Is your Remote Desktop System safe from Brute Force Attacks?

As we have explained in the previous Troldesh ransomware blog post, cyber criminals are now spreading ransomware by gaining access to computers through Remote Desktop. Remote access to the victim’s computer is gained by using brute-force techniques which can effectively crack weak passwords.
Typically, the attacker scans a list of IP ranges for RDP port 3389 (default RDP port) which are open for connection. Once an attacker finds a port, they launch the brute-force attack. The brute-force technique uses a trial and error password guessing attack with a list of commonly used credentials, dictionary words, and other combinations. There are several tools available on the Internet that performs the above Port scanning and RDP brute forcing with ease.
Once the access is gained, criminals simply disable the system’s antivirus and run the payload. This means, even if the antivirus is updated and has a detection against the malware, turning off its protection renders the system defenseless.
However, Quick Heal Firewall feature can effectively prevent such unauthorized access by configuring it to allow only trusted IP addresses from accessing the system via Remote Desktop.
Configuring Firewall:
First, we need to create a rule to block RDP connections from any incoming systems. Then we create an exception rule to allow only specific systems from being able to bypass the first rule and access the systems RDP.
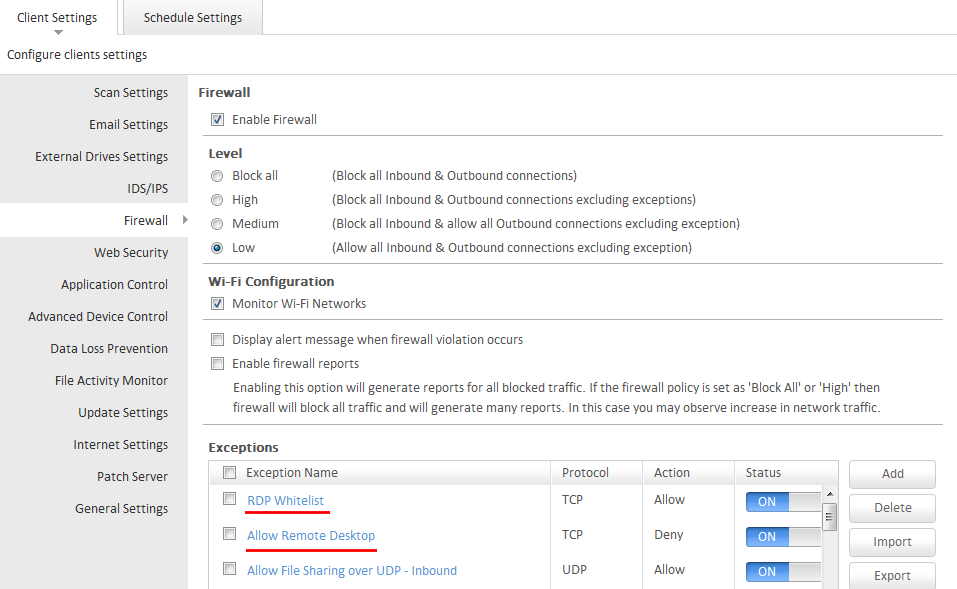
For Seqrite EPS Products:
Login to the EPS Console => Select Settings Tab => Firewall.
Note: These settings will be applicable to all clients under the default policy.
For other Groups created, the configuration should be made on its respective policy.
For Quick Heal Standalone Products:
Open Quick Heal Dashboard => Select Internet and Network => Firewall Protection=> Advanced Settings – Configure=> Traffic Rules.
1) To block all RDP connections:
- Scroll down and double click on the Allow Remote Desktop rule.
- Click on Next till you reach the last window i.e Select Action
- Here change the action from Allow to Deny and click on Finish.
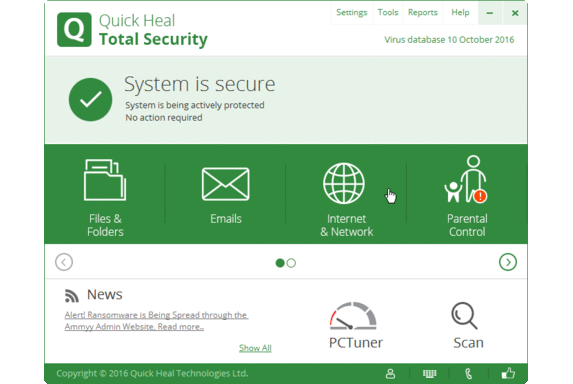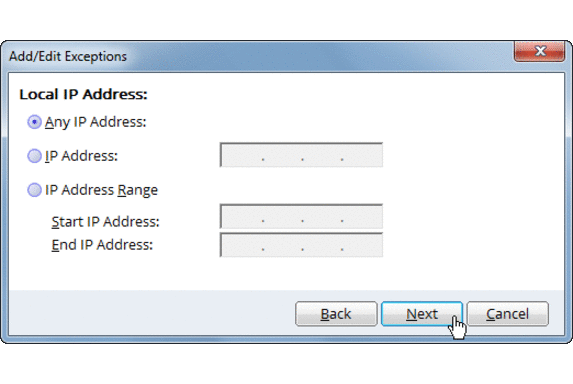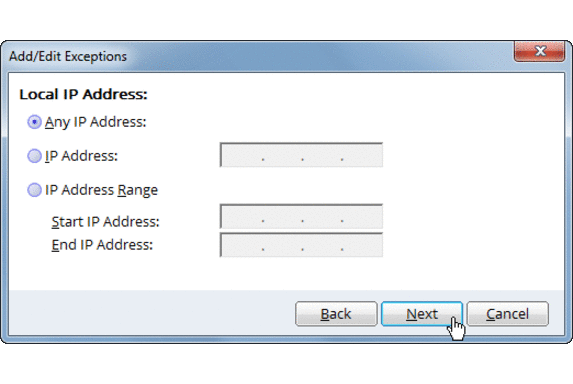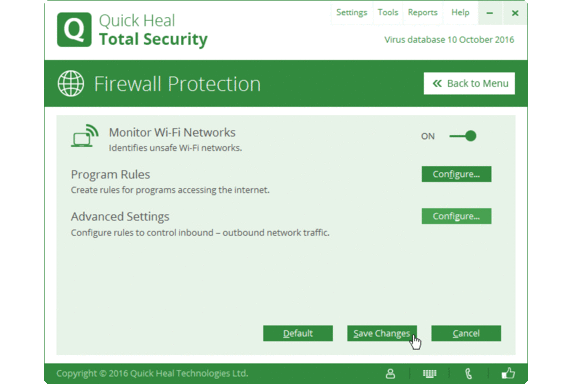
2) To add exception for trusted systems:
- In the Traffic rule window, click on Add for adding an exception.
- Give any Name for the rule eg. RDP White-list and select Next twice.
- In the Local TCP/UDP Port window enter the RDP port in the Specific port option and click Next. By default the RDP port is 3389.
- In the Remote IP Address enter the IP address of the system from which you would want to accept RDP connections.
- You can also enter an IP range to allow RDP connections from multiple systems of the specified range. Eg. 192.168.0.1 to 192.168.0.255.
- Select Next for the Remote TCP/UDP port window.
- Select an action to be taken as ‘Allow’ in the last window and click finish.
Now save the changes made by clicking on OK and selecting Save Changes.
Note: Make sure that the RDP White-list rule is higher than the Allow Remote Desktop rule in the Firewall rule list.
Other Security practices to help avoid RDP brute forcing attacks.
– Use strong and unique passwords on user accounts that cannot be easily breached. Weak passwords like Admin, admin@123, user, 123456, password, Pass@123, etc., can be easily brute-forced in the first few attempts itself.
– Configure password protection for your security software. This would prevent any unauthorized users accessing the system from disabling or uninstalling it. Quick Heal users can enable this feature from the Settings => Password Protection.
– Disable the Administrator account and use a different account name for administrative activities. Most brute-force attempts are done on an Administrator user account as it is present by default. Also, remove any other unused or guest accounts if configured on the system.
– Change the default RDP port from the default‘3389’. Most attacks of such type focus on targeting the port 3389 of RDP.
– Enable Network Level Authentication (NLA) feature in your RDP settings available in Windows Vista and later OS.
Ref: https://technet.microsoft.com/en-us/library/cc732713.aspx
– Configuring Account Lockout Policies that automatically lock the account after a specific number of failed attempts. This feature is available in Windows and the threshold can be customized as per the administrator.
Ref: https://technet.microsoft.com/en-us/library/dd277400.aspx
43 Comments
Thank you.
thank you
THANK YOU
how i can buy my product key
Hi Anubhav,
You can buy a Product Key (or a license) from our website – http://www.quickheal.com/home-users
Regards,
i like
very good
thankyou
OFLINE UPDATE KAISE KARNA HOGA .PLEASE BAL DIGIYA.
Hi,
Please click here – https://www.quickheal.co.in/quick-heal-antivirus-updates-download/
Regards,
We have quickheal antivirus server edition 2013
updated till date. There are no such iption which you have mentioned.
Kindly suggest the process for older verions
Hi Vivel,
Thank you for writing in. Our support engineers would gladly help you with this issue. Please call us on our toll-free no. 1800-121-7377 or visit https://bit.ly/QHChat to chat with us online. You can also raise a ticket at https://bit.ly/Askus and we will get back to you at the earliest.
Regards,
Virus Detectted Scan
THANKS
i like verymuch
Let me know whether I have select inbound and outbound both option to add RDP Whitelist or not
Hi Suman,
Thank you for writing in. Our support engineers would gladly help you with this issue. Please call us on our toll-free no. 1800-121-7377 or visit https://bit.ly/QHChat to chat with us online. You can also raise a ticket at https://bit.ly/Askus and we will get back to you at the earliest.
Regards,
Thankyou Quickheal for make my pc safe….
It is abest antivirus for pc
very nice way to update pc
I think the default settings of QH for “Allow Remote Desktop” should have been “DENY” and not “ALLOW” as is the case now. I feel the reason for this is that most users do not need Remote Desktop and most users certainly are not of such settings. If at all any user attempts to use Remote Desktop, QH may issue suitable notification that Remote Desktop setting needs to be changed to allow any such authorised entry.
I am sorry about the typo in my post: My post should have read “most users certainly are not aware of such settings”, instead of “most users certainly are not of such settings”.
its too good
GOOD
Since a long time I was facing the biggest issue and now it is solved..For the same I lost belief in the product but thank you..I wish you will post more solutions which are mostly unanswerable by most EXPERTS(as they are called)..Thanks a ton..
thank u
thanks for better services and anti wires protection.
I have your paid antivirus software. Somehow all the data and installed program erased and again after formate i have installed it now.
Hi,
Thank you for writing in. Our support engineers would gladly help you with this issue. Please call us on our toll-free no. 1800-121-7377 or visit https://bit.ly/QHChat to chat with us online. You can also raise a ticket at https://bit.ly/Askus and we will get back to you at the earliest.
Regards,
I got this Quick Heal from a software shop with code. after installation I was try to update it but refused to be up to date
Hi,
Thank you for writing in. Our support engineers would gladly help you with this issue. Please visit https://bit.ly/QHChat to chat with us online. You can also raise a ticket at https://bit.ly/Askus and we will get back to you at the earliest.
Regards,
Team Quick Heal
sir when we opening some sites getting some problems please rectify
Hi Tejasree,
Thank you for writing in. Our support engineers would gladly help you with this issue. Please visit https://bit.ly/QHChat to chat with us online. You can also raise a ticket at https://bit.ly/Askus and we will get back to you at the earliest.
Regards,
Team Quick Heal
How to change the listening port for Remote Desktop
1.] Open the registry editor by typing the “regedit” command
2.] Search for this registry subkey:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\TerminalServer\WinStations\RDP-Tcp\PortNumber
3.] Double-click or right-click on the “PortNumber” registry subkey, select the decimal base and type the port number of your choice (the default port is 3389, in this example, we selected port 3390). Click on “Ok” to save your selection.
4.] Restart the computer.
Thank you for sharing this information.
my computer do not work proper and there is more virus in my computer
Hi Rahul,
Thank you for writing in. Our support engineers would gladly help you with this issue. Please call us on our toll-free no. 1800-121-7377 or visit https://bit.ly/QHChat to chat with us online. You can also raise a ticket at https://bit.ly/Askus and we will get back to you at the earliest.
Regards,
protection out of dated i regularly update but sim bole quick heal is red
Hi,
Thank you for writing in. Our support engineers would gladly help you with this issue. Please call us on our toll-free no. 1800-121-7377 or visit https://bit.ly/QHChat to chat with us online. You can also raise a ticket at https://bit.ly/Askus and we will get back to you at the earliest.
Regards,
Team Quick Heal
some unknown virus has entered my laptop and is slowing down or l. not alllowing normal work, please do the needfu
Hi,
Thank you for writing in. Our support engineers would gladly help you with this issue. Please visit https://bit.ly/QHChat to chat with us online. You can also raise a ticket at https://bit.ly/Askus and we will get back to you at the earliest.
Regards,
Team Quick Heal
My pc is Very Problem in very slow speed in work
Hi,
Thank you for writing in. Our support engineers would gladly help you with this issue. Please visit https://bit.ly/QHChat to chat with us online. You can also raise a ticket at https://bit.ly/Askus and we will get back to you at the earliest.
Regards,
Team Quick Heal