Mailto Ransomware under the skin of explorer.exe

All of us, at some point in time, must have heard the story of Wolf and the flock of sheep. The fooling trick used by the wicked wolf of pretending to be a sheep is still in use by many malware authors. They pretend to be genuine processes to achieve their villainy activities.
Such a case has been recently observed in Mailto ransomware wherein it is making use of legitimate windows process known as ‘explorer.exe’.
Now, how are hackers doing this?
The closest answer is, process code injection!
That is correct, but this time the technique used for injection is not very common.
The Mailto or Netwalker performs process hollowing in explorer.exe. This helps in evading the Anti-Virus software (AVs) to easily perform the encryption.
In process hollowing, usually, the target process is created in suspended mode and the injection is carried out. But here the process is not created in suspended mode— rather it uses the ‘Debug’ mode.
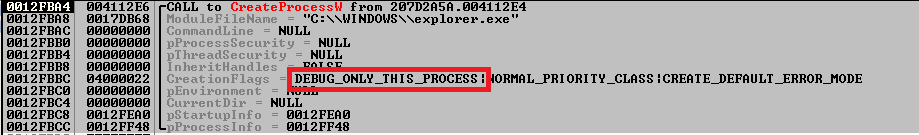
Fig.1: Mailto Creates the Process in Debug mode
To perform further injection activity, it gets the process and thread details using debug APIs like WaitForDebugEvent.
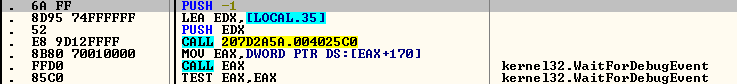
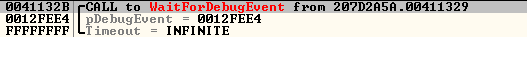
Fig.2: API to get the process and thread details
Then, a section is created with a size similar to that of the sample using ZwCreateSection and its view is mapped in the current process using ZwMapViewOfSection.
In this view, the sample file is copied, and manual relocation is performed.
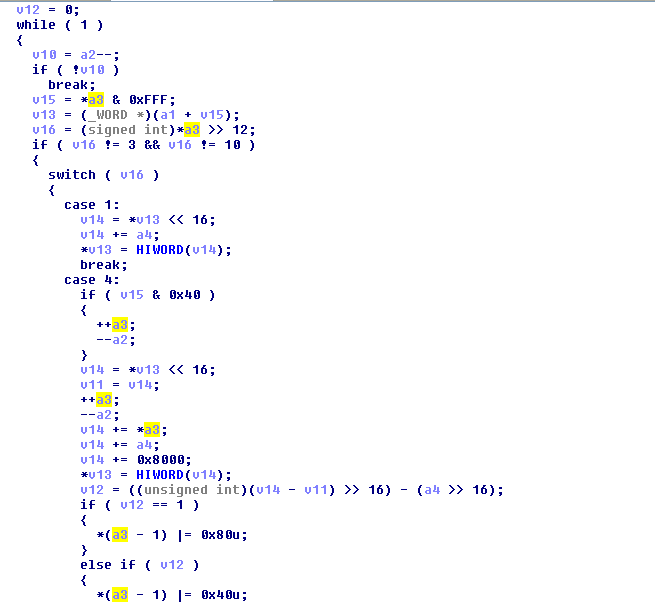
Fig.3: Relocation of Hardcoded addresses
The view of this section is then unmapped using ZwUnmapViewOfSection. The thread context of the process created (explorer.exe) is retrieved and changes are made, setting the start address of the thread from where the execution is intended to begin.
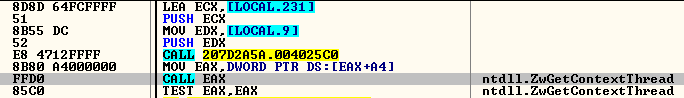
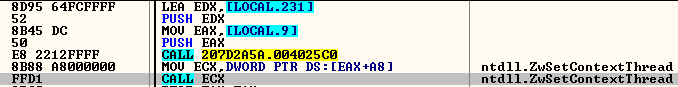
Fig.4: Setting the Start address of injected code
Finally, call to ContinueDebugEvent and DebugActiveProcessStop makes the execution of the thread ‘start’ that will be responsible for the encryption of the files. The process tree is shown in the below image.
