New ICICI Bank phishing scam
Phishing, an attempt to steal banking details, is a serious problem faced by banks worldwide. Commonly, a phishing attempt appears as an e-mail that comes from a known institution like a bank or a popular online shopping website. I recently came across such an email which pretends to be from ICICI bank. The email looks like this:
The email misguides Internet users by saying – “ICICI Bank is constantly striving to provide you with more convenience, control, and security to assist in managing your finances online. As part of our ongoing efforts to operate on ISO requirements, and create an enhanced security portal for your online banking services, we have upgraded the ICICI Bank Electronic-Sign Consent and Online Access. To upgrade your account security status it is mandatory that you kindly update your online banking Information. Do kindly update and unlock your ICICI Bank Online profile by following the steps”.
The mail then creates a sense of urgency by mentioning that the account will be suspended if the user does not undergodo the upgrade process within 72 hours.
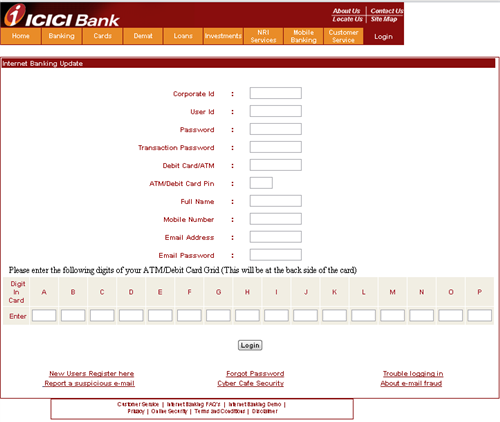
The email also contains an HTML file attachment which the attacker aims to execute on the victim’s machine. Upon execution, it looks like an exact replica of the ICICI Internet banking form with fields like user ID, password, debit card no., pin no., mobile no. and more.
This HTML file contains a malicious unescape ( ); function in JavaScript. Attackers often use Unescape when they hack and insert links. After decoding the script we found that the attacker gathers all the information and submits it to the following link:
“hxxp:// accountauthenticate. com/www.icicibank.com.verification.process.platform.validation.process.
evaluate.login.username.correct.qualification.enter.send.verify.complete.information.database.center.align.justify.
align.synchronise.clickhere.virtual.keyboard/BankAway/delete.gif.php”
Quick Heal successfully detects this attack and protects its users from such phishing attempts. Please note that banks never ask for confidential data like login and transaction password, One Time Password (OTP), Unique Reference No. (URN) etc. through emails.


8 Comments
Thanks for this information. I always Trust Quick Heal for Protection.
Thanks for keeping us updated. Quick Heal is great in terms of trustworthiness. Looking forward to similar updates in the future.
Thanks for the information and taking corrective action. Hope you find solution to other phishing attacks as well.
Great job by Quick Heal, At large we can benefit with this great efforts of quickheal by sharing this info with your near and dear
Thanks for the information.
@Kamal, @Sanjay, @CR Jayawant, @Shivkumar, @Sameer: Thank you for the appreciation. Quick Heal will continue to provide you with trustworthy protection.
Thank you very much for timely warning in such an important matter. Please keep it-up…
Thanks for the information sir.