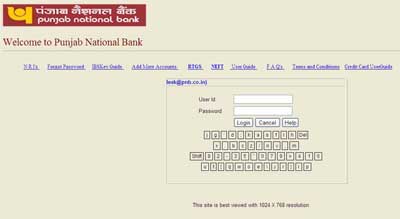
Quick Heal Anti-Phishing plug-in is protecting users from visiting this fraudulent website. We are keeping watch on the new modifications to this on going threat. On 9th Jan we received around 6 such emails with various message in email. On 10th we did not received any message as I guess the hacker/attacker took weekly off on Sunday. On 11th Jan we again received 12 mails of PNB phishing attack. Today its 12th Jan and we have received 5 more emails of this phishing fraud. During all these days the attacker has been changing the redirection server that redirects users to his phishing website as the older pages are being deleted on the web server by the ISP.
More details as it appears..
No Comments, Be The First!