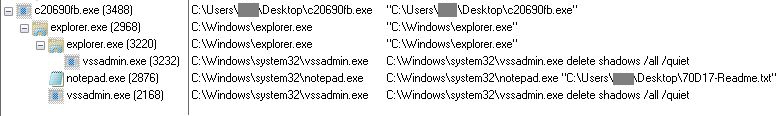
Fig.5: Process Tree
When we decrypt the encrypted data present in the .rsrc section, we get all the important information present in JSON format. This information contains base64 encrypted ransom note, e-mail addresses used in the ransom note, processes that need to be killed if in execution, whitelisted paths, file names and extensions, etc.
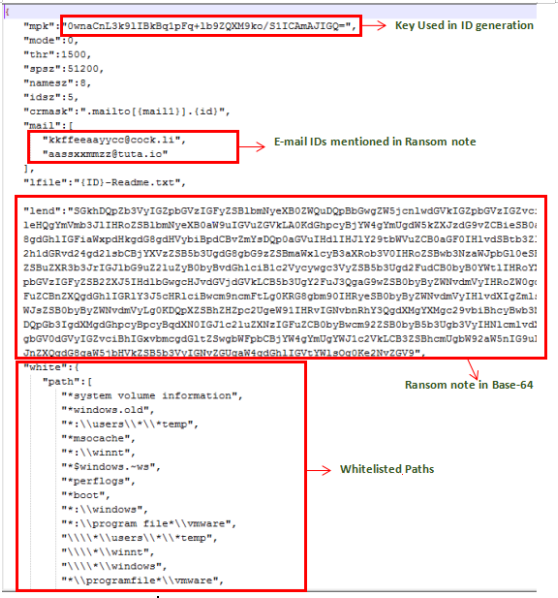
Fig.6: Decrypted data
Injected explorer.exe Activity
After injection, the malware (i.e. injected explorer.exe) drops its copy at ‘%ProgramFiles%\<8 Alphanumeric characters>\<8 Alphanumeric characters>.exe’ and sets the RUN entry for its persistence.
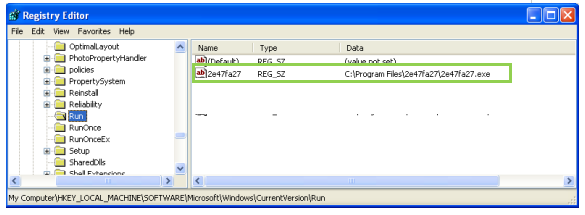
Fig.7: RUN Entry
Further, it deletes the shadow copies of the system using the command:
‘%system32%\vssadmin.exe delete shadows /all /quiet’
ID Generation
The ID is the extension that will be used for newly encrypted files and as the name of ransom note file. It is generated using the key kept under the tag ‘mpk’ in decrypted JSON, the retrieved computer name and the hardware profile information about the machine being infected (through GetCurrentHwProfileW Windows API).
SHA-256 of these components is calculated and the first five characters of the output are used as the new extension of encrypted files. Its first eight characters are used as the name of the directory and as the filename when the self-copy is dropped at ‘%ProgramFiles%’.
SHA-256 Output:
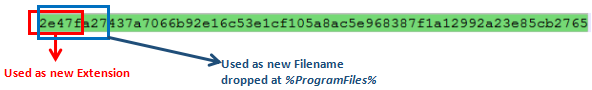
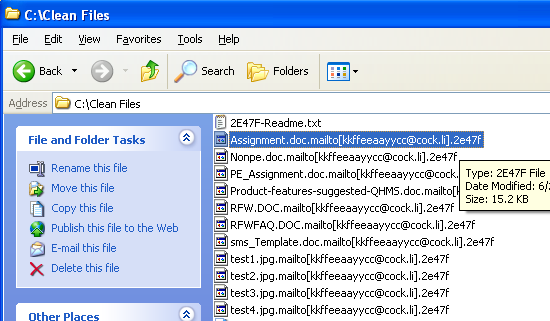
Fig.8: Encrypted Files with Extension generated above
The files are encrypted with SALSA20 algorithm and the filename is appended with ‘.mailto[<mail-id>].<ID generated above(I.e extension)>’.
After encryption, the ‘explorer.exe’ kills the parent process and deletes the original sample, the file dropped at %ProgramFiles% and also the RUN entry, eradicating the traces of its existence.
The Infection Vector is not clear as yet , but most likely the attacker may have used spam mails for propagation.
A ransom note is dropped with the name ‘<ID>-Readme.txt’ containing the ransom payment details on every encrypted location.
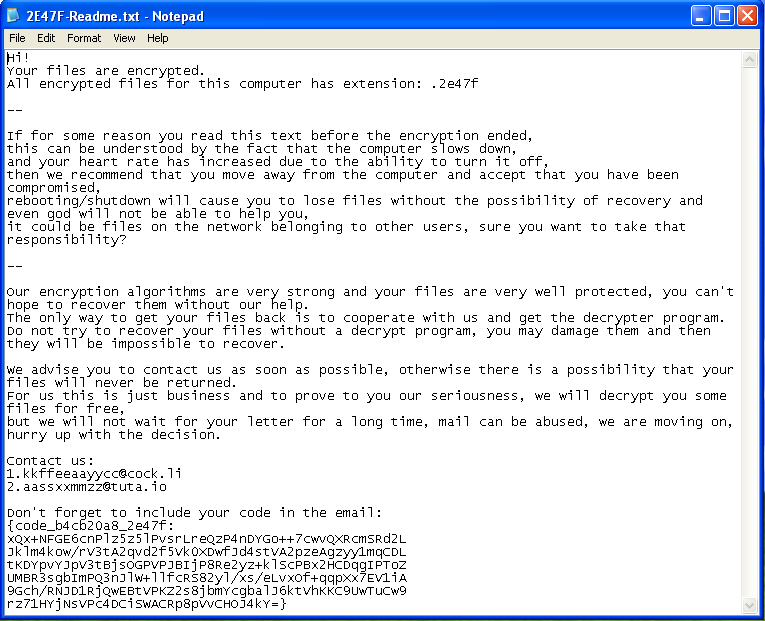
Fig.9: Ransom Note
Conclusion
Several old stories educate us to be aware of roguery intentions of those whom we trust easily —one should take care and should not completely trust the processes that appear to be legitimate that ultimately might help malware to bypass security products.
Here, the injection through process hollowing is done in explorer.exe which itself makes it very difficult to make its presence perceptible. Moreover, while creating the process for injection, instead of using a suspended mode, it is using the not so commonly used ‘Debug’ mode. This makes AV prevention techniques to fail.
How Quick Heal protects its users from the Mailto Ransomware?
Quick Heal successfully blocks Mailto ransomware with the following protection layers:
- Virus Protection
- Behavior Detection
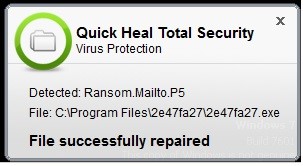
Fig.10: Virus Protection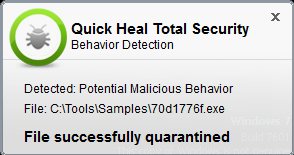
Fig.11: Behavior Detection
IOCs:
207D2A5AA3A00B8C908B6CFFCF6DDED8
3D6203DF53FCAA16D71ADD5F47BDD060
775F5027ABC97C0EC8E9202A4ED4CC14
B0008E752F488D7E97A8D2452411527E
73DE5BABF166F28DC81D6C2FAA369379
D7D7F3C95D03367C61BCFDFE4E7AB47A
Subject Matter Expert:
Priyanka Shinde, Umar Khan | Quick Heal Security Labs

No Comments, Be The First!