From the last one year, Quick Heal Security Labs has been observing a boost in the number of…
Security
Cryptocurrency miner hits IoT devices, mostly affects Brazil and Russia!
According to a blogpost published on Aug 1, 2018, 200,000 routers in Brazil were compromised to deliver Cryptocurrency…
Beware of the Armage Ransomware – the File Destroyer!
In July last week, Quick Heal Security Labs detected a new ransomware called Armage. It appends ‘.Armage’ extension…
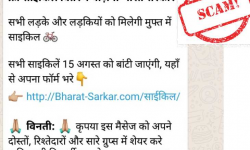
Beware of the ‘Free Cycle Distribution Yojana’ WhatsApp message. It’s fake!
As India’s Independence Day (15th of August) approaches, messages about free distribution schemes are doing the rounds on…
The evolution of a 4-year-old-threat Emotet: From an infamous Trojan to a complex threat distributer
Emotet malware campaign has been existing for a long time. It comes frequently in intervals with different techniques…
Your copy-paste habit can cost you your money
How often do you store your important data in files? It’s very common, right? This data may be…
Cryptojacking is When Someone Illegally Uses Your PC to Make Digital Money & 8 Facts
What attracts more than a magnet? You might have guessed it right – it is money! And where…
CVE-2018-5002 – Adobe Flash Player Stack Buffer Overflow Vulnerability Alert!
The recent zero-day vulnerability CVE-2018-5002 in Adobe Flash Player enables attackers to perform a Remote Code Execution on…
Cryptocurrency mining rampage throttles Linux machines – an analysis by Quick Heal Security Labs
Quick Heal Security Labs recently came across a Linux-based Monero (XMR) miner. Monero (XMR) is one of the…
An analysis of the Dharma ransomware outbreak by Quick Heal Security Labs
On April 25, 2018, Quick Heal Security Labs issued an advisory on a new ransomware outbreak. We are…