Bladabindi Malware Abusing Pastebin.com as Infection Vector

Earlier, malware authors kept their payloads on Command and Control (C&C) servers or compromised websites. And to do this, they had to setup their C&C server or compromise a genuine website. But now, they don’t need to bother about such things, as they have started using genuine file sharing sites like “Pastebin.com” which allows user to store malware in plain-text. Pastebin.com is a well-known website where users can store plain text.
While analyzing malware samples, we found that the malware is downloading the “Base64” encoded text from pastebin.com. On decoding this Base64 data, we received an executable file which is the main payload of the malware. Most of these executables are from “Bladabindi” family.
The downloader enters into the user’s computer using various techniques like spam emails and social engineering. In this report, we will see how pastebin.com is misused with analysis of one malware sample.
Analysis of Bladabindi (MD5: 0C34D70FF9DD1BA3B7BFE9F4FBA8F010)
The file is an Auto-it installer. On execution, it drops two executable files at “C:\Documents and Settings\[user]\Local Settings” and executes the same. The dropped files are as follows:
- TempWinToFlash.exe: Genuine tool used to create bootable USB with any Windows Setup from a DVD/ISO
- TempWindows.exe: Copies itself in “%temp%” as system.exe and executes it. Now this system.exe downloads Base64 encoded file from “pastebin.com\download.php?i=pejXu40a” decodes it and injects the decoded executable in self-process. Thereafter, all activities are carried out by this downloaded file.
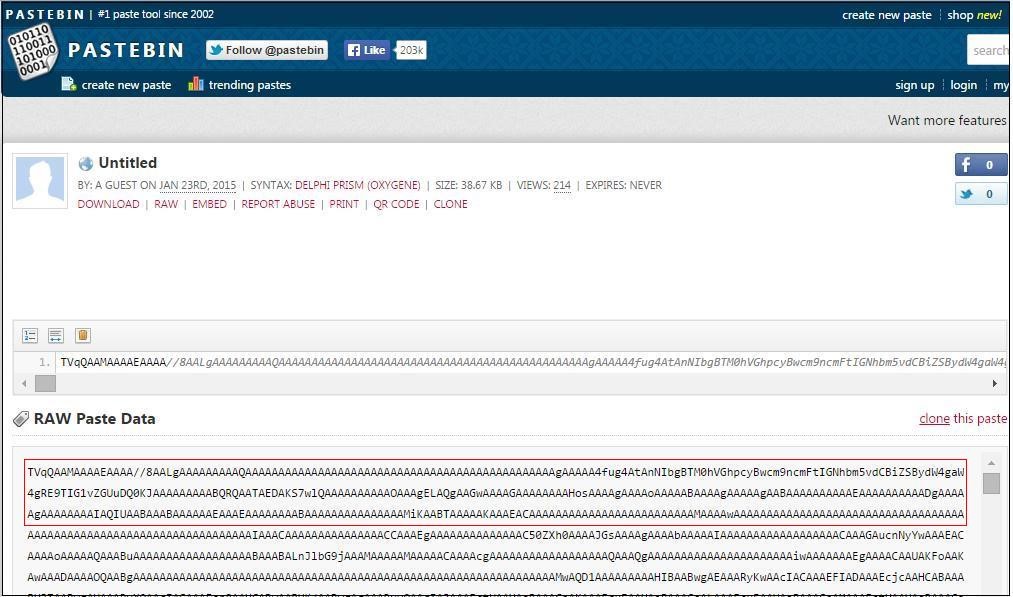
This Base64 Encoded file on Pastebin.com looks like the below figure 1.
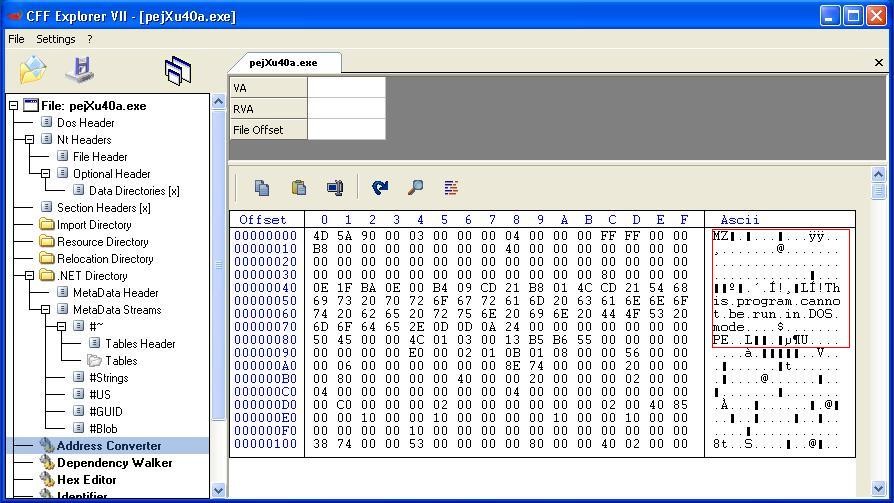
After Base64 decode it is .Net file as below.
Activity of Main_Component.exe (In memory component)
This component is developed using Microsoft Visual Basic.Net.
Auto-run
It copies system.exe in “Startup” folder as 12ce4e06a81e8d54fd01d9b762f1b1bb.exe
Registry changes for Auto-run
It adds the following auto-run registry entry:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\
12ce4e06a81e8 d54fd01d9b762f1b1bb: “%temp%\system.exe”
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\
12ce4e06a81e8d54fd01d9b762f1b1bb : “%temp%\system.exe”
Other Registry Changes
It also adds the following registry entry:
HKEY_CURRENT_USER\Environment\SEE_MASK_NOZONECHECKS = 1
Further it saves downloaded Base64 encoded data in registry such as:
HKEY_CURRENT_USER\Software\12ce4e06a81e8d54fd01d9b762f1b1bb\f8c065f4e758233f0d12dc9b8cf7a2ce = [Base64_Encoded_Main_Payload]
Bypass Firewall:
It executes the following command to bypass Firewall:
netsh firewall add allowedprogram [Path_Of_system.exe] ENABLE
Main Activity
This backdoor gathers the following data and sends it to C&C server:
- Computer name
- User name
- OS version
- Date of installation
It provides the following RAT functionalities to the attacker:
- Keylogging
- Capturing screenshots
- Bypassing Firewall
- Process Management: start new process or kill any process
- Registry Management: get or set registry key/value
- Provides remote shell access to the attacker
- Downloading and executing files
- Updating current RAT
- Compressing files for uploading
- Deleting self-copies
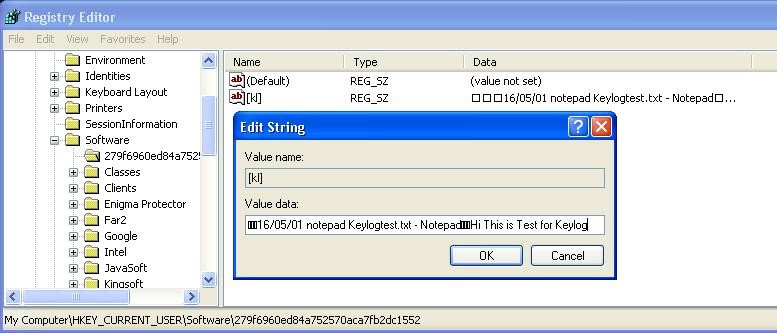
The main payload of the virus saves all keystrokes in the registry as shown in figure 3.
Encryption and decryption
The malware sends all data in Base64 encoded format. Except files are uploaded after ZIP compression.
The backdoor supports following commands:
| “CAP” | Take screen shot and send it to C&C. |
| “kl” | Sends key logged data in Base64 encoded format. |
| “rn” | Download and execute file. |
| “un” + “~” | Bypass firewall by using
“netsh firewall delete allowedprogram \””. |
| “un” + “!” | End current application. |
| “un” + “@” | Start new process and end current application. |
| “Up” | Update RAT downloads new file and replace it with current. |
| rss | Remote shell |
| inf | Send information of installed malware component like:
Installed volumes serial number, Auto run Registry Key, Exe Process with path, etc. |
| RG + “~” | List all registry sub-keys and values of specified registry key |
| RG + “!” | Set Registry value as specified key |
| RG + “@” | Delete value for specified Registry key |
| RG + “#” | Create Sub-Key for specified key |
| RG + “$” | Delete sub-key tree for specified registry key |
Tricks used by the malware to avoid detection and cleaning
- Critical process
It makes itself as a critical process to prevent it from being stopped. The infected system may crash with a stop code 0x000000F4 if the malware process is interrupted. This can make it difficult to clean the computer when the malware is running.
- Registry resident non executable payload
Downloaded file is never saved on the disk, but it gets saved in the registry. The next time the system is booted, the downloaded file is read from the registry and decoded; the decoded executable is then injected into the system.exe process.
- Bypass automated analysis or make analysis difficult
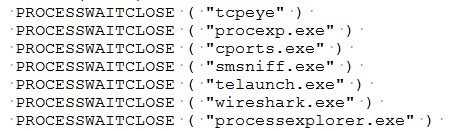
The first component mentioned above (0C34D70FF9DD1BA3B7BFE9F4FBA8F010) is an auto-it installer. The Auto-It script contains the following code:
Due to this code, it will not show any malicious activity when any one of these monitoring tools is running. This enables the malware to bypass automated analysis. It also makes it difficult for analysts to manually analyze the sample.
Statistics about the “pastebin.com”
The main payload is stored in Base64 encoded format. We have found more than 100 Base64 encoded files on “pastebin.com”. Almost all of these files are malicious. Interestingly, 90% of them belong to the same malware family i.e., Bladabindi. The Bladabindi samples have been listed below:
| File Name | MD5(After Base64 Decryption) | Date Uploaded | No. of Downloads |
| maYGSJCE.txt | d6970b1ecb80a3d547e8f4e02cee5398 | 24-Jan-16 | 1288 |
| 6A2bWaLW.txt | 3bbcf3bd1da31a9db42016c4df579efe | 7-Feb-16 | 46 |
| etyinjbb.txt | e52e16c23ae389045ce8f3016baf2917 | 9-Feb-16 | 60 |
| ypi89T1N.txt | 50bdce08a13587a9163d2e3e15038b3c | 11-Feb-16 | 96 |
| Kc063FLa.txt | 0ca6c92280ca9f6c0d6f3de565102789 | 13-Feb-16 | 90 |
| r73g5ZcQ.txt | 6cafb49af51a081dfabea417ddf63382 | 15-Feb-16 | 17 |
| 4vkGXgMm.txt | 0332726731694abcc3859ab31d910178 | 19-Feb-16 | 46 |
| 4UNdJehk.cs | 777252b978e8fded255d87dd4e141865 | 25-Feb-16 | 49 |
| g4TpnaQx.txt | 291b7a2bccc2cd132a3a7ada301687ca | 25-Feb-16 | 50 |
| YyVDCPGF.txt | e52c69649019a84e4f00616b029c4813 | 29-Feb-16 | 46 |
| G4pyW8Nd.cs | 6926608e7cf967597ab16a8e615a1295 | 1-Mar-16 | 48 |
| PnTq9Tzu.txt | 8c3906072e1767ce83fde2dcfb4ae5a0 | 4-Mar-16 | 41 |
| sN33WjEs.txt | c38f4c069940318236f265df4bf50369 | 6-Mar-16 | 43 |
| 7kmFXuv2.txt | 8fc065c4e26c3088f4ee510d679fcb50 | 6-Mar-16 | 45 |
| qgW3iaZd.txt | e00d4bc57c9613d78b89c6175fa5c422 | 6-Mar-16 | 55 |
| tNyvK9La.txt | 5c6365694e219baaa93c964265a99d8e | 10-Mar-16 | 46 |
| QmYfNwMe.txt | cbaebc74b7991028d8b0deb7a7feef5b | 13-Mar-16 | 46 |
| w8pR9Kx7.txt | 54a00dce2b6150b991d69d72aa20f88f | 27-Mar-16 | 61 |
| WPveSANA.txt | dd7971459d2f2436a2d7ded062560ebe | 28-Mar-16 | 54 |
| vbFuaG8B.txt | e1d6994007b77db2137b3c37211da641 | 28-Mar-16 | 42 |
| jKjxmp3H.txt | 011b816123c586362ff84c40c5367e5f | 28-Mar-16 | 47 |
| JL0AhHvt.txt | cfdd43745ada1e35e0d54a1c03372fc5 | 28-Mar-16 | 42 |
| J7yDkhG4.cs | 37087fb23720f2d153d5d93ff5ac2b02 | 28-Mar-16 | 47 |
| FWy2Bwze.txt | f712efdecf834da398a68ceb2b1066bc | 28-Mar-16 | 50 |
| d7b36SCq.txt | b6029da18724abd87efbab6942cf2ad | 28-Mar-16 | 50 |
| b2S1QH7b.txt | 4befc92ce3d59e7f91c29d967cb2e51 | 28-Mar-16 | 47 |
| wWUCRtUn.txt | 7B75861CCF60960CB7A4510F62DCC759 | 3-Aug-15 | 204 |
| X9qT2gdv.txt | B6E3214B8571667E9E6C8D949143A409 | 2-Aug-15 | 203 |
| pMFr9T7Z.txt | 95175B900A661E6517466ECDBB11F8EC | 2-Aug-15 | 182 |
| WSm8bhnD.txt | 38C833ED93ECCB73EA652749AB5FF6D2 | 2-Aug-15 | 189 |
| q6TcsD93.txt | A7DE2A7A3E88EC73A6E5DDDAF1EBFEF4 | 1-Aug-15 | 211 |
| 5c4Gkx4s.txt | 1DA67EB93E87C84F538D7070EB9EF946 | 1-Aug-15 | 229 |
| gmePj6As.txt | B31E511502634C47067B2247D487AE52 | 30-Jul-15 | 170 |
| B0YtjY5d.txt | 0C9F01C2417B8E45C51E29A544B5D8FE | 30-Jul-15 | 212 |
| SDfnfN22.txt | 467DEE8AC854B9294D818900847EC986 | 30-Jul-15 | 182 |
| UCNZ6vAT.txt | D46A18E03CA59BD1F9925C70D3C537C1 | 29-Jul-15 | 192 |
| bJWCCZcH.txt | 712B9273724AFE942B52D31593EBC020 | 28-Jul-15 | 192 |
| ziN2uncg.txt | C4481C61E8FC87627E74B9E86DFA5984 | 22-Jul-15 | 195 |
| zy7aQ0XC.txt | 959E924082E4F6B12CFC802FD0E5E2CB | 14-Jul-15 | 156 |
| dcQbqCHN.txt | E50FD6BC5E6969AA3D10C34ED9EAC0BB | 22-Jul-15 | 189 |
| 8y93ZV9w.txt | 80E4F2BD93CFAD05C27D82DB52A67173 | 2-Jul-15 | 233 |
| hcYBCaqP.txt | CEA83249D6DD7E0DA1233AA694A241A4 | 27-Jul-15 | 209 |
| J9HkHtEQ.txt | 0CAD1A373392EB6C494F8B1991E45978 | 24-Jul-15 | 195 |
| ympQ7j6V.txt | 9F6BD8384EF226AC45AEF44D6DB54391 | 14-Jul-15 | 178 |
| ynbvfred.txt | 1642873BBEF7D991DF11539E16CA6000 | 29-Jul-15 | 217 |
| ZwCAc7A4.txt | 6C30D822F38114E6D2B68BD7A7618568 | 15-Jun-15 | 219 |
| KCyVSNK1.txt | 800388926C83A71121562308FDC1B105 | 23-Apr-15 | 191 |
| 7GC1AXmv.txt | 2B155E4268482A8CEE87CA27E400C803 | 19-Mar-15 | 211 |
| Ym7e4iDh.txt | F15353C8FD5EA57C02417A8921DCBD5B | 27-Mar-15 | 218 |
| KPuZ5NQX.txt | 487C285566533C4CFC9AF6A3814CBB3B | 23-Jan-15 | 215 |
| kjipFGzz.txt | 652302915BDE357879A8594E62E32808 | 13-Oct-14 | 220 |
| TOTAL | 7564 |
Quick Heal Detection
| Component Name/Description | MD5 | Quick Heal Detection Name |
| Random_Name.exe | 0C34D70FF9DD1BA3B7BFE9F4FBA8F010 | TrojanDownldr.Bladabindi.BS64 |
| TempWindows.exe | EBB8BC149C8D7FFBAFD8D232BDD9D796 | TrojanDownldr.Bladabindi.BS64 |
| Main Payload | 959E924082E4F6B12CFC802FD0E5E2CB | Backdoor.Bladabindi.AL3 |
Conclusion
Malware authors are abusing “pastebin.com” for spreading different malware families. As per our analysis among all these families, “Bladabindi” RAT is spreading rapidly. More than 7500 users have been infected via pastebin.com since 2015. As the main payload is never stored on the disk, it is difficult to detect such malware.
Acknowledgment
Subject Matter Experts
- Prakash Galande
- Sagar Daundkar
– Threat Research & Response Team
No Comments, Be The First!