Cyber Crimes against India – Increasing in Leaps and Bounds
Reportedly, India happens to be the 4th most favorite target of cyber criminals when it comes to phishing attacks. This fact is vouched by the number of cyber attacks hitting the country, which has scaled exponentially in 2013.
Here are some findings by the Indian Computer Emergency Response Team (CERT-In)
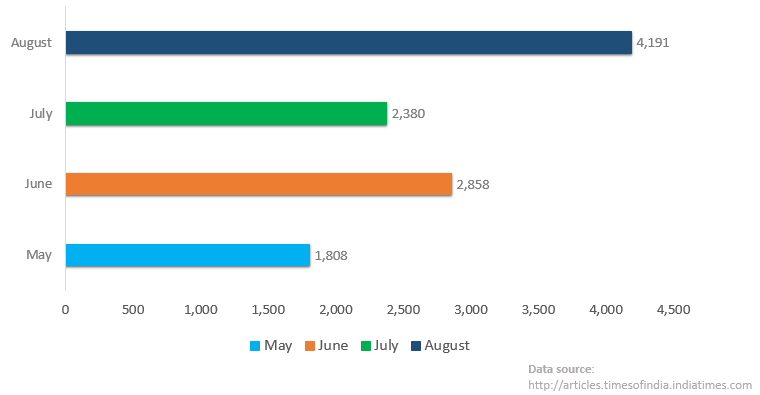
Number of Indian Websites defaced and hacked in 2013:
August – 4,191
July – 2,380
June – 2,858
May – 1,808
Most of these compromised Websites belong to the .in domain, whose servers are located in India.
List of Offenders
Some of the main cyber crooks that India is dealing with presently are:
- SA3D HaCk3D
- h4x0r HuSsY
- SanFour2S
- BD GREY HAT HACKERS
- Suwario
- SpyDy
- hasnain haxor
- CouCouM
Agenda behind the Cyber Attacks
These cyber attacks that have been happening are aimed towards:
- Stealing passwords
- Attacking data-driven applications
- Launching man-in-the-middle attacks
- Web shell loading
What is being done to contain the situation?
If we are to believe what the National Security Council Secretariat (NSCS) has to say, then the situation is grim. The Indian Cabinet did initiate a cyber security architecture, but it did not prove to be promising; it showed very little progress. But Indian does have a roadmap where bodies such as the National Technical Research Organisation and defence and home ministries will play intertwined role in the nation’s cyber protection. And this pyramid will be head by CERT-In, as the overlooker.
More Expectations from Homegrown Security Solutions
The government has expressed its interest in deploying homegrown security software rather than foraging for software developed elsewhere.
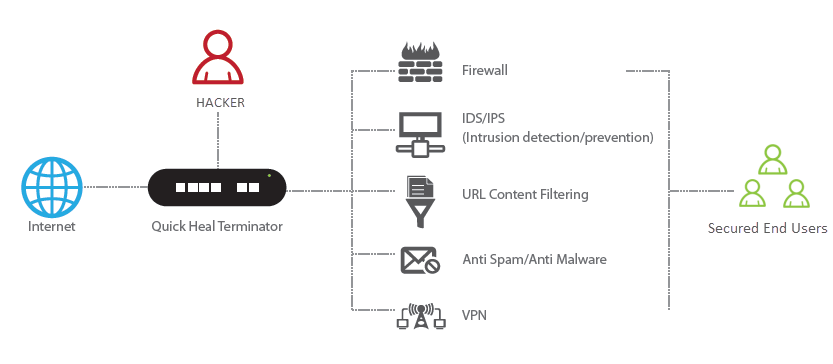
In the wake of the increasing cyber attacks in the country, and given the government’s interest in indigenous software, Quick Heal strives to stand out in the crowd. Its Unified Threat Management solution christened Terminator has all that is required to counter such threats. This software has been developed with the aim to make the IT infrastructure of an enterprise stable, secure, and productive.
You can download Terminator’s Data Sheet to get an in-depth analysis on its features and how they work to protect enterprise network.
Data source:
articles.timesofindia.indiatimes.com

1 Comment
Thank you Rajib sir for this helpful info.
Regards,
Hrushi