Fake Coronavirus tracking app exploiting our fear and vulnerable social situation

As the Coronavirus spreads across countries creating fear across the globe, everybody wants to stay on top of any information related to it wanting to remain safe and away from infected people. Malware authors are also taking advantage of this situation. Previously on the Android Playstore, there were many applications present which claimed that they could provide Coronavirus tracking information. But Google has set up some rules for these types of applications and have considered these under the ‘Sensitive events’ category. According to policies from this rule, Google proactively removed many applications from Playstore to stop malware authors to take advantage of this situation.
But malware authors have used another way to enter into the user’s phone. They are using their sites to publish malicious apps developed by hackers themselves. There is a website named ‘coronavirusapp[.]site’ —on this website, an Android application is hosted which claims to get real-time info about Coronavirus patients. The application claims that it will give notification to the user if a Coronavirus patient is present in the vicinity.

Fig. 1 – Site snapshot
But in reality, this app is ransomware —it locks the user’s android device and asks for a ransom.
Technical Analysis of the App:
After launch, this application asks to ignore battery optimization so it can run in the background.
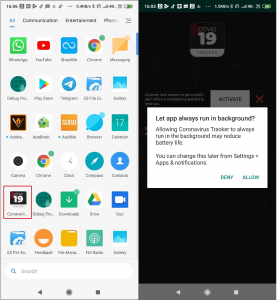
Fig. 2 – Asking for Battery optimization
After getting this permission it starts its malicious activity where it asks for accessibility permission —accessibility was introduced in Android to assist physically impaired users. Accessibility service has access to sensitive information such as the information about running applications on the phone. Attackers can misuse this data. The App’s next step is to ask for device admin permission. Device administrator enabled app can enforce security policies, password policies being one of them. Malware authors can use this permission to take control of the device.

Fig. 3 – Activities asking for device admin permission and accessibility
After granting permissions, when the user clicks on ‘scan area for coronavirus’, the app calls upon the onhideapp() method which further checkmarks all required permissions. If all permissions are given by the user, it hides its icon from the application drawer.
![]()
Fig. 4 – Code to hide the application icon
How does this malware lock the phone? 
Fig. 5 – Phone locking flow
Below are the events which occur to lock User’s device:
A) Due to accessibility permission malware can get all accessibility events. In the above code snippet (block 1) we can see it checks accessibility events type. If this type is TYPE_WINDOW_CONTENT_CHANGED (Constant Value: 2048) Or TYPE_WINDOW_STATE_CHANGED (Constant Value: 32) it calls upon the method Onblocker().
B) In this method it creates a new thread (code snippet block 2) in which it calls method startblockedactivity(), which starts BlockedAppactivity. Before calling this it checks various conditions such as, if the app is hidden from the app drawer (code snippet block 3).
C) Then BlockedAppactivity is started. In oncreate it sets contentview to blocked app which is the ransomware note (code snippet block 4).
Thus, whenever the user tries to open any app this activity opens not allowing the user to use the intended app.
Below is a snapshot of ransomware note activity. where the malware author asks for 250 $ ransom. There is another variant of the app in which ransom amount is 100 $. There is a button ‘Web designius’. —when a user clicks on this button it redirects to Pastebin page where malware author has given instructions to unlock the phone.
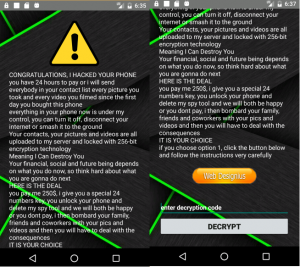
Fig. 6 – a variant of coronavirus tracker ransomware with 250 $ ransom note
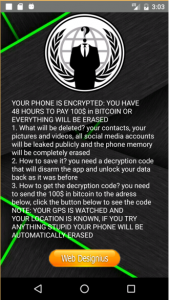
Fig. 7 – a variant of coronavirus tracker ransomware with 100 $ ransom note
Malware author has written pin verification code in the same activity. The BlockedAppactivity has a function named verifyPin() which checks input code to hardcoded key ‘4865083501’. By entering this key user can unlock his phone.
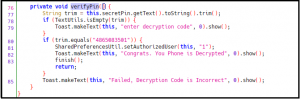
Fig. 8 – Pin verification code
There are many sites which are offering Coronavirus tracking maps and Coronavirus related information, many of these sites ask users to install Android applications to get more info. We have analyzed one of the sites which claims to give good info but in reality, is a ransomware app. Users should not fall prey to these types of apps and sites. If they want information for their safety, they can visit the official WHO website.
Application name :
Coronavirus tracker
Detection:
Quick Heal Mobile Security detects these apps under detection Android.Locker.O
IOC:
69a6b43b5f63030938c578eec05993eb
D1d417235616e4a05096319bb4875f57
How to stay safe –
1. Check an app’s description before you download it.
2. Check the app developer’s name and their website.If the name sounds strange or odd, you have all the reasons to suspect it.
3. Go through the reviews and ratings of the app. But, note that these can also be faked.
4. Avoid downloading apps from third-party app stores.
5. Use a reliable mobile antivirus (like Quick Heal Total Security), that can prevent fake and malicious apps from getting installed on your phone.


No Comments, Be The First!