FAQs on SSL certificates and their importance
While browsing the web a user frequently comes across several pages where a secure channel of communication is required. This is especially true since many attackers have staged phishing attacks and stolen confidential information over the years. Pages that involve financial transactions, login details and other data are hence secured with the help of SSL (Secure Sockets Layer) and TLS (Transport Layer Security) certification.
These certificates were first created by Netscape in 1993 for Internet communication security. It prevents eavesdropping and tampering from a third party and thus helps avoid MITM (man-in-the-middle) attacks. It is most commonly used while web browsing, checking email, instant faxing, instant messaging and VoIP activities.
How to spot a SSL certificate?
In order to spot this certification on a page one needs to locate a padlock symbol on the address bar (or at the bottom right corner) and the text “HTTPS” before the URL. This presence signifies that SSL certification is present and that the page where one shares data is authentic and secure.
This implies that the communication between the client and the server is encrypted and also that interference from third-parties is impossible. Thus a malicious party cannot intercept the transaction, steal data or forge replicas of the webpage without the certificate.
How does a SSL certificate work?
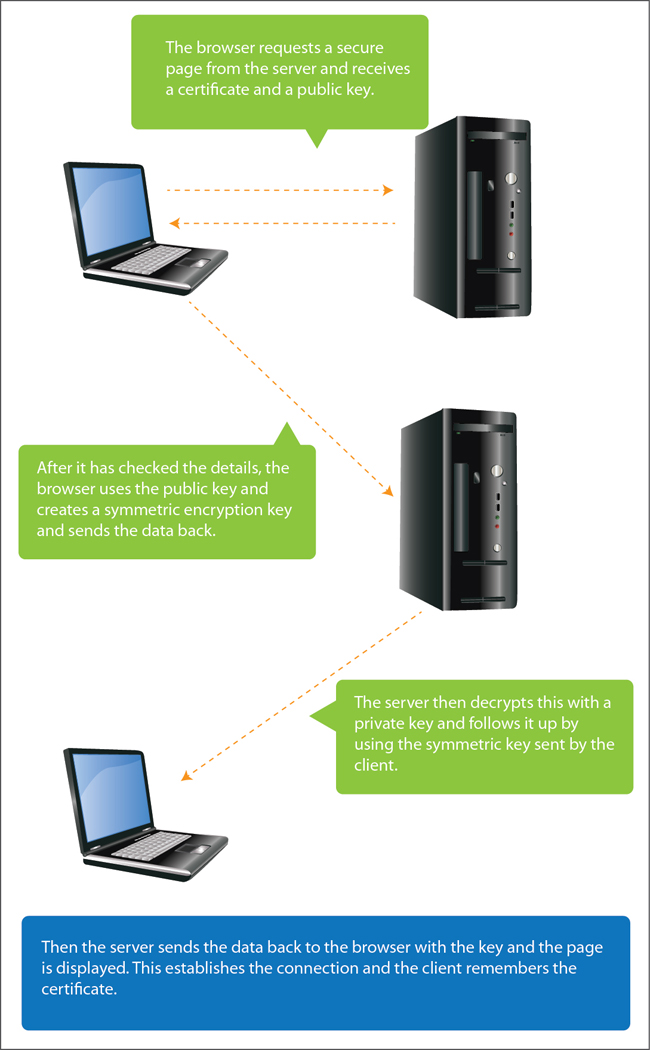
SSL effectively adds a security layer between a browser and a server. Popular servers like Gmail and Facebook (and others) have signed certificates that are already present on an end user’s machine. The absence of a signed certificate leads to an “untrusted certificate” error arising. A secure communication (known as a handshake) is established between a client and a server before the following steps take place:
What are the different kinds of keys?
The server possesses two keys (public key1 and private key2) to access the data. The public key is shared with a client but the private key is retained. The code that is encrypted with the public key can only be decrypted with the private key and this ensures authenticity. Hence these keys are used in pairs and form a symmetric algorithm.
The client also has a symmetric algorithm. So it uses the public key sent by the server and then sends its own public key back to the server. This is not a very complicated procedure and is carried out to discourage phishers and attackers.
Who issues a SSL certificate?
SSL/TLS certificates are issued by a Certificate Authority (CA) who identifies both parties of a transaction. There are about 50 CA’s currently in operation and some of the popular ones are VeriSign, GoDaddy, Comodo, Geotrust etc. A CA ensures that a ‘root certificate’3 has validating information, server details, a public key and also a hash to prevent tampering and rogue certificates.
Login data and debit/credit card details should never be entered in a page that has an invalid SSL certificate. An invalid SSL certificate is a clear sign that the page has been compromised and it is the easiest way to spot fake phishing websites. Quick Heal’s Web Security protects users from threats transferred through malicious websites. It scans all accessed webpages for fraudulent activity and provides protection against phishing attacks and gives zero-time protection from infected websites and malwares.
- Public key – First part of a symmetric cryptographic system and is used to encrypt plain text. This is available to all parties.
- Private key – Second part of the symmetric cryptographic system and is used to decrypt ciphered text. This is only available to the sender.
- Root certificate – Either an unsigned public key certificate or a self-signed certificate that identifies the Certificate Authority of a webpage.

2 Comments
Thanks rahul,
Really the blog is fantastic and liked it very much although i was knowing SSL and all but the way it is putted is really appreciable and last terms explained summarizes it “THE BEST